
|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|

|
|
安全性在軟體開發中至關重要,預計到2028 年,應用程式安全市場將達到118.3 億美元。增強監管合規性等眾多優勢,並簡化使用者體驗。
Securing Applications through Authentication and Authorization: A Comprehensive Exploration
透過身份驗證和授權保護應用程式:全面探索
In the rapidly evolving realm of software development, security remains paramount. The global app security market is projected to reach a colossal $6.97 billion by 2024, and an estimated $11.83 billion by 2028. Amidst this burgeoning landscape, C# JSON Web Tokens (JWTs) have emerged as a powerful solution for managing user authentication and authorization, providing unparalleled efficiency and standardization.
在快速發展的軟體開發領域,安全性仍然至關重要。預計到2024 年,全球應用安全市場將達到69.7 億美元的巨大規模,到2028 年預計將達到118.3 億美元。和授權的強大解決方案,提供無與倫比的效率和標準化。
The Critical Role of Authentication and Authorization
身份驗證和授權的關鍵作用
A staggering majority of businesses lack confidence in their cybersecurity capabilities, while industry experts posit that every application suffers from at least four security vulnerabilities. Fortunately, technological advancements have ushered in a plethora of solutions to combat this pervasive threat.
驚人的大多數企業對其網路安全能力缺乏信心,而行業專家認為每個應用程式都至少存在四個安全漏洞。幸運的是,技術進步帶來了大量的解決方案來應對這種普遍的威脅。
Authentication and authorization, implemented through C# JWT Token, offer a robust defense mechanism for safeguarding applications. These measures confer numerous benefits, including:
透過 C# JWT 令牌實現的身份驗證和授權為保護應用程式提供了強大的防禦機制。這些措施帶來了許多好處,包括:
- Reduced Risks: Authorization in C# JWT ensures that only authorized individuals can access essential functionalities and resources, mitigating the likelihood of malicious attacks and data breaches.
- Regulatory Compliance: This dual approach guarantees that all access to sensitive data adheres to industry regulations, adding an extra layer of protection to your application.
Understanding Authentication and Authorization
降低風險:C# JWT 中的授權可確保只有經過授權的個人才能存取基本功能和資源,從而降低惡意攻擊和資料外洩的可能性。遵守行業法規,增加了額外的保護為您的應用程式提供保護層。
Authentication and authorization are indispensable data security processes employed by administrators to shield their systems from unauthorized access. While these terms may appear synonymous, they fulfill distinct roles.
身份驗證和授權是管理員用來保護其係統免受未經授權的存取的不可或缺的資料安全過程。雖然這些術語可能看起來是同義詞,但它們發揮著不同的作用。
Authentication: This process verifies the identity of users prior to granting access to applications. When attempting to access a website, for instance, users are required to provide credentials such as a username and password. If the submitted information matches the system's database, access is granted. Multiple authentication methods are available, including:
身份驗證:此程序在授予應用程式存取權限之前驗證使用者的身份。例如,當嘗試造訪網站時,使用者需要提供使用者名稱和密碼等憑證。如果提交的資訊與系統的資料庫匹配,則授予存取權限。可以使用多種身份驗證方法,包括:
- Email and Password: The prevalent method involves users inputting their email address and password to access an application and subsequently re-entering this information upon each session.
- SMS Authentication: This method requires users to input a one-time code received via text message upon accessing an application.
- Third-Party Authentication: Similar to SMS authentication, users receive a code from a mobile application to gain access.
- Biometric Authentication: This technology relies on fingerprint, facial, or voice recognition to verify user identity.
Authorization: This process determines the resources and actions that users are permitted to access. It typically occurs post-authentication and involves user permissions and control policies. Authorization mechanisms come in various forms, the most common of which are:
電子郵件和密碼:普遍的方法是使用者輸入電子郵件地址和密碼來存取應用程序,然後在每次會話時重新輸入此資訊。代碼第三方身份驗證:與簡訊身份驗證類似,用戶從行動應用程式接收代碼以獲取存取權限。存取的資源和操作。它通常發生在身份驗證後,涉及使用者權限和控制策略。授權機制有多種形式,最常見的是:
- Access Control Lists (ACLs): These systems assign permissions or deny access based on the user's authorization level.
- Data Access: Databases can be classified according to their sensitivity levels, enabling administrators to grant varying levels of access to specific users. For example, employees may be restricted to internal data, while managers can access confidential data.
Authentication vs. Authorization
存取控制清單 (ACL):這些系統根據使用者的授權等級分配權限或拒絕存取。例如,員工可能僅限於內部數據,而經理可以存取機密數據。
In C# JWT, authentication pertains to credential verification through ID tokens, while authorization focuses on granting or denying permissions through access tokens. Authentication is directly visible to users, whereas authorization remains concealed.
在 C# JWT 中,身份驗證涉及透過 ID 令牌進行憑證驗證,而授權則專注於透過存取權杖授予或拒絕權限。身份驗證對使用者直接可見,而授權則保持隱藏。
JSON Web Tokens (JWTs) and Their Applications in Modern Web Development
JSON Web 令牌 (JWT) 及其在現代 Web 開發中的應用
JSON Web Tokens (JWTs) have become a ubiquitous standard for safeguarding data exchanged between parties. They encapsulate encoded claims in a specific JSON format, facilitating data sharing. The use of JWTs offers numerous advantages:
JSON Web 令牌 (JWT) 已成為保護各方之間交換資料的普遍標準。它們以特定的 JSON 格式封裝編碼的聲明,從而促進資料共享。使用 JWT 具有許多優勢:
- Resource Conservation: JWTs are generated on the server and distributed to clients, who then submit them with requests. This approach conserves database space and eliminates the need for data lookups, expediting JWT verification.
- Enhanced Security: A JWT typically comprises three components: Header, Payload, and Signature. The Header specifies the token type (JWT) and its signing algorithm. The Payload contains claims, represented as a JSON string. The Signature ensures the token's integrity by cryptographically vouching for the Payload and Header. This signature is known only to the issuer and recipient, preventing unauthorized token alteration.
JWTs are widely employed for authentication in modern web applications. Typically, the server verifies the signature of a JWT and confirms the trustworthiness of its Payload. JWTs can also be utilized for application authorization, enabling users to prove their identity and access required resources.
資源節約:JWT 在伺服器上產生並分發給客戶端,然後客戶端透過請求提交它們。這種方法節省了資料庫空間並消除了資料查找的需要,從而加快了 JWT 驗證。標頭指定令牌類型 (JWT) 及其簽章演算法。有效負載包含聲明,表示為 JSON 字串。簽章透過加密方式保證有效負載和標頭來確保令牌的完整性。此簽章只有頒發者和接收者知道,從而防止未經授權的代幣變更。通常,伺服器驗證 JWT 的簽章並確認其有效負載的可信度。 JWT 還可以用於應用程式授權,使用戶能夠證明自己的身分並存取所需的資源。
Decoding JWTs in C# for Authentication and Authorization
在 C# 中解碼 JWT 以進行身份驗證和授權
Numerous developers leverage JWTs in C# for authentication and authorization purposes. C# offers a comprehensive range of libraries for creating and validating JWTs, facilitating seamless encoding and decoding.
許多開發人員利用 C# 中的 JWT 進行身份驗證和授權。 C# 提供了一系列用於建立和驗證 JWT 的全面函式庫,從而促進無縫編碼和解碼。
JWT Encoding:
JWT 編碼:
- Select an appropriate library for your project.
- Generate the Header, which specifies the token type and signing algorithm.
- Create the Payload, which encapsulates claims as a JSON string.
- Employ the library's built-in functions to generate a signature using the Header and Payload.
- Concatenate the Header, Payload, and Signature to form the JWT.
JWT Decoding:
為您的專案選擇合適的函式庫。 、有效負載和簽名以形成JWT.JWT 解碼:
- Use the library to parse the JWT string into its Header, Payload, and Signature components.
- Verify the Signature by comparing it to the Header and Payload using the library's validation methods.
- Decode the Payload to extract user-specific claims, such as ID or permissions.
Final Reflections
使用該庫將JWT 字串解析為其標頭、有效負載和簽名組件。 ID 或權限.最後的思考
C# JWT significantly enhances authorization and authentication mechanisms in software applications. Its simplicity and security streamline workflows, ultimately bolstering software performance and safeguarding against malicious threats.
C# JWT 顯著增強了軟體應用程式中的授權和身份驗證機制。其簡單性和安全性簡化了工作流程,最終增強了軟體效能並防範惡意威脅。
As organizations navigate the digital realm, embracing C# JWT technology empowers them to decode JWTs seamlessly and strengthen their security practices. This transformative approach not only protects sensitive data but also fuels innovation within the enterprise landscape.
隨著組織在數位領域中探索,採用 C# JWT 技術使他們能夠無縫解碼 JWT 並加強其安全實踐。這種變革性方法不僅可以保護敏感數據,還可以促進企業環境中的創新。
免責聲明:info@kdj.com
The information provided is not trading advice. kdj.com does not assume any responsibility for any investments made based on the information provided in this article. Cryptocurrencies are highly volatile and it is highly recommended that you invest with caution after thorough research!
If you believe that the content used on this website infringes your copyright, please contact us immediately (info@kdj.com) and we will delete it promptly.
-

-

-
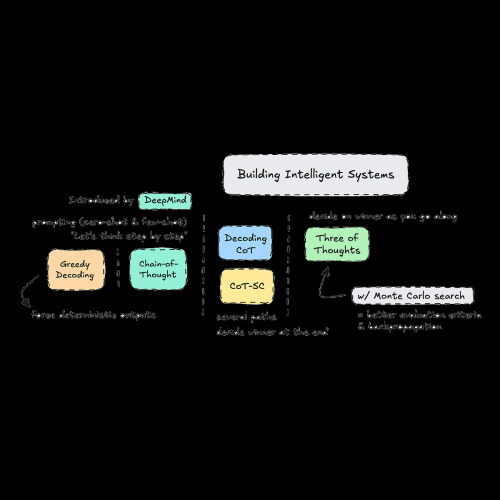
- 高階即時工程:思想鏈 (CoT)
- 2024-12-24 00:45:02
- 比較不同的推理技術
-

-
- 比特幣主導地位的看跌蝙蝠模式顯示山寨幣看漲階段
- 2024-12-24 00:45:02
- 最新的市場數據指出了比特幣在加密貨幣市場中的主導地位(BTC.d)的一個值得注意的發展。
-

-

-

-

- LCX交易所透過特別的聖誕代幣上市為加密世界帶來節日歡樂
- 2024-12-24 00:45:02
- 這個假期,LCX 透過特別的聖誕節代幣上市,為加密世界帶來節日的歡樂!




































