|
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
威胁研究员 Dancho Danchev 最近发现了 130 个似乎属于假冒加密货币卖家的域名。 WhoisXML API 研究团队试图
Recently, threat researcher Dancho Danchev uncovered 130 domains that seemingly belong to fake cryptocurrency sellers. The WhoisXML API research team sought to find potential connections to the threat by expanding the current list of indicators of compromise (IoCs) using our vast array of DNS intelligence sources.
最近,威胁研究人员 Dancho Danchev 发现了 130 个看似属于假冒加密货币卖家的域名。 WhoisXML API 研究团队试图通过使用我们大量的 DNS 情报源扩展当前的妥协指标 (IoC) 列表来寻找与威胁的潜在联系。
Our in-depth investigation led to the discovery of:
我们的深入调查发现:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
从我们的分析中获得的其他工件的样本可以从我们的网站下载。
More IoC Facts
更多国际奥委会事实
To learn more about the 130 domain names tagged as IoCs, we performed a bulk WHOIS lookup, which revealed that:
为了了解有关标记为 IoC 的 130 个域名的更多信息,我们执行了批量 WHOIS 查找,结果显示:
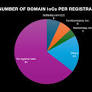
The actors behind the malicious fake cryptocurrency-selling campaigns used both old and new domain names. The oldest domain IoC was created in 2014, while the newest two domains were created in 2024. Eighteen domains were created in 2023; seven in 2021; six each in 2019, 2020, and 2022; two in 2024; and one each in 2014 and 2016. Finally, 83 domain IoCs did not have creation dates in their current WHOIS records.
恶意假冒加密货币销售活动背后的参与者同时使用了新旧域名。最古老的 IoC 域创建于 2014 年,最新的两个域创建于 2024 年。2023 年创建了 18 个域; 2021 年 7 个; 2019 年、2020 年和 2022 年各 6 个; 2024 年两次; 2014 年和 2016 年各有一个。最后,83 个域 IoC 在其当前的 WHOIS 记录中没有创建日期。
The domain IoCs were spread across 11 countries topped by the U.S., which accounted for 28 domains. Four domains were registered in Iceland. Austria, China, and the U.K. accounted for two domain IoCs each. One domain each was registered in Cyprus, Denmark, Germany, Kazakhstan, Switzerland, and Turkey. Finally, 86 domain IoCs did not have registrant countries in their current WHOIS records.
域 IoC 分布在 11 个国家,其中美国最多,占 28 个域。四个域名在冰岛注册。奥地利、中国和英国各占两个域 IoC。塞浦路斯、丹麦、德国、哈萨克斯坦、瑞士和土耳其各注册了一个域名。最后,86 个域名 IoC 在其当前的 WHOIS 记录中没有注册国家/地区。
IoC DNS Footprints
IoC DNS 足迹
To uncover other artifacts potentially connected to the fake cryptocurrency-selling campaigns, we first performed WHOIS History API queries for the 130 domains tagged as IoCs. Their historical WHOIS records contained 336 email addresses after duplicates were removed, 57 of which were public.
为了发现可能与虚假加密货币销售活动相关的其他工件,我们首先对标记为 IoC 的 130 个域执行 WHOIS History API 查询。删除重复项后,他们的 WHOIS 历史记录包含 336 个电子邮件地址,其中 57 个是公开的。
We then used the 57 public email addresses as reverse WHOIS API search terms and found 522 email-connected domains after duplicates and the IoCs were filtered out. Twenty-one of the email-connected domains were associated with 1—2 threats according to Threat Intelligence API. Take a look at five examples below.
然后,我们使用 57 个公共电子邮件地址作为反向 WHOIS API 搜索词,在过滤掉重复项和 IoC 后发现了 522 个与电子邮件连接的域。根据威胁情报 API,21 个电子邮件连接域与 1-2 个威胁相关。看看下面的五个例子。
Next, DNS lookups for the 130 domains tagged as IoCs revealed that 91 of them did not actively resolve to any IP address. The remaining 39 domain IoCs, meanwhile, resolved to 41 IP addresses after duplicates were removed. Threat Intelligence Lookup showed that 39 of them were associated with various threats. Take a look at five examples below.
接下来,对标记为 IoC 的 130 个域的 DNS 查找显示,其中 91 个域没有主动解析到任何 IP 地址。与此同时,其余 39 个域 IoC 在删除重复项后解析为 41 个 IP 地址。威胁情报查找显示,其中 39 个与各种威胁相关。看看下面的五个例子。
A bulk IP geolocation lookup for the 41 IP addresses showed that:
对 41 个 IP 地址的批量 IP 地理定位查找显示:
They were also spread across 12 ISPs topped by Amazon, which accounted for 22 IP address IoCs. Automattic, Cloudflare, and Namecheap tied in second place with two IP IoCs each. One IP address IoC each was administered by Confluence Networks, GigeNET, Hong KongMegalayer Technology Co., Hostinger International, http.net Internet GmbH, LeaseWeb U.S.A., UCloud Information Technology (HK) Limited, and World4You Internet Services GmbH. Finally, five IP addresses did not have ISPs in their A records.
它们还分布在以亚马逊为首的 12 个 ISP 中,占 22 个 IP 地址 IoC。 Automattic、Cloudflare 和 Namecheap 并列第二,各有两个 IP IoC。各一个 IP 地址 IoC 由 Confluence Networks、GigeNET、Hong KongMegalayer Technology Co.、Hostinger International、http.net Internet GmbH、LeaseWeb USA、UCloud Information Technology (HK) Limited 和 World4You Internet Services GmbH 管理。最后,有五个 IP 地址的 A 记录中没有 ISP。
We also subjected the 41 IP addresses to reverse IP lookups and found that only two of them could be dedicated. Altogether, they hosted 259 domains after duplicates, the IoCs, and the email-connected domains were filtered out.
我们还对 41 个 IP 地址进行了反向 IP 查找,发现其中只有两个可以专用。在过滤掉重复项、IoC 和电子邮件连接域后,它们总共托管了 259 个域。
To cover all bases, we looked for domains that started with the same text strings as the IoCs. They only used different topTLD extensions. Eighty-four text strings also appeared in 1,947 string-connected domains. They were:
为了涵盖所有基础,我们寻找以与 IoC 相同的文本字符串开头的域。他们仅使用不同的顶级顶级域名 (topTLD) 扩展名。 84 个文本字符串也出现在 1,947 个字符串连接域中。他们是:
Threat Intelligence API found that 15 of them were associated with various threats. Take a look at five examples below.
威胁情报 API 发现其中 15 个与各种威胁相关。看看下面的五个例子。
Our DNS deep dive into the fake cryptocurrency-selling campaigns led to the discovery of 2,769 potentially connected artifacts. Many of them, 75 to be exact, seem to have already been weaponized. As cryptocurrency usage becomes more popular, we are bound to see more threats targeting them, making staying ahead of the curve critical.
我们的 DNS 深入研究了虚假加密货币销售活动,发现了 2,769 个潜在关联的工件。他们中的许多人,确切地说是 75 人,似乎已经武器化了。随着加密货币的使用变得越来越流行,我们必然会看到更多针对它们的威胁,因此保持领先地位至关重要。
Download a sample of the threat research materials now or contact sales to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
立即下载威胁研究材料样本或联系销售人员讨论您对威胁检测和响应或其他网络安全用例的情报需求。
免责声明:info@kdj.com
所提供的信息并非交易建议。根据本文提供的信息进行的任何投资,kdj.com不承担任何责任。加密货币具有高波动性,强烈建议您深入研究后,谨慎投资!
如您认为本网站上使用的内容侵犯了您的版权,请立即联系我们(info@kdj.com),我们将及时删除。
-

-

-

-

-

-

- Solaxy(SOLX)预售涉及3000万美元的里程碑
- 2025-04-05 03:40:12
- Solaxy是第2层模因硬币,旨在增强Solana的可扩展性和解决网络拥塞,同时削减交易成本。
-

-

- 象征性的黄金资本化已经超过了12亿美元的大关
- 2025-04-05 03:35:12
- 这种增长是由于黄金价格飙升和对区块链资产的兴趣日益增加所致。对金牌加密资产的兴趣日益加剧,是使存储现代化的更广泛运动的一部分
-