|
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
在比特幣交易期間確定和防止非法交易是私人金融市場的挑戰性問題。
Cryptocurrency has become increasingly used these days. It is a digital currency, i.e. the encrypted data strings which only exist electronically. They are not decentralized; in other words, they are not issued by the government. Cryptography algorithms are used to create cryptocurrency and they are validated through mining1. If the miners are successful, they will receive cryptocurrency as a reward2,3,4. These electronic currencies are stored in a structure and it is called blockchain. Blockchain gives information with node details in a distributed environment. The information cannot be edited or ruined. Transactions occur in blocks of data, and each block has a pointer to the previous block. The arrival of Bitcoin has triggered the popularity of cryptocurrency5. However, this recurring use of cryptocurrency has captured the attention of many scammers. Cryptocurrency scams occur through many means; ransomware attack, financial crimes, Ponzi schemes, etc. However, cryptocurrency is a small network that provides anonymity to its users. Scammers take advantage of this and use this facility to camouflage themselves.
如今,加密貨幣已經越來越多地使用。這是一種數字貨幣,即僅在電子上存在的加密數據字符串。他們不是分散的;換句話說,它們不是由政府發行的。加密算法用於創建加密貨幣,並通過Mining1進行驗證。如果礦工成功,他們將獲得加密貨幣作為獎勵2,3,4。這些電子貨幣存儲在結構中,稱為區塊鏈。區塊鏈在分佈式環境中提供了帶有節點詳細信息的信息。信息不能編輯或破壞。交易發生在數據塊中,每個塊都有指向上一個塊的指針。比特幣的到來觸發了加密貨幣的普及5。但是,這種反複使用的加密貨幣吸引了許多騙子的注意。加密貨幣騙局通過多種方式發生。勒索軟件攻擊,金融犯罪,龐氏騙局等。但是,加密貨幣是一個為用戶提供匿名的小網絡。騙子利用這一點,並利用此設施偽裝自己。
Bitcoin
比特幣
Bitcoin is one of the first cryptocurrency. It works by using blockchain and is more valuable than others. The bitcoin blockchain can be viewed as a shared ledger in which every transaction is recorded and cannot be changed. Each block has a unique hash pointer which points to the previous block. These points are the links between each block. Nodes in the network would validate the new transaction and is added to the ledger or the blockchain which is then published to the rest of the nodes. When mining is done to create new bitcoin, the miner gets the unique hash value of the new coin using algorithms. In recent days, the Bitcoin’s pseudonymity is used for illegal activities such as goods transport and banking transactions6.
比特幣是第一個加密貨幣之一。它通過使用區塊鏈而起作用,並且比其他區塊更有價值。比特幣區塊鏈可以看作是共享分類帳,其中每次交易被記錄並且不能更改。每個塊都有一個唯一的哈希指針,指向上一個塊。這些點是每個塊之間的鏈接。網絡中的節點將驗證新事務,並將其添加到分類帳或區塊鏈中,然後將其發佈到其餘節點。採礦以創建新的比特幣時,礦工使用算法獲得了新硬幣的唯一哈希值。最近幾天,比特幣的化名用於非法活動,例如商品運輸和銀行交易6。
Anti money laundering in cryptocurrency
在加密貨幣中洗錢
Weaker sections of society struggle to be included in the financial process of the country. Financial inclusion basically means providing access to these groups of society to participate in the country’s financial development by providing them with financial services and products at a reasonable cost. But these marginal groups are restricted access to these systems, which is an accidental repercussion of Anti Money Laundering (AML) regulations. Unfortunately, these regulations cannot be avoided to maintain the protection of our economy. AML also results in relatively higher costs on products. AML regulations are mandatory and must be followed because many illegal transactions are identified and thus avoided.
社會較弱的部分難以將其納入該國的財務過程中。金融包容基本上意味著通過為這些社會群體提供訪問權,以合理的成本為他們提供金融服務和產品,從而參與該國的財務發展。但是這些邊際群體受到限制對這些系統的訪問,這是對反洗錢(AML)法規的意外影響。不幸的是,這些法規無法避免維持對我們經濟的保護。 AML還導致產品成本相對較高。 AML法規是強制性的,必須遵循,因為確定了許多非法交易並因此避免。
Literature review
文獻綜述
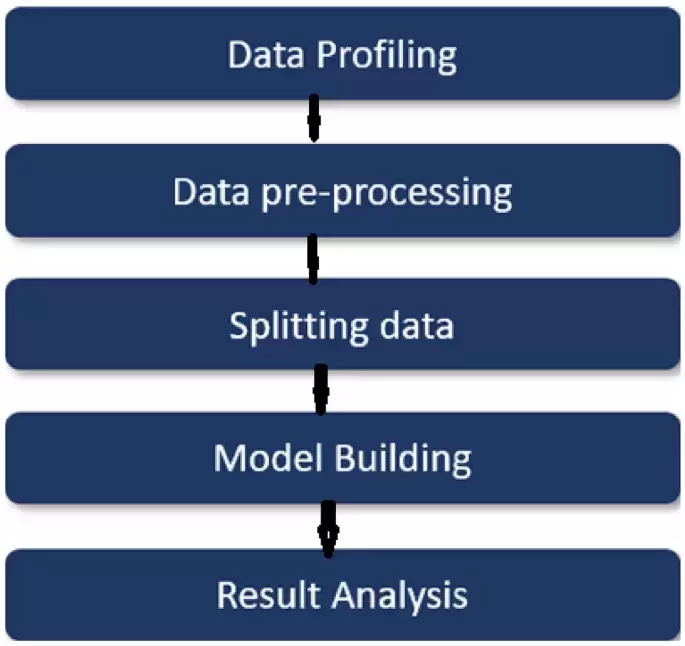
The financial marketing studies say that Bitcoin purchase increases in 2024. While the volume of transactions increases, fraudulent activities also increased7. Dhanya8 collected the Bitcoin data from 2013 to 2018 and proposed rollover techniques for better prediction of accuracy in the time series model. She considered the Bitcoin date from The bitcoin data from 2013 to 2018. Also recent machine learning methods overcome the time series mode. In this paper, we consider the data till 2024. The proposed security protocol for Bitcoin is one of the important aspects. Recently, Badertscher et al.9 proposed a security proof for the Bitcoin protocol. They proposed a secure protocol for global clock and hash functions. As an application and case study, Kumar et al.10 proposed a model for blockchain-based land registration. In an unpublished Arxiv paper, Weber et al.6 proposed different machine learning models to predict illicit transactions. They have found precision, recall, F1 score, and micro-average. For illicit transactions with GCN, their precision value is 0812, Recall score is 0.512 and R1 score is 0.628. Our experimental results are shown in the section 4.1, which improved their results. Chen et al.11 gave a detailed survey on different machine learning methods to detect suspicious transactions on Bitcoin11. In this paper, they have an analysis of some of the important aspects such as risk scoring, link analysis and behavioral modeling. Klaus Grobys et al.12 proposed a statistical distribution model for stolen Bitcoins. Features extractions are one of the important in the study of Bitcoin transactions. Vlahavas et al.13 used a clustering algorithm for feature extractions. Pranav Nerurka14 proposed a graph attention network (GAT2) with accuracy of to identify illegal transactions.
金融營銷研究表明,比特幣購買在2024年增加。雖然交易量增加,但欺詐活動也增加了7。 Dhanya8從2013年到2018年收集了比特幣數據,並提出了擬議的翻轉技術,以更好地預測時間序列模型的準確性。她考慮了比特幣的日期,從2013年到2018年的比特幣數據。最近的機器學習方法也克服了時間序列模式。在本文中,我們考慮到2024年的數據。比特幣的擬議安全協議是重要方面之一。最近,Badertscher等人9提出了比特幣協議的安全證明。他們為全局時鐘和哈希功能提出了一個安全的協議。作為一項應用和案例研究,Kumar等人10提出了一個基於區塊鏈的土地註冊的模型。 Weber等人在未發表的Arxiv論文中。 6提出了不同的機器學習模型來預測非法交易。他們發現了精度,召回,F1分數和微平均水平。對於與GCN的非法交易,其精度值為0812,召回得分為0.512,R1得分為0.628。我們的實驗結果顯示在第4.1節中,這改善了其結果。 Chen等人11對不同的機器學習方法進行了詳細的調查,以檢測比特幣上的可疑交易。在本文中,他們對一些重要方面進行了分析,例如風險評分,鏈接分析和行為建模。 Klaus Grobys等人112提出了一個被盜比特幣的統計分佈模型。提取物是比特幣交易研究中的重要之一。 Vlahavas等人13使用聚類算法進行特徵提取。 Pranav Nerurka14提出了一個圖形注意網絡(GAT2),其準確性以識別非法交易。
Motivations and key contributions
動機和關鍵貢獻
Identifying and preventing the illegal transactions during bitcoin transactions are challenging problems in the private financial market. The actor called a “miner” (person/machine) will participate and validate all the Bitcoin transactions. The miner is considered the most important person for the creation of new cryptocurrencies and their validations. The minor’s decision is based on his mathematical model used for the transactions. Even a small error in the prediction model leads to a huge financial loss for the transacting people. For example, during the 10-year period 2011–2021, nearly 1.7 million Bitcoin units were stolen due to criminal activity, with losses exceeding 700 million12. So,
在比特幣交易期間確定和防止非法交易是私人金融市場的挑戰性問題。演員稱為“礦工”(人/機器)將參與並驗證所有比特幣交易。礦工被認為是創建新的加密貨幣及其驗證的最重要的人。未成年人的決定基於他用於交易的數學模型。即使是預測模型中的一個小錯誤也會導致交易人員造成巨大的財務損失。例如,在2011 - 2021年的10年期間,由於犯罪活動,將近170萬個比特幣單位被盜,損失超過7億12。所以,
免責聲明:info@kdj.com
所提供的資訊並非交易建議。 kDJ.com對任何基於本文提供的資訊進行的投資不承擔任何責任。加密貨幣波動性較大,建議您充分研究後謹慎投資!
如果您認為本網站使用的內容侵犯了您的版權,請立即聯絡我們(info@kdj.com),我們將及時刪除。
-

-

- PI網絡問題導致用戶信任下降
- 2025-04-02 23:15:12
- PI網絡問題導致用戶信任下降,這對於團隊解決這些問題至關重要。
-

-

- 唐納德·特朗普總統決定建立美國政府加密保護區的決定引發了極大的興奮
- 2025-04-02 23:10:12
- 隨著財政部和聯邦機構將於4月5日透露包括比特幣在內的數字資產持有量,所有人都將向所有加密貨幣削減。
-

-

- 長期說最容易被說話的模因硬幣
- 2025-04-02 23:05:12
- RRX通過其龐大的社區和過去的拋物線運行吸引了零售投資者。市值不到100億美元
-

- 比特幣價格是NFT市場的脈搏
- 2025-04-02 23:00:14
- 比特幣不僅是另一個加密貨幣,而且是市場的脈動。現在,它是在告訴我們NFT的下一步將要發生的事情。
-

- Mutuum Finance(MUTM)準備使用其創新協議破壞貸款和借貸市場
- 2025-04-02 23:00:14
- 在許多加密代幣已經經歷了他們的主要運行時,仍然有一些隱藏的寶石仍然處於可訪問的價格。
-

- 陪審員退休以考慮他們的判決,以審判一個被指控刺傷一名13歲的男生
- 2025-04-02 22:55:12
- 去年,Jahziah Coke被發現在財產中受到嚴重傷害,無法保存