 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
Cryptocurrency News Video
Password reset token leak via "Host header" and "url" on third party website | Earn upto 200 to 300$
Feb 25, 2025 at 06:06 am Tech_Minded_Ashish
Password Reset Token Leak via "Host Header" and "URL" on a Third-Party Website This vulnerability occurs when a web application improperly handles password reset tokens, exposing them to attackers through: Host Header Manipulation: Some applications generate password reset links using the Host header provided in the HTTP request. If an attacker manipulates the Host header and the application blindly trusts it, the reset link might include a malicious domain controlled by the attacker. The victim, upon receiving and clicking the link, submits their reset token to the attacker's domain, allowing account takeover. URL Exposure on a Third-Party Website: If an application leaks password reset URLs in referer headers, logs, or third-party integrations, an attacker monitoring those locations can capture the reset token. Example: If the reset link is included in a URL parameter that gets logged or shared with external services (e.g., analytics tools, chatbots), attackers might retrieve it and reset the victim’s password. Impact Allows an attacker to reset passwords of victim accounts. Leads to full account takeover. Can be exploited remotely if combined with phishing or session hijacking. Mitigation ✅ Use absolute, hardcoded URLs for password reset links instead of relying on the Host header. ✅ Implement a strict Content Security Policy (CSP) to prevent token exposure in third-party requests. ✅ Avoid logging sensitive URLs and tokens. ✅ Use Referer-Policy: no-referrer to prevent leaks in referer headers. ✅ Ensure password reset tokens are short-lived and single-use. #ethicalhacking #bugbountyhunting #coding #cybersecurity #computersecurity
Disclaimer:info@kdj.com
The information provided is not trading advice. kdj.com does not assume any responsibility for any investments made based on the information provided in this article. Cryptocurrencies are highly volatile and it is highly recommended that you invest with caution after thorough research!
If you believe that the content used on this website infringes your copyright, please contact us immediately (info@kdj.com) and we will delete it promptly.
-
- The operation of ignoring information on the Bitcoin market on weekends is like covering up the ears!
- Apr 19, 2025 at 01:55 pm 领航时代1573
- Telegram free group: https://t.me/+Ic-ZFwGh... Telegram Telegram Private Chat: @linghangshidai1573 WeChat Public Account: Pioneering Times 1573 QQ Contact: 3766740475 All views do not constitute any investment advice! For learning and communication only. #bitcoin #Bitcoin #Ether#btc #Big cake #eth #doge #technical analysis #Dowry theory...
-

- 2025.4.19 Bitcoin Market Analysis | Weekend oscillations are preferred, where is the rhythm of the change? Short-term long, be prepared for the trend coming soon. It is true that the profit is too much, but don’t be greedy. BTC ETH BNB OKB DOGE LTC AVAX C
- Apr 19, 2025 at 01:55 pm 三一学社 币圈琛哥
- 💹Telegram public group: https://t.me/biquancheng 💹Telegram private chat: https://t.me/BTCcheng 💹Chenge personal Twitter: https://twitter.com/chenchenbtc 💹Chenge uses Chenge’s recommended link to register an exchange, recharge the specified amount, and you can join the Chenge’s strategy channel for free! The only joint exchange bitget: https://partner.bitget...
-
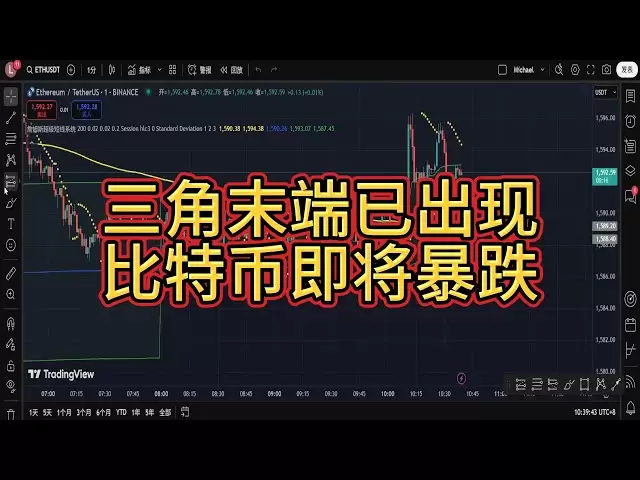
- Is Bitcoin about to experience big fluctuations? A narrow range of fluctuation for a week! Wavely moving forward, spiral decline is about to begin?
- Apr 19, 2025 at 01:50 pm 币圈小神仙
- #Bitcoin#Bitcoin#btc#market analysis#Bitcoin market analysisBitcoin is about to experience big fluctuations? A narrow range of fluctuation for a week! Wavely moving forward, spiral decline is about to begin? Is Bitcoin about to experience big fluctuations? A narrow range of fluctuation for a week! Wavely moving forward, spiral decline is about to begin? Michael is good at using harmonic form trading and Vegas tunnel trading system, and is also the founder of Kobe's trading system. Entering the circle in 2019, making steady profits for more than 5 years! Happy to share and look forward to communication! Michael Financial Telegram Fan Group: https://t.me...
-
- Analysis of BTC and ETH on April 19, 2025. Bitcoin has been sideways for 6 consecutive days, and the change is coming. Pay attention to this key signal. Lay out the operation ideas next week in advance, and wait patiently for #eth#btc##cryptocurrency#cz#d
- Apr 19, 2025 at 01:50 pm 三一学社 比特币清风
- 💹Telegram public group: https://t.me/qingfengBTC 💹Telegram Telegram private chat: https://t.me/qingfengtrader 💹Qingfeng's only Twitter: https://twitter.com/qingfengtrader 💹 Bitget exchange's largest rebate activity: https://partner.bitget.fit/bg/TCQQ05 Invitation code: 26be Brothers who make contracts...
-
-

- Pi Network GCV New Update Today - Pi Network New Update Today - Pi Network Big Surprise Countdown
- Apr 19, 2025 at 01:45 pm Dey's Technical
- Pi Network GCV New Update Today - Pi Network New Update Today - Pi Network Big Surprise Countdown Dey's Technical Pionex Exchange Link: https://www.pionex.com/en/signUp?r=0jA2bdLfLa8 Pi...
-

- Pi Coin Plus Etherimum Coin | Pi Network Update | Pi News | | Pi Price | Albarizon
- Apr 19, 2025 at 01:40 pm albarizon
- How to Create Binanace Account: https://youtu.be/gtd48M6KVsA Link: https://accounts.binance.com/register?ref=714142769 Referral ID: 714142769 New Channel Link👇: https://youtube.com/@albarizone For...
-

- Pi Network Integration Ethereum | Pi Network Latest Update | Pi Coin Price Prediction |
- Apr 19, 2025 at 01:40 pm Faruk Monitor
- Pi Network Integration Ethereum | Pi Network Latest Update | Pi Coin Price Prediction | Pi Network Code 👍 farukcryotoking ✅Contact No 🤙 8252634344 ---------------------------+---------------...
-

- coindesk CONSENSUS2025 Toronto Meeting | Pi Network New Update, binance ethereum xrp mastercard visa
- Apr 19, 2025 at 01:35 pm MetaMitra
- मेटामित्र की All इन्विटेशन लिंक https://linktr.ee/metamitra मेटामित्र की इन्विटेशन लिंक से एक्सचेंज में अकॉउंट ओपन कर सकते हैं। MUDREX INDIAN EXCHANGE https://mudrexmobile.page.link/UyTGiRauS5...




















































