|
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
Cryptocurrency News Articles
Astrix Customers Break Boundaries in Non-Human Identity (NHI) Security: Triumphant Real-World Cases
Apr 22, 2024 at 06:54 pm
In this series, Astrix customers showcase innovative NHI security strategies. From automating NHI offboarding to eliminating super-admin tokens, these real-world examples provide insights into how Astrix empowers customers to address NHI security challenges.
Astrix Customers Lead the Way in Non-Human Identity (NHI) Security: Real-World Success Stories
Astrix Security customers are trailblazers in the realm of NHI security. From automating NHI offboarding processes to swiftly removing super-admin tokens, these real-life accounts offer valuable insights into the implementation of a robust NHI security strategy.
Chapter 1: Comprehensive NHI Inventory and Remediation
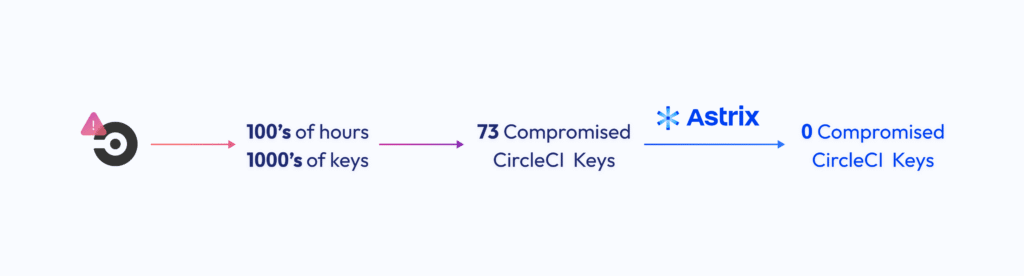
In the wake of a security breach, a leading SaaS provider was compelled to reassess the security of their NHI ecosystem, which encompasses tokens, secrets, and service accounts. Despite manually rotating thousands of keys, the nagging question remained: had they truly identified and resolved all compromised identities?
Enter Astrix Security. By leveraging Astrix's extensive capabilities, the security team unearthed 73 compromised CircleCI identities across multiple GitHub organizations. This startling discovery underscored the inadequacy of manual efforts and the critical need for automated NHI inventory and remediation.
Chapter 2: Implementing Zero Trust for NHIs
Fast forward a year, the company's security posture had undergone a remarkable transformation. Astrix's deep-dive analysis revealed the presence of numerous Super-Admin tokens with no expiration across their GitHub organizations. Recognizing the immense risk posed by these tokens, the security team partnered with engineering to eliminate the threat and implement best practices.
Within hours, they successfully removed the risky tokens and introduced a robust policy for token rotation and least privilege. This swift and decisive action effectively neutralized the threat posed by these over-privileged tokens.
Chapter 3: Emerging NHI Experts
Beyond the specific case studies, these experiences highlight the transformative impact of Astrix on the customer's security team. They gained expertise in a previously uncharted territory, enabling them to:
- Identify and close critical security gaps
- Implement best practices across the organization
- Foster collaboration between security and engineering teams
- Raise awareness about the vulnerabilities and misuse of NHIs
Armed with this newfound expertise, the security team can now enforce NHI policies and best practices across diverse environments, ensuring tight security while embracing the benefits of NHI automation and connectivity.
Astrix: Empowering Customers in the NHI Security Frontier
These real-world success stories exemplify the value of Astrix Security's platform in empowering customers to lead the non-human identity security frontier. By equipping them with comprehensive NHI inventory, intelligent remediation capabilities, and deep security context, Astrix enables organizations to:
- Detect and neutralize NHI-related threats promptly
- Implement zero-trust principles for NHIs
- Become NHI security experts
- Enhance collaboration between security and business teams
- Drive security awareness and best practices throughout the organization
As the NHI landscape continues to evolve, Astrix Security remains committed to providing customers with the most innovative and effective solutions to safeguard their digital infrastructure. By partnering with Astrix, organizations can confidently navigate the complexities of NHI security, protect their critical assets, and achieve their business objectives in a secure and compliant manner.
Disclaimer:info@kdj.com
The information provided is not trading advice. kdj.com does not assume any responsibility for any investments made based on the information provided in this article. Cryptocurrencies are highly volatile and it is highly recommended that you invest with caution after thorough research!
If you believe that the content used on this website infringes your copyright, please contact us immediately (info@kdj.com) and we will delete it promptly.
-

-

-

-

-

- Ethereum (ETH) Price Attempts to Stabilize After Dipping Below $1,600. Long-Term Holders Have Entered Capitulation Territory
- Apr 12, 2025 at 11:25 am
- Ethereum price is attempting to stabilize after dipping below $1,600. Long-term holders have entered capitulation territory for the first time in months.
-

-

-

-




















![Crypto Otaku - CRYPTO CHAOS! 83K BITCOIN! CRYPTO RALLY!! XCN , JASMY , SWFTC LEAD!!! [Episode 228] Crypto Otaku - CRYPTO CHAOS! 83K BITCOIN! CRYPTO RALLY!! XCN , JASMY , SWFTC LEAD!!! [Episode 228]](/uploads/2025/04/12/cryptocurrencies-news/videos/crypto-otaku-crypto-chaos-k-bitcoin-crypto-rally-xcn-jasmy-swftc-lead-episode/image-1.webp)