
|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|
用于数据发现和治理的 OpenMetadata 平台已受到严重漏洞的影响,使攻击者能够绕过身份验证并在 Kubernetes 工作负载上执行远程代码执行 (RCE)。这些漏洞允许未经授权的访问和加密货币挖掘活动。微软已敦促用户应用 OpenMetadata 更新并加强身份验证措施,以减少潜在的利用。

Critical Vulnerabilities in OpenMetadata Platform Pose Severe Threat to Kubernetes Workloads: Urgent Mitigation Required
OpenMetadata 平台中的关键漏洞对 Kubernetes 工作负载构成严重威胁:需要紧急缓解
[Redmond, Washington] - February 28, 2023
[华盛顿州雷德蒙德] - 2023 年 2 月 28 日
Cybersecurity researchers from Microsoft have uncovered a series of critical vulnerabilities in the OpenMetadata platform that empower threat actors to exploit Kubernetes workloads for clandestine crypto mining activities. These vulnerabilities have the potential to compromise enterprise environments and disrupt critical business operations.
Microsoft 的网络安全研究人员发现了 OpenMetadata 平台中的一系列严重漏洞,这些漏洞使威胁行为者能够利用 Kubernetes 工作负载进行秘密加密货币挖掘活动。这些漏洞有可能危害企业环境并扰乱关键业务运营。
The Microsoft security blog has issued a stark warning, revealing that five significant vulnerabilities allow attackers to bypass authentication and execute Remote Code Execution (RCE) on affected Kubernetes workloads. These vulnerabilities, designated as CVE-2024-28255, CVE-2024-28847, CVE-2024-28253, CVE-2024-28848, and CVE-2024-28254, affect OpenMetadata versions preceding 1.3.1.
微软安全博客发布了严厉警告,揭示了五个重大漏洞,允许攻击者绕过身份验证并在受影响的 Kubernetes 工作负载上执行远程代码执行(RCE)。这些漏洞(指定为 CVE-2024-28255、CVE-2024-28847、CVE-2024-28253、CVE-2024-28848 和 CVE-2024-28254)影响 1.3.1 之前的 OpenMetadata 版本。
Understanding the Vulnerabilities
了解漏洞
CVE-2024-28255, rated 9.8 on the Common Vulnerability Scoring System (CVSS), exploits a flaw in the API authentication mechanism of OpenMetadata. By exploiting this vulnerability, attackers can bypass authentication and gain unauthorized access to sensitive endpoints.
CVE-2024-28255 在通用漏洞评分系统 (CVSS) 上的评级为 9.8,利用了 OpenMetadata 的 API 身份验证机制中的缺陷。通过利用此漏洞,攻击者可以绕过身份验证并获得对敏感端点的未经授权的访问。
CVE-2024-28255, assigned a CVSS score of 9.4, stems from deficiencies in JWT token validation within the JwtFilter component. This vulnerability allows attackers to send a malicious PUT request to modify system policies, potentially leading to remote code execution.
CVE-2024-28255 的 CVSS 评分为 9.4,源于 JwtFilter 组件内 JWT 令牌验证的缺陷。该漏洞允许攻击者发送恶意 PUT 请求来修改系统策略,从而可能导致远程代码执行。
Exploitation Modus Operandi
开发操作模式
Security analysts have observed a systematic attack sequence involving the exploitation of these vulnerabilities:
安全分析师观察到涉及利用这些漏洞的系统攻击序列:
- Vulnerability Identification and Exploitation: Attackers target vulnerable versions of OpenMetadata and exploit the vulnerabilities to gain initial code execution within the container hosting the compromised image.
- Intrusion Validation and Connectivity Establishment: Post-infiltration, attackers validate their intrusion through ping requests to specific domains linked to Interactsh, a popular tool for attacker communication.
- Crypto-Mining Malware Deployment: Once successful access is established, attackers download crypto-mining malware from a remote server and execute it with elevated permissions. The server hosting the malware has been traced to China.
Mitigation Measures
漏洞识别和利用:攻击者以 OpenMetadata 的易受攻击版本为目标,并利用这些漏洞在托管受感染映像的容器内获得初始代码执行。入侵验证和连接建立:渗透后,攻击者通过对链接到的特定域发出 ping 请求来验证其入侵。 Interactsh,一种流行的攻击者通信工具。加密挖掘恶意软件部署:一旦成功建立访问,攻击者就会从远程服务器下载加密挖掘恶意软件并以提升的权限执行它。托管该恶意软件的服务器已被追踪到中国。 缓解措施
To mitigate these threats and protect OpenMetadata workloads, organizations are strongly advised to implement the following measures:
为了减轻这些威胁并保护 OpenMetadata 工作负载,强烈建议组织实施以下措施:
- Update to OpenMetadata 1.3.1 or Later: Update the image version of Kubernetes clusters running OpenMetadata to the latest version, specifically 1.3.1 or newer, to patch these vulnerabilities.
- Strong Authentication: Employ robust authentication mechanisms for accessing OpenMetadata over the Internet. Avoid using default credentials and consider implementing multi-factor authentication.
- Network Segmentation: Restrict access to OpenMetadata workloads from untrusted networks to reduce the attack surface.
- Regular Security Audits: Conduct regular security audits to scan for vulnerabilities and misconfigurations that could expose OpenMetadata to attacks.
- Incident Response Plan: Establish an incident response plan to promptly detect and mitigate potential security breaches.
Organizations using OpenMetadata are urged to prioritize these mitigation measures to prevent exploitation of these critical vulnerabilities and protect their Kubernetes workloads from malicious crypto mining activities.
更新到 OpenMetadata 1.3.1 或更高版本:将运行 OpenMetadata 的 Kubernetes 集群的镜像版本更新到最新版本,特别是 1.3.1 或更高版本,以修补这些漏洞。 强身份验证:采用强大的身份验证机制通过 Internet 访问 OpenMetadata。避免使用默认凭据并考虑实施多重身份验证。网络分段:限制来自不受信任的网络对 OpenMetadata 工作负载的访问,以减少攻击面。定期安全审核:定期进行安全审核,以扫描可能使 OpenMetadata 遭受攻击的漏洞和错误配置。事件响应计划:建立事件响应计划,以及时检测和缓解潜在的安全漏洞。敦促使用 OpenMetadata 的组织优先考虑这些缓解措施,以防止这些关键漏洞被利用,并保护其 Kubernetes 工作负载免受恶意加密挖掘活动的影响。
免责声明:info@kdj.com
The information provided is not trading advice. kdj.com does not assume any responsibility for any investments made based on the information provided in this article. Cryptocurrencies are highly volatile and it is highly recommended that you invest with caution after thorough research!
If you believe that the content used on this website infringes your copyright, please contact us immediately (info@kdj.com) and we will delete it promptly.
-
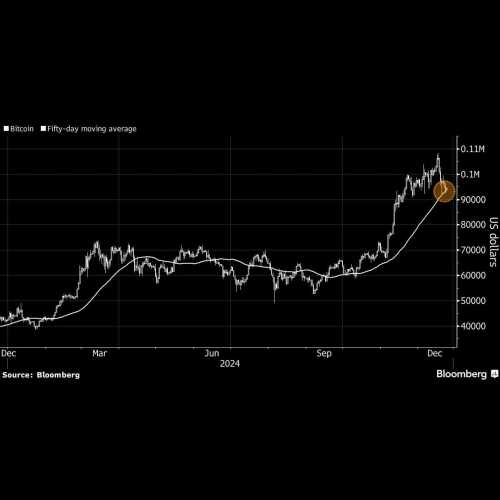
- 随着投机热情降温,比特币跌破 50 天移动平均线
- 2024-12-24 10:55:02
- (彭博社)——比特币在破纪录的一年的最后一段时间里表现疲软。周二早些时候,该数字资产在亚洲以约 94,500 美元易手
-
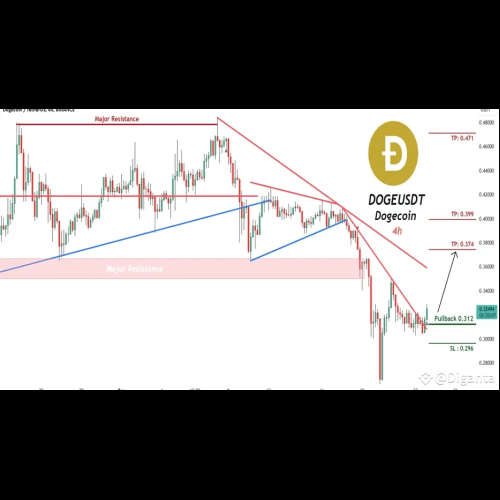
- 我们来谈谈狗狗币吧! 😂
- 2024-12-24 10:55:02
- 嘿,币安家族,我们在 DOGEUSDT(狗狗币)市场的 4 小时时间范围内发现了一个有趣的交易信号。这可能是一个跳上总督火箭的绝佳机会! 🚀
-

-
-
-

-

- 今年圣诞节市场升温,值得关注的 5 种加密货币
- 2024-12-24 10:45:02
- 当我们进入假期季节时,加密货币市场正在变得兴奋起来。从历史上看,年底市场活动会增加,今年圣诞节也不例外。
-

- 如何找到领先的人工智能代理加密项目
- 2024-12-24 10:45:02
- 近一个月来,AI Agent在加密行业掀起了新一波热潮。不到一个月的时间,整个AI Agent赛道项目市值就达到了数百亿美元。
-





































