|
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
拉撒路集團是朝鮮相關的網絡犯罪集團,試圖黑客網絡聯合創始人肯尼·李(Kenny Li)。襲擊是由

A North Korea-affiliated cybercrime syndicate, known as Lazarus Group, attempted to scam Manta Network co-founder Kenny Li in a new phishing attempt.
朝鮮附屬的網絡犯罪集團被稱為拉撒路集團(Lazarus Group),試圖在新的網絡釣魚嘗試中騙曼塔網絡聯合創始人肯尼·李(Kenny Li)。
According to a recent report by TokenPost, the hackers contacted Li on Telegram, posing as a trusted contact who had arranged a Zoom meeting on April 17.
根據Tokenpost的最新報告,黑客在Telegram上與Li聯繫,認為是一個值得信賴的聯繫人,他於4月17日安排了Zoom會議。
During the call, Li noticed several strange prompts, including a request for camera access and a script file download, which raised his suspicions. As a result, he deleted their messages and left the meeting, only to discover later that the contact had blocked him.
在通話中,李注意到了幾個奇怪的提示,包括訪問攝像機的請求和腳本文件下載,這引起了他的懷疑。結果,他刪除了他們的信息並離開了會議,只是發現接觸阻止了他。
This experience highlights a growing trend of Zoom-based attacks against members of the crypto community, which have been linked by cybersecurity experts to the Lazarus Group, who have been exploiting vulnerabilities in Web3 infrastructure.
這種經歷強調了對加密社區成員的基於變焦的攻擊的日益增長的趨勢,這些攻擊已由網絡安全專家與Lazarus集團聯繫起來,Lazarus集團一直在利用Web3基礎架構中的漏洞。
How Lazarus Exploits Zoom for Crypto Scams
拉撒路如何利用Zoom進行加密騙局
The attack on Li involved a fake Zoom call with pre-recorded footage from previous meetings, that was probably obtained by compromising team members’s email accounts. The audio was not working and familiar faces were shown, mimicking a legitimate meeting, before a prompt to download a script file appeared.
對李的攻擊涉及一個假縮放電話,其中包括先前會議的預錄錄像,這可能是由於損害團隊成員的電子郵件帳戶而獲得的。在提示下載腳本文件之前,音頻沒有工作,並顯示了熟悉的面孔,模仿了合法的會議。
This tactic is similar to what has been previously reported about Zoom scams. For instance, SlowMist conducted an investigation last year that found hackers were using fake Zoom interfaces to trick users to download malware. These malicious files steal system data, browser cookies and cryptocurrency wallet credentials and send them to the remote server of the attackers.
這種策略類似於以前報導的有關變焦騙局的策略。例如,Slowmist去年進行了一項調查,發現黑客正在使用假縮放界面來欺騙用戶下載惡意軟件。這些惡意文件竊取系統數據,瀏覽器cookie和加密貨幣錢包憑據,並將其發送到攻擊者的遠程服務器。
In another instance, a user from Vow | ContributionDAO had a nearly identical experience on April 18, when an attacker, pretending to be part of a blockchain team, demanded a specific Zoom link. However, when the user suggested switching to Google Meet, the attackers disappeared.
在另一種情況下,來自Vow的用戶|貢獻者在4月18日的經驗幾乎相同,當時一名攻擊者假裝是區塊鏈團隊的一部分,要求有特定的變焦鏈接。但是,當用戶建議切換到Google見面時,攻擊者消失了。
As these attacks become increasingly sophisticated, members of the crypto community are raising alarm. These scams can become very convincing when they are made using deepfake technology or pre-recorded footage.
隨著這些攻擊變得越來越複雜,加密社區的成員正在引起警報。當使用Deepfake技術或預錄錄像製作時,這些騙局可能會變得非常令人信服。
KiloEx Recovers $7.5M After Separate Exploit
Kiloex單獨利用後恢復了750萬美元
In a separate development, decentralized exchange KiloEx has recovered $7.5 million after being hacked.
在另一個發展中,分散的交易所Kiloex被黑客入侵後已收回了750萬美元。
The DeFi protocol announced on Wednesday that the attacker returned the funds, stolen four days earlier, after they reached an agreement on a bounty deal.
DEFI協議週三宣布,襲擊者在達成賞金協議的協議後,在四天前被盜的資金退還了資金。
The exploit was due to a manipulated price oracle, a known vulnerability of decentralized finance platforms. KiloEx had enlisted the help of several cybersecurity firms, including SlowMist and Sherlock to trace the attack.
漏洞利用是由於價格甲骨文的操縱,這是分散融資平台的已知漏洞。 Kiloex邀請了幾家網絡安全公司的幫助,包括Slowmist和Sherlock來追踪襲擊。
After the exploit, KiloEx temporarily suspended operations and is still deciding whether to pursue legal action against the hacker. The incident also serves as a stark reminder that vulnerabilities in smart contracts and oracles remain prime targets for cybercriminals in the DeFi sector.
漏洞利用後,Kiloex暫時暫停了行動,並且仍在決定是否針對黑客採取法律訴訟。該事件還提醒人們,智能合約和甲骨文中的脆弱性仍然是Defi行業網絡犯罪分子的主要目標。
免責聲明:info@kdj.com
所提供的資訊並非交易建議。 kDJ.com對任何基於本文提供的資訊進行的投資不承擔任何責任。加密貨幣波動性較大,建議您充分研究後謹慎投資!
如果您認為本網站使用的內容侵犯了您的版權,請立即聯絡我們(info@kdj.com),我們將及時刪除。
-

- 不變的(IMX)代幣價格跳躍44%
- 2025-04-23 16:35:12
- 加密貨幣市場令人震驚,遊戲平台的本地代幣不可變動(IMX)不可變的本地代幣,正以低調的44%的價格漲幅領先於收費。
-

- 這句話“漲潮升起所有船”完美地捕捉了加密貨幣市場的現狀
- 2025-04-23 16:35:12
- 這句話“漲潮升起所有的船”,完美地捕捉了加密貨幣市場的當前狀態,因為比特幣的崛起使山寨幣越來越高。
-

- Sui Crypto增長了近32%,維持了上一交易力的積極勢頭。
- 2025-04-23 16:30:13
- 根據Crypto.news的數據,SUI(SUI)在過去24小時的交易中增長了31.8%。
-

- 罕見的兩便士件今天將在拍賣會上售價高達400英鎊
- 2025-04-23 16:30:13
- 今天的拍賣會將一件罕見的兩便士作品在拍賣會上最高可達400英鎊 - 並敦促英國人檢查他們的變化,以防萬一。
-

- HBAR價格目標0.382斐波那契水平為關鍵突破點
- 2025-04-23 16:25:12
- HBAR的價格正在增長強勁的看漲勢頭,在過去24小時內上漲了近8%,以0.1835美元的價格交易。
-

-

-

-

- 比特幣(BTC)超過$ 93,000,吸引了投資者的期望
- 2025-04-23 16:15:12
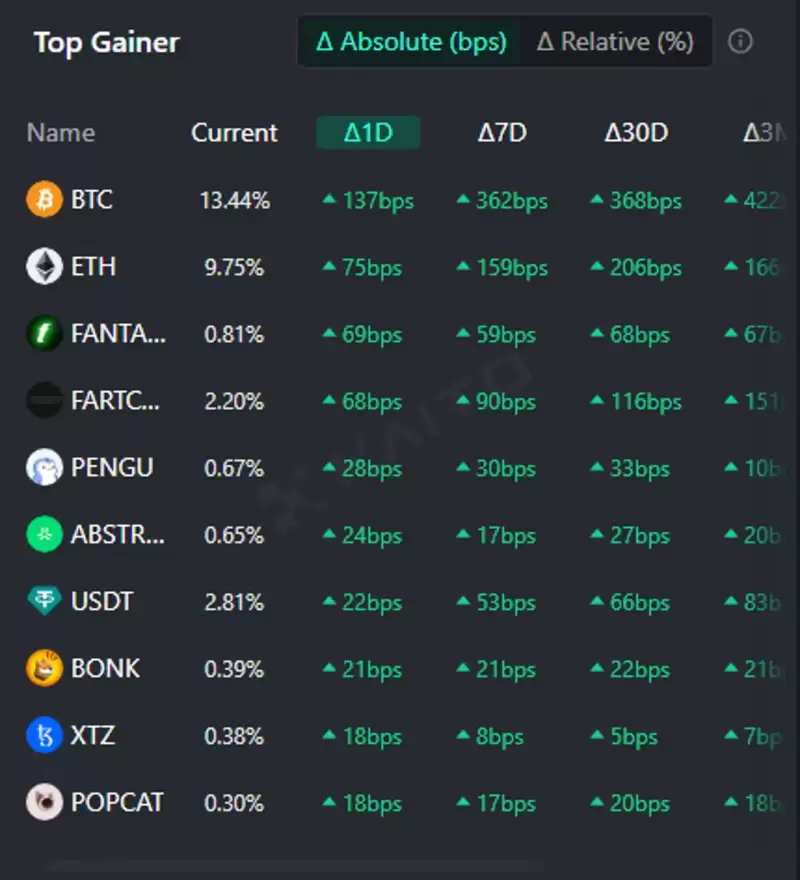
- 根據代幣思維的最高獲取者(量化特定令牌在加密貨幣市場中的影響的度量)