|
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
威脅研究員 Dancho Danchev 最近發現了 130 個似乎屬於假加密貨幣賣家的網域。 WhoisXML API 研究團隊試圖
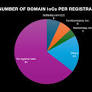
Recently, threat researcher Dancho Danchev uncovered 130 domains that seemingly belong to fake cryptocurrency sellers. The WhoisXML API research team sought to find potential connections to the threat by expanding the current list of indicators of compromise (IoCs) using our vast array of DNS intelligence sources.
最近,威脅研究人員 Dancho Danchev 發現了 130 個看似屬於假加密貨幣賣家的網域。 WhoisXML API 研究團隊試圖透過使用我們大量的 DNS 情報來源擴展目前的妥協指標 (IoC) 清單來尋找與威脅的潛在連結。
Our in-depth investigation led to the discovery of:
我們的深入調查發現:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
從我們的分析中獲得的其他工件的樣本可以從我們的網站下載。
More IoC Facts
更多國際奧委會事實
To learn more about the 130 domain names tagged as IoCs, we performed a bulk WHOIS lookup, which revealed that:
為了了解有關標記為 IoC 的 130 個網域的更多信息,我們執行了批量 WHOIS 查找,結果顯示:
The actors behind the malicious fake cryptocurrency-selling campaigns used both old and new domain names. The oldest domain IoC was created in 2014, while the newest two domains were created in 2024. Eighteen domains were created in 2023; seven in 2021; six each in 2019, 2020, and 2022; two in 2024; and one each in 2014 and 2016. Finally, 83 domain IoCs did not have creation dates in their current WHOIS records.
惡意假冒加密貨幣銷售活動背後的參與者同時使用了新舊網域。最古老的 IoC 域創建於 2014 年,最新的兩個域創建於 2024 年。 2021 年 7 個; 2019 年、2020 年及 2022 年各 6 個; 2024 年兩次; 2014 年和 2016 年各有一個。
The domain IoCs were spread across 11 countries topped by the U.S., which accounted for 28 domains. Four domains were registered in Iceland. Austria, China, and the U.K. accounted for two domain IoCs each. One domain each was registered in Cyprus, Denmark, Germany, Kazakhstan, Switzerland, and Turkey. Finally, 86 domain IoCs did not have registrant countries in their current WHOIS records.
域 IoC 分佈在 11 個國家,其中美國最多,佔 28 個域。四個網域在冰島註冊。奧地利、中國和英國各佔兩個域 IoC。塞浦路斯、丹麥、德國、哈薩克、瑞士和土耳其各註冊了一個網域。最後,86 個網域 IoC 在其目前的 WHOIS 記錄中沒有註冊國家。
IoC DNS Footprints
IoC DNS 足跡
To uncover other artifacts potentially connected to the fake cryptocurrency-selling campaigns, we first performed WHOIS History API queries for the 130 domains tagged as IoCs. Their historical WHOIS records contained 336 email addresses after duplicates were removed, 57 of which were public.
為了發現可能與虛假加密貨幣銷售活動相關的其他工件,我們首先對標記為 IoC 的 130 個網域執行 WHOIS History API 查詢。刪除重複項後,他們的 WHOIS 歷史記錄包含 336 個電子郵件地址,其中 57 個是公開的。
We then used the 57 public email addresses as reverse WHOIS API search terms and found 522 email-connected domains after duplicates and the IoCs were filtered out. Twenty-one of the email-connected domains were associated with 1—2 threats according to Threat Intelligence API. Take a look at five examples below.
然後,我們使用 57 個公共電子郵件地址作為反向 WHOIS API 搜尋字詞,在重複項和 IoC 被過濾掉後發現了 522 個電子郵件連接網域。根據威脅情報 API,21 個電子郵件連線域與 1-2 個威脅相關。看看下面的五個例子。
Next, DNS lookups for the 130 domains tagged as IoCs revealed that 91 of them did not actively resolve to any IP address. The remaining 39 domain IoCs, meanwhile, resolved to 41 IP addresses after duplicates were removed. Threat Intelligence Lookup showed that 39 of them were associated with various threats. Take a look at five examples below.
接下來,對標記為 IoC 的 130 個網域的 DNS 查找顯示,其中 91 個網域沒有主動解析到任何 IP 位址。同時,其餘 39 個域 IoC 在刪除重複項後解析為 41 個 IP 位址。威脅情報查找顯示,其中 39 個與各種威脅相關。看看下面的五個例子。
A bulk IP geolocation lookup for the 41 IP addresses showed that:
對 41 個 IP 位址的批次 IP 地理定位查找顯示:
They were also spread across 12 ISPs topped by Amazon, which accounted for 22 IP address IoCs. Automattic, Cloudflare, and Namecheap tied in second place with two IP IoCs each. One IP address IoC each was administered by Confluence Networks, GigeNET, Hong KongMegalayer Technology Co., Hostinger International, http.net Internet GmbH, LeaseWeb U.S.A., UCloud Information Technology (HK) Limited, and World4You Internet Services GmbH. Finally, five IP addresses did not have ISPs in their A records.
它們也分佈在以亞馬遜為首的 12 個 ISP 中,佔 22 個 IP 位址 IoC。 Automattic、Cloudflare 和 Namecheap 並列第二,各有兩個 IP IoC。各一個 IP 位址 IoC 由 Confluence Networks、GigeNET、Hong KongMegalayer Technology Co.、Hostinger International、http.net Internet GmbH、LeaseWeb USA、UCloud Information Technology (HK) Limited 和 World4You Internet Services GmbH 管理。最後,有五個 IP 位址的 A 記錄中沒有 ISP。
We also subjected the 41 IP addresses to reverse IP lookups and found that only two of them could be dedicated. Altogether, they hosted 259 domains after duplicates, the IoCs, and the email-connected domains were filtered out.
我們也對 41 個 IP 位址進行了反向 IP 查找,發現其中只有兩個可以專用。在過濾掉重複項、IoC 和電子郵件連接網域後,它們總共託管了 259 個網域。
To cover all bases, we looked for domains that started with the same text strings as the IoCs. They only used different topTLD extensions. Eighty-four text strings also appeared in 1,947 string-connected domains. They were:
為了涵蓋所有基礎,我們尋找以與 IoC 相同的文字字串開頭的域。他們只使用不同的頂級頂級域名 (topTLD) 擴展名。 84 個文字字串也出現在 1,947 個字串連接域。他們是:
Threat Intelligence API found that 15 of them were associated with various threats. Take a look at five examples below.
威脅情報 API 發現其中 15 個與各種威脅有關。看看下面的五個例子。
Our DNS deep dive into the fake cryptocurrency-selling campaigns led to the discovery of 2,769 potentially connected artifacts. Many of them, 75 to be exact, seem to have already been weaponized. As cryptocurrency usage becomes more popular, we are bound to see more threats targeting them, making staying ahead of the curve critical.
我們的 DNS 深入研究了虛假加密貨幣銷售活動,發現了 2,769 個潛在關聯的工件。他們中的許多人,確切地說是 75 人,似乎已經武器化了。隨著加密貨幣的使用變得越來越流行,我們必然會看到更多針對它們的威脅,因此保持領先地位至關重要。
Download a sample of the threat research materials now or contact sales to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
立即下載威脅研究資料樣本或聯絡銷售人員討論您對威脅偵測和回應或其他網路安全用例的情報需求。
免責聲明:info@kdj.com
所提供的資訊並非交易建議。 kDJ.com對任何基於本文提供的資訊進行的投資不承擔任何責任。加密貨幣波動性較大,建議您充分研究後謹慎投資!
如果您認為本網站使用的內容侵犯了您的版權,請立即聯絡我們(info@kdj.com),我們將及時刪除。
-

-

- Kishu(OK X)將注意力作為高利潤機會,基金為0.15%。
- 2025-04-04 10:30:12
- FTT有機會每天損失15.66美元,每天損失291.8美元。
-

- 唐納德·特朗普(Donald Trump)的新185個國家關稅計劃將比特幣和加密貨幣市場陷入短暫的混亂
- 2025-04-04 10:25:12
- 比特幣以及整個加密貨幣市場,在過去的幾個小時中,新浪的看跌感官擊中
-

-

- 隨著2025年4月的展開,加密貨幣市場處於不斷變化狀態
- 2025-04-04 10:20:12
- 比特幣(BTC)保持其位置約為85,000美元,以太坊(ETH)和XRP試圖獲得動力
-

-

- 加密貨幣市場正經歷著巨大的湍流,以太坊(ETH)也不例外
- 2025-04-04 10:15:28
- 加密貨幣市場正經歷著巨大的湍流,以太坊(ETH)也不例外。以太坊(ETH)墜毀以下
-

-