|
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
Cryptocurrency News Articles
Internet Computer Protocol (ICP) Introduces Verified Credentials (VCs) to Prevent Bot Manipulation of Social Media
Jun 19, 2024 at 01:12 am
Internet Computer Protocol (ICP), a decentralized blockchain network that extends the functionality of Web3 by overcoming the limitations of traditional blockchains and smart contracts, has introduced Verified Credentials (VCs), a walletless solution that enables efficient and trustworthy and sharing of personal data while maintaining privacy and control.

Internet Computer Protocol (ICP), a Layer 1 blockchain that extends the functionality of Web3, has introduced Verified Credentials (VCs), a walletless solution that enables efficient and trustworthy sharing of personal data while maintaining privacy and control.
VCs were officially unveiled at the Digital Identity unConference Europe (DICE) 2024 in Zurich, Switzerland. They also bring with them the first application designed to prevent the manipulation of public discourse on social media by eliminating the problem of bots and fake accounts, a crucial mission given that nearly half the global population is set to vote in national elections in 2024.
Today, for most users, their wallets such as Metamask, work as their universal Web3 identity. With VCs, ICP offers a walletless infrastructure and tooling to issue, share, and consume credentials in a privacy-preserving fashion.
VCs, described in ICP’s latest Roadmap as one of the key focus areas, are built on top of the Internet Identity (II), a decentralized identity solution running end-to-end on the Internet Computer blockchain. Internet Identity provides a robust authentication solution based on passkeys rather than passwords or seed phrases. Passkeys are built on a standardized technology that offers protection against phishing attacks. This makes Internet Identity both more convenient and secure than traditional sign-in methods.
Verifiable credentials are digital representations of data (qualifications, achievements, or attributes) that are cryptographically secured and portable. A VC is a digital version of a physical credential that the holder can quickly share online with service providers needing to verify a claim, such as age or humanity. The VC is tied to a user through a digital identity provider like Internet Identity.
“The new Verifiable Credentials feature of Internet Identity addresses long standing problems for online privacy-preserving authentication: all a user needs is a computing device that has a passkey (all recent ones do) and a browser,” said Jan Camenisch, CTO of the DFINITY Foundation. “Apart from dApps on the Internet Computer, traditional systems can also plug in with Internet Identity and allow users to authenticate with Verifiable Credentials, e.g., proving that they are a real person, that they did KYC, or that they are over 18.”
Until now, users authenticating with Internet Identity to a dApp were assigned a unique and pseudonymous identifier for each dApp without any additional attributes such as name, age, or residency. The Verified Credentials framework allows users to assign identity attributes to their Internet Identity.
The user can easily manage and reuse the credential without dApps being able to tie it back to them. VCs put users in control of who they share their credentials with and how much information they want to divulge. For instance, a user can verify their age without revealing their name or date of birth, a feature called selective disclosure.
When end-users authenticate to an application, Internet Identity creates their unique identifier for that service. This way, different applications cannot track users as they explore the web.
Moreover, the Verified Credentials framework solves the problem of dApp interoperability in a privacy-preserving fashion. Internet Identity (II) acts as the trusted intermediary between a Relying Party and an Issuer, using an alias to share credentials instead of the user’s real principal.
Proof of Unique Humanity (PoUH)
One of the first applications of Verified Credentials in the ICP ecosystem is the Proof of Unique Humanity (PoUH), implemented by the decentralized on-chain messaging app OpenChat and developed by Decide AI. The identity issuer links a credential to biometric data such as facial, finger or palm print recognition, requiring users to prove that they are human and possess only one account on a platform.
Users anonymously using multiple accounts and bots has long been considered an issue that not only contributes to the amount of illicit behavior conducted online, but also underpins the level of toxic discourse prevalent on traditional social media platforms.
A report published at the end of 2023 by Queensland University of Technology showed that the spread of disinformation by bots is getting worse. Researchers identified a network of 1,200 automated X (formerly Twitter) accounts promoting the conspiracy theory that Trump beat current President Joe Biden in the 2020 election, which attracted over three million impressions. They also discovered a separate network of 1,300 accounts broken into clusters circulating pro-Trump messages, including misleading news items.
Proof of Unique Humanity (PoUH) will help combat the activity of bots and foster more virtuous discourse on social media. The problem with the existing Proof of humanity is that it is easy to manipulate. Users or bots can solve all sorts of proof of humanity tests and do it a hundred times over to get a hundred accounts.
On the other hand, Proof of Unique Humanity (PoUH) prevents people from piloting multiple online accounts by linking a credential to the biometric data. It eliminates the risk of a user creating hundreds of social media accounts, or taking advantage of token farming or air
Disclaimer:info@kdj.com
The information provided is not trading advice. kdj.com does not assume any responsibility for any investments made based on the information provided in this article. Cryptocurrencies are highly volatile and it is highly recommended that you invest with caution after thorough research!
If you believe that the content used on this website infringes your copyright, please contact us immediately (info@kdj.com) and we will delete it promptly.
-

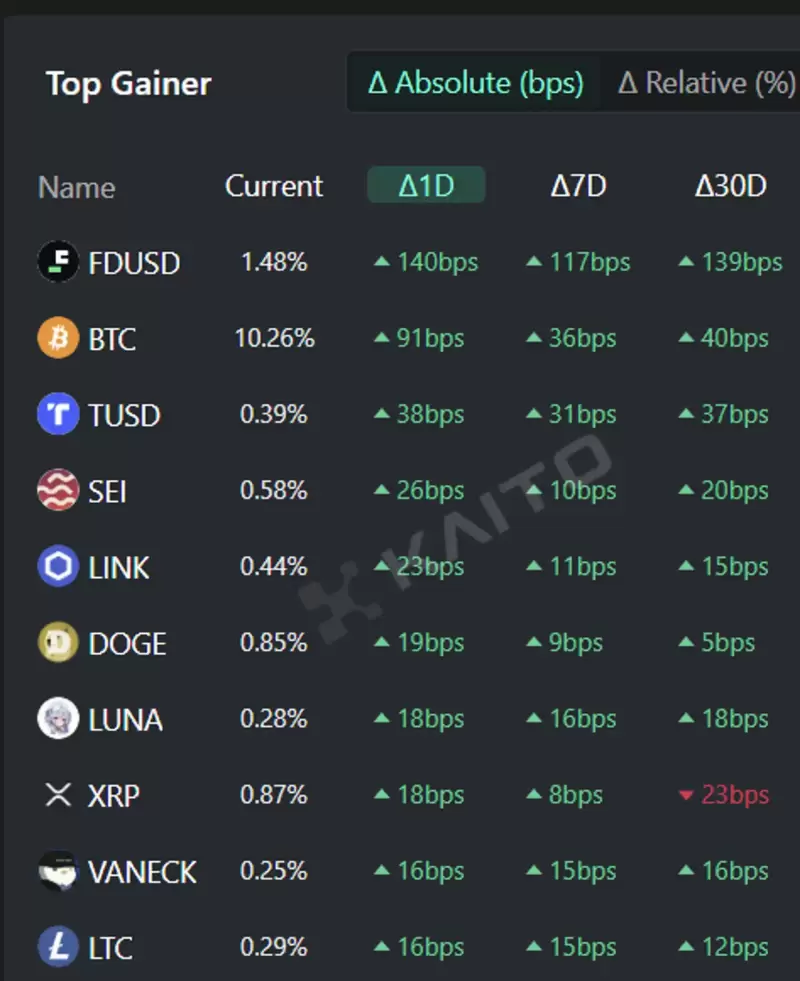
- FDUSD, BTC, TUSD, SEI, and LINK are the top 5 virtual asset-related keywords attracting the most interest
- Apr 03, 2025 at 03:45 pm
- According to the Token Mindshare (a metric quantifying the influence of specific tokens in the virtual asset market) top gainers from the AI-based Web3 search platform Kaito
-

-

-

-

-

- Meme Cryptocurrency Dogecoin DOGE/USD Falls After President Donald Trump's Tariff Shock, Extending Weekly Losses to Over 16%
- Apr 03, 2025 at 03:35 pm
- Popular dog-themed cryptocurrency Dogecoin DOGE/USD fell Wednesday after President Donald Trump's tariff shock, extending its weekly losses to over 16%.
-

-

-