
|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|
Cryptocurrency News Articles
Critical OpenMetadata Platform Flaws Threaten Kubernetes Workloads; Urgent Patches Needed
Apr 23, 2024 at 07:07 am
The OpenMetadata platform, utilized for data discovery and governance, has been compromised by critical vulnerabilities, enabling attackers to bypass authentication and execute Remote Code Execution (RCE) on Kubernetes workloads. These vulnerabilities permit unauthorized access and crypto-mining activities. Microsoft has urged users to apply updates to OpenMetadata and reinforce authentication measures to mitigate potential exploitation.

Critical Vulnerabilities in OpenMetadata Platform Pose Severe Threat to Kubernetes Workloads: Urgent Mitigation Required
[Redmond, Washington] - February 28, 2023
Cybersecurity researchers from Microsoft have uncovered a series of critical vulnerabilities in the OpenMetadata platform that empower threat actors to exploit Kubernetes workloads for clandestine crypto mining activities. These vulnerabilities have the potential to compromise enterprise environments and disrupt critical business operations.
The Microsoft security blog has issued a stark warning, revealing that five significant vulnerabilities allow attackers to bypass authentication and execute Remote Code Execution (RCE) on affected Kubernetes workloads. These vulnerabilities, designated as CVE-2024-28255, CVE-2024-28847, CVE-2024-28253, CVE-2024-28848, and CVE-2024-28254, affect OpenMetadata versions preceding 1.3.1.
Understanding the Vulnerabilities
CVE-2024-28255, rated 9.8 on the Common Vulnerability Scoring System (CVSS), exploits a flaw in the API authentication mechanism of OpenMetadata. By exploiting this vulnerability, attackers can bypass authentication and gain unauthorized access to sensitive endpoints.
CVE-2024-28255, assigned a CVSS score of 9.4, stems from deficiencies in JWT token validation within the JwtFilter component. This vulnerability allows attackers to send a malicious PUT request to modify system policies, potentially leading to remote code execution.
Exploitation Modus Operandi
Security analysts have observed a systematic attack sequence involving the exploitation of these vulnerabilities:
- Vulnerability Identification and Exploitation: Attackers target vulnerable versions of OpenMetadata and exploit the vulnerabilities to gain initial code execution within the container hosting the compromised image.
- Intrusion Validation and Connectivity Establishment: Post-infiltration, attackers validate their intrusion through ping requests to specific domains linked to Interactsh, a popular tool for attacker communication.
- Crypto-Mining Malware Deployment: Once successful access is established, attackers download crypto-mining malware from a remote server and execute it with elevated permissions. The server hosting the malware has been traced to China.
Mitigation Measures
To mitigate these threats and protect OpenMetadata workloads, organizations are strongly advised to implement the following measures:
- Update to OpenMetadata 1.3.1 or Later: Update the image version of Kubernetes clusters running OpenMetadata to the latest version, specifically 1.3.1 or newer, to patch these vulnerabilities.
- Strong Authentication: Employ robust authentication mechanisms for accessing OpenMetadata over the Internet. Avoid using default credentials and consider implementing multi-factor authentication.
- Network Segmentation: Restrict access to OpenMetadata workloads from untrusted networks to reduce the attack surface.
- Regular Security Audits: Conduct regular security audits to scan for vulnerabilities and misconfigurations that could expose OpenMetadata to attacks.
- Incident Response Plan: Establish an incident response plan to promptly detect and mitigate potential security breaches.
Organizations using OpenMetadata are urged to prioritize these mitigation measures to prevent exploitation of these critical vulnerabilities and protect their Kubernetes workloads from malicious crypto mining activities.
Disclaimer:info@kdj.com
The information provided is not trading advice. kdj.com does not assume any responsibility for any investments made based on the information provided in this article. Cryptocurrencies are highly volatile and it is highly recommended that you invest with caution after thorough research!
If you believe that the content used on this website infringes your copyright, please contact us immediately (info@kdj.com) and we will delete it promptly.
-
-
-

-
-
-

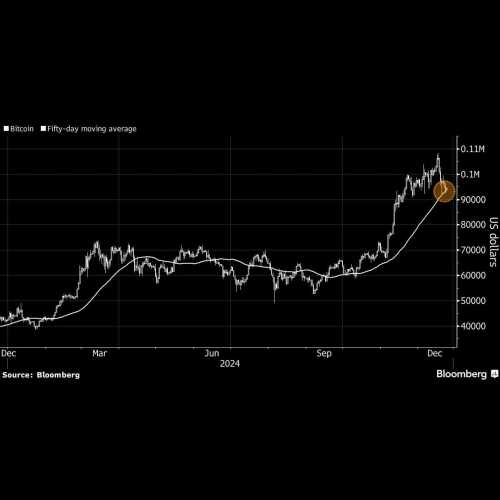
- RWA Tokenization Platform Allo Secures $100M in Debt Financing to Bolster Bitcoin (BTC)-Backed Lending Business
- Dec 24, 2024 at 10:45 am
- The RWA market currently hovers near $900 trillion, while tokenized assets are projected to make up 10% of global gross domestic product worth $24 trillion by 2027.
-

-

-





































