-
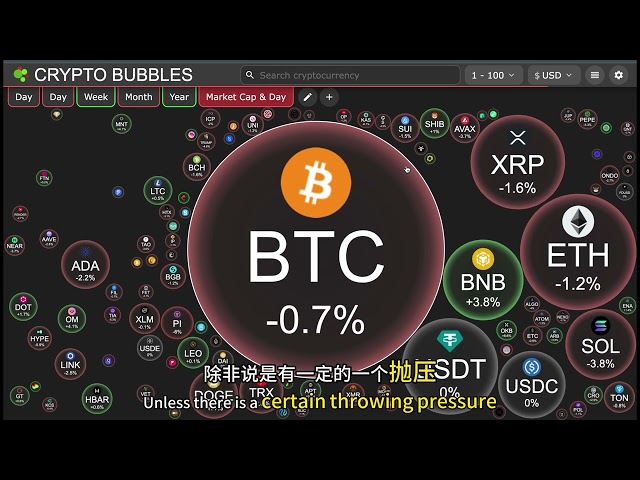
 Bitcoin
Bitcoin $83,267.6339
-0.22% -
 Ethereum
Ethereum $1,910.4421
0.59% -
 Tether USDt
Tether USDt $0.9999
-0.02% -
 XRP
XRP $2.3289
-0.69% -
 BNB
BNB $637.3734
6.38% -
 Solana
Solana $128.8563
-2.95% -
 USDC
USDC $1.0000
0.01% -
 Dogecoin
Dogecoin $0.1732
1.34% -
 Cardano
Cardano $0.7206
-0.36% -
 TRON
TRON $0.2147
-0.56% -
 Pi
Pi $1.3599
-6.77% -
 UNUS SED LEO
UNUS SED LEO $9.8297
0.05% -
 Chainlink
Chainlink $13.7729
-0.67% -
 Toncoin
Toncoin $3.3994
-0.35% -
 Stellar
Stellar $0.2709
0.69% -
 Hedera
Hedera $0.1899
0.68% -
 Avalanche
Avalanche $18.6247
-0.62% -
 Shiba Inu
Shiba Inu $0.0...01309
1.75% -
 Sui
Sui $2.2834
-0.20% -
 Litecoin
Litecoin $93.4414
3.24% -
 Polkadot
Polkadot $4.3758
2.99% -
 MANTRA
MANTRA $6.8177
3.23% -
 Bitcoin Cash
Bitcoin Cash $335.6751
1.56% -
 Ethena USDe
Ethena USDe $0.9996
-0.02% -
 Dai
Dai $1.0000
-0.02% -
 Bitget Token
Bitget Token $4.4428
0.50% -
 Hyperliquid
Hyperliquid $13.9667
3.87% -
 Monero
Monero $209.4895
-1.24% -
 Uniswap
Uniswap $6.2429
1.46% -
 Aptos
Aptos $5.3667
2.10%
How to respond if the private key of a Bitcoin wallet is leaked?
A leaked Bitcoin private key demands immediate action: transfer funds to a new, secure wallet, contact relevant exchanges or authorities, and enhance security practices to prevent future leaks. Speed minimizes losses.
Mar 15, 2025 at 09:31 pm

Key Points:
- Immediate action is crucial upon suspecting a private key leak. Delay increases the risk of significant financial loss.
- The severity of the response depends on the type of wallet and the level of access the attacker might have.
- Securing remaining assets requires swift transfer to a new, secure wallet.
- Reporting the incident to relevant authorities and exchanges might be necessary, depending on the circumstances.
- Prevention through strong security practices is paramount.
How to Respond if the Private Key of a Bitcoin Wallet is Leaked?
Discovering a leaked Bitcoin private key is a critical situation demanding immediate and decisive action. The first step is to assess the extent of the compromise. Did someone directly obtain your private key, or was it potentially exposed through a vulnerability in a software wallet or exchange? Understanding this will guide your response.
If you suspect a leak through a compromised exchange or service, immediately contact their support team. Many exchanges have security protocols to mitigate such incidents, and contacting them promptly might limit the damage. Simultaneously, begin securing your remaining assets.
Next, you need to move your Bitcoin to a new, secure wallet. This is paramount. Do not use the compromised wallet again. Create a new wallet using reputable software or a hardware wallet, ensuring you follow best practices for generating and securing new keys. Transfer your remaining Bitcoin to this new wallet as quickly as possible. This minimizes the window of vulnerability.
The method of transferring your Bitcoin will depend on the type of wallet you're using. For example, if you're using a desktop wallet, you'll need to use the wallet software's functionality to initiate a transaction. If your funds are on an exchange, the transfer process will be through the exchange interface. Remember, speed is of the essence.
Consider the type of wallet involved. A hardware wallet leak is less common and usually implies physical theft or compromise of the device itself. Software wallets are more vulnerable to malware or phishing attacks, while paper wallets present a risk of physical loss or damage. The response will differ based on this.
After securing your remaining assets, consider reporting the incident. Depending on the circumstances, you might need to report the incident to the relevant authorities, especially if you suspect criminal activity. Reporting to the exchange, if involved, might also trigger their security protocols and help prevent further attacks.
If you suspect your computer or device is compromised, take immediate steps to secure it. This includes running a full malware scan, changing all your passwords, and considering a complete operating system reinstallation. This helps to prevent further attacks and protect other sensitive information.
Remember, strong security practices are essential to prevent private key leaks. This includes using strong, unique passwords, enabling two-factor authentication (2FA) wherever possible, and being wary of phishing attempts. Regularly update your software and be cautious about the websites and applications you interact with.
Frequently Asked Questions:
Q: What if I only have a partial leak of my private key?
A: Even a partial leak can be extremely dangerous. Treat it as a full leak and take immediate action to secure your remaining funds by transferring them to a new wallet. The risk of someone piecing together the missing information is too high.
Q: Can I recover my Bitcoin if the private key is completely leaked and the funds are stolen?
A: Once your Bitcoin is transferred using your private key, it is generally considered irreversible. Recovering the funds after a complete leak is extremely difficult, if not impossible, without assistance from the blockchain or the individual who obtained your funds. Prevention is crucial.
Q: How can I verify if my private key has been leaked?
A: There's no foolproof method to verify a private key leak unless you see transactions being made from your wallet without your authorization. However, regular monitoring of your wallet balance and transaction history is important. Suspicious activity warrants immediate action.
Q: What should I do if I suspect my private key was leaked through a compromised exchange?
A: Contact the exchange's support team immediately. They may have procedures to help mitigate the issue. Simultaneously, move your remaining funds to a secure, independent wallet that is not associated with the compromised exchange.
Q: Are hardware wallets completely immune to private key leaks?
A: While hardware wallets offer significantly better security than software wallets, they are not entirely immune to leaks. Physical theft or compromise of the device can lead to private key exposure. Proper physical security measures are crucial.
Q: What are the best practices for securing my Bitcoin private keys?
A: Use strong, unique passwords, enable 2FA, utilize reputable hardware wallets, store your private keys offline (preferably using a paper wallet with multiple copies stored securely in different locations), and be extremely vigilant about phishing scams and malware. Regularly back up your wallet and keep your software updated.
Disclaimer:info@kdj.com
The information provided is not trading advice. kdj.com does not assume any responsibility for any investments made based on the information provided in this article. Cryptocurrencies are highly volatile and it is highly recommended that you invest with caution after thorough research!
If you believe that the content used on this website infringes your copyright, please contact us immediately (info@kdj.com) and we will delete it promptly.
- Solana (SOL) Cup-and-Handle Pattern Hints at Breakout Toward $3,800
- 2025-03-17 19:10:57
- IntelMarkets (INTL) Price Could See Growth Following the Potential Approval of an XRP ETF Before May
- 2025-03-17 19:10:57
- Cardano (ADA) whales are making better choices as they shift a portion of their holdings into Mutuum Finance (MUTM)
- 2025-03-17 19:10:57
- The Mustard Seed: A Thesis That Bitcoin Will Reach $10M per Coin by 2035
- 2025-03-17 19:10:57
- The U.S. pro-crypto pivot under President Donald Trump may come at a hefty price, one European Central Bank Governing Council member has warned.
- 2025-03-17 19:10:57
- 21Shares to Liquidate Its Bitcoin and Ethereum Futures-Tracking ETFs
- 2025-03-17 19:10:57
Related knowledge

How do I use multi-signature on my hardware wallet on my Ledger device?
Mar 17,2025 at 01:36am
Key Points:Multi-signature (multisig) wallets enhance security by requiring multiple approvals for transactions.Ledger devices support multisig through compatible wallets and specific configurations.Setting up multisig involves generating multiple keys and configuring the wallet accordingly.Understanding the intricacies of threshold signatures is crucia...

How do I use staking on my Ledger device?
Mar 17,2025 at 12:41pm
Key Points:Ledger devices offer a secure way to stake various cryptocurrencies. However, the process varies depending on the coin and the chosen staking provider.You'll generally need a Ledger Live account and the correct application installed on your device.Understanding the risks associated with staking, such as potential slashing, is crucial before p...

How do I export my private keys from my Ledger device?
Mar 17,2025 at 02:30pm
Key Points:Ledger devices do not directly "export" private keys in the traditional sense. The private keys are never revealed or accessible outside the secure element of the device.You can access and use your private keys indirectly through the device's interaction with your chosen wallet software.The process involves using your Ledger device with compa...

How do I fix a connection issue with my Ledger device?
Mar 16,2025 at 08:26am
Key Points:Troubleshooting Ledger connection issues often involves checking the device's charge, the USB cable, and the computer's USB ports.Software updates on both the Ledger device and its associated computer applications are crucial for optimal functionality and connection stability.Correctly installing the Ledger Live application and ensuring its c...

How do I use a password manager on my Ledger Nano S/X?
Mar 16,2025 at 09:25pm
Key Points:Ledger devices do not directly integrate with password managers. Their security model prioritizes offline key storage.You can use a password manager for your computer passwords, but not for your Ledger device seed phrase or PIN.Storing your Ledger PIN in a password manager is highly discouraged due to security risks.Strong, unique PINs and se...

How do I check the authenticity of my Ledger device?
Mar 17,2025 at 02:45pm
Key Points:Verifying your Ledger device's authenticity involves checking for several security features both on the device itself and through Ledger's official website.The packaging and the device itself contain unique identifiers that can be verified.Ledger's website provides tools to confirm the authenticity of your device and its bootloader.Understand...

How do I use multi-signature on my hardware wallet on my Ledger device?
Mar 17,2025 at 01:36am
Key Points:Multi-signature (multisig) wallets enhance security by requiring multiple approvals for transactions.Ledger devices support multisig through compatible wallets and specific configurations.Setting up multisig involves generating multiple keys and configuring the wallet accordingly.Understanding the intricacies of threshold signatures is crucia...

How do I use staking on my Ledger device?
Mar 17,2025 at 12:41pm
Key Points:Ledger devices offer a secure way to stake various cryptocurrencies. However, the process varies depending on the coin and the chosen staking provider.You'll generally need a Ledger Live account and the correct application installed on your device.Understanding the risks associated with staking, such as potential slashing, is crucial before p...

How do I export my private keys from my Ledger device?
Mar 17,2025 at 02:30pm
Key Points:Ledger devices do not directly "export" private keys in the traditional sense. The private keys are never revealed or accessible outside the secure element of the device.You can access and use your private keys indirectly through the device's interaction with your chosen wallet software.The process involves using your Ledger device with compa...

How do I fix a connection issue with my Ledger device?
Mar 16,2025 at 08:26am
Key Points:Troubleshooting Ledger connection issues often involves checking the device's charge, the USB cable, and the computer's USB ports.Software updates on both the Ledger device and its associated computer applications are crucial for optimal functionality and connection stability.Correctly installing the Ledger Live application and ensuring its c...

How do I use a password manager on my Ledger Nano S/X?
Mar 16,2025 at 09:25pm
Key Points:Ledger devices do not directly integrate with password managers. Their security model prioritizes offline key storage.You can use a password manager for your computer passwords, but not for your Ledger device seed phrase or PIN.Storing your Ledger PIN in a password manager is highly discouraged due to security risks.Strong, unique PINs and se...

How do I check the authenticity of my Ledger device?
Mar 17,2025 at 02:45pm
Key Points:Verifying your Ledger device's authenticity involves checking for several security features both on the device itself and through Ledger's official website.The packaging and the device itself contain unique identifiers that can be verified.Ledger's website provides tools to confirm the authenticity of your device and its bootloader.Understand...
See all articles