-
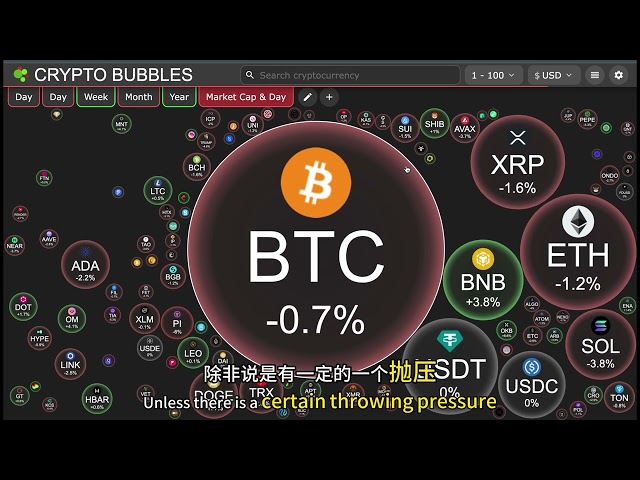
 Bitcoin
Bitcoin $83,267.6339
-0.22% -
 Ethereum
Ethereum $1,910.4421
0.59% -
 Tether USDt
Tether USDt $0.9999
-0.02% -
 XRP
XRP $2.3289
-0.69% -
 BNB
BNB $637.3734
6.38% -
 Solana
Solana $128.8563
-2.95% -
 USDC
USDC $1.0000
0.01% -
 Dogecoin
Dogecoin $0.1732
1.34% -
 Cardano
Cardano $0.7206
-0.36% -
 TRON
TRON $0.2147
-0.56% -
 Pi
Pi $1.3599
-6.77% -
 UNUS SED LEO
UNUS SED LEO $9.8297
0.05% -
 Chainlink
Chainlink $13.7729
-0.67% -
 Toncoin
Toncoin $3.3994
-0.35% -
 Stellar
Stellar $0.2709
0.69% -
 Hedera
Hedera $0.1899
0.68% -
 Avalanche
Avalanche $18.6247
-0.62% -
 Shiba Inu
Shiba Inu $0.0...01309
1.75% -
 Sui
Sui $2.2834
-0.20% -
 Litecoin
Litecoin $93.4414
3.24% -
 Polkadot
Polkadot $4.3758
2.99% -
 MANTRA
MANTRA $6.8177
3.23% -
 Bitcoin Cash
Bitcoin Cash $335.6751
1.56% -
 Ethena USDe
Ethena USDe $0.9996
-0.02% -
 Dai
Dai $1.0000
-0.02% -
 Bitget Token
Bitget Token $4.4428
0.50% -
 Hyperliquid
Hyperliquid $13.9667
3.87% -
 Monero
Monero $209.4895
-1.24% -
 Uniswap
Uniswap $6.2429
1.46% -
 Aptos
Aptos $5.3667
2.10%
How to protect a Dogecoin wallet address from hacker attacks?
Safeguarding your Dogecoin requires a multi-pronged approach: use a strong password, secure your seed phrase, update wallet software regularly, enable 2FA, and be vigilant against phishing scams.
Mar 12, 2025 at 02:55 pm

Key Points:
- Understanding Dogecoin Wallet Vulnerabilities: Dogecoin wallets, like all cryptocurrency wallets, are susceptible to various attack vectors. Understanding these vulnerabilities is the first step towards effective protection.
- Choosing a Secure Wallet Type: Different wallet types offer varying levels of security. Hardware wallets generally provide the strongest protection.
- Strong Password and Seed Phrase Management: Robust passwords and secure seed phrase storage are paramount to preventing unauthorized access.
- Software Updates and Security Patches: Keeping your wallet software up-to-date is crucial to mitigating newly discovered vulnerabilities.
- Recognizing and Avoiding Phishing Scams: Phishing attempts are a common attack vector. Learning to identify and avoid these scams is vital.
- Two-Factor Authentication (2FA): Implementing 2FA adds an extra layer of security to your account.
- Regular Security Audits: Periodically reviewing your security practices ensures ongoing protection.
How to Protect a Dogecoin Wallet Address from Hacker Attacks?
Protecting your Dogecoin wallet address from hacker attacks requires a multi-layered approach focusing on both software and user practices. The inherent value of Dogecoin, like any cryptocurrency, makes it a target for malicious actors. Therefore, proactive security measures are essential.
Understanding Dogecoin Wallet Vulnerabilities:
Dogecoin wallets, whether software or hardware-based, can be vulnerable to various attacks. These include phishing scams designed to steal your login credentials or seed phrase, malware that infects your computer and steals your private keys, and exploits targeting vulnerabilities in the wallet software itself. Understanding these threats is the first crucial step in protecting your funds.
Choosing a Secure Wallet Type:
The type of wallet you choose significantly impacts its security. Hardware wallets, like Ledger or Trezor, are considered the most secure option as they store your private keys offline, making them significantly less vulnerable to online attacks. Software wallets, while convenient, are more susceptible to malware and online attacks. Paper wallets, while offering offline security, require meticulous care to prevent loss or damage.
Strong Password and Seed Phrase Management:
A strong, unique password is essential. Avoid easily guessable passwords and utilize a password manager to generate and store complex passwords securely. Your seed phrase is the ultimate key to your Dogecoin; treat it like a highly sensitive document. Never share it with anyone, and store it offline in a secure and physically protected location. Multiple backups in different secure locations are recommended.
Software Updates and Security Patches:
Regularly update your wallet software. Developers frequently release updates that patch security vulnerabilities. Failing to update leaves your wallet susceptible to known exploits that malicious actors could use to gain access. Check for updates frequently, and install them immediately.
Recognizing and Avoiding Phishing Scams:
Phishing scams are a common attack vector. These scams often involve fake websites or emails that mimic legitimate Dogecoin services, attempting to trick you into revealing your login credentials or seed phrase. Be wary of unsolicited emails or messages requesting your login details or seed phrase. Always verify the authenticity of websites and emails before entering any sensitive information.
Two-Factor Authentication (2FA):
Enable two-factor authentication (2FA) whenever possible. 2FA adds an extra layer of security by requiring a second verification method, such as a code from your phone or email, in addition to your password. This makes it significantly harder for hackers to access your account, even if they obtain your password.
Regular Security Audits:
Periodically review your security practices. This includes checking your password strength, ensuring your seed phrase is safely stored, verifying that your wallet software is up-to-date, and reviewing your online activity for any suspicious behavior. Regular audits help identify and address potential vulnerabilities before they can be exploited.
Using reputable exchanges:
Choose reputable and well-established cryptocurrency exchanges to buy, sell, and store your Dogecoin. Look for exchanges with strong security measures in place, including 2FA and robust security protocols.
Educate yourself on cryptocurrency security best practices:
Continuously learn about the latest security threats and best practices to protect your cryptocurrency. Stay updated on news and information related to cryptocurrency security to remain ahead of potential attacks.
Common Questions:
Q: What happens if my Dogecoin wallet is hacked?
A: If your Dogecoin wallet is hacked, your Dogecoin could be stolen. The extent of the loss depends on the amount of Dogecoin in your wallet. Reporting the incident to the appropriate authorities and the exchange (if applicable) is crucial.
Q: Can I recover my Dogecoin if my wallet is compromised?
A: Recovery depends on the type of wallet and the nature of the compromise. If you have a backup of your seed phrase and it hasn't been compromised, you might be able to recover your Dogecoin by restoring your wallet. However, if your seed phrase is lost or compromised, recovery is typically impossible.
Q: Are hardware wallets completely secure?
A: While hardware wallets are significantly more secure than software wallets, they are not completely immune to attacks. Physical theft or sophisticated attacks targeting the hardware itself are still potential risks.
Q: What should I do if I suspect a phishing attempt?
A: Do not click on any links or provide any personal information. Report the suspicious email or website to the appropriate authorities and the platform involved.
Q: How often should I update my wallet software?
A: Update your wallet software as soon as updates are released. Check for updates regularly, as security vulnerabilities can be discovered and patched at any time.
Disclaimer:info@kdj.com
The information provided is not trading advice. kdj.com does not assume any responsibility for any investments made based on the information provided in this article. Cryptocurrencies are highly volatile and it is highly recommended that you invest with caution after thorough research!
If you believe that the content used on this website infringes your copyright, please contact us immediately (info@kdj.com) and we will delete it promptly.
- Solana (SOL) Cup-and-Handle Pattern Hints at Breakout Toward $3,800
- 2025-03-17 19:10:57
- IntelMarkets (INTL) Price Could See Growth Following the Potential Approval of an XRP ETF Before May
- 2025-03-17 19:10:57
- Cardano (ADA) whales are making better choices as they shift a portion of their holdings into Mutuum Finance (MUTM)
- 2025-03-17 19:10:57
- The Mustard Seed: A Thesis That Bitcoin Will Reach $10M per Coin by 2035
- 2025-03-17 19:10:57
- The U.S. pro-crypto pivot under President Donald Trump may come at a hefty price, one European Central Bank Governing Council member has warned.
- 2025-03-17 19:10:57
- 21Shares to Liquidate Its Bitcoin and Ethereum Futures-Tracking ETFs
- 2025-03-17 19:10:57
Related knowledge

How do I use multi-signature on my hardware wallet on my Ledger device?
Mar 17,2025 at 01:36am
Key Points:Multi-signature (multisig) wallets enhance security by requiring multiple approvals for transactions.Ledger devices support multisig through compatible wallets and specific configurations.Setting up multisig involves generating multiple keys and configuring the wallet accordingly.Understanding the intricacies of threshold signatures is crucia...

How do I use staking on my Ledger device?
Mar 17,2025 at 12:41pm
Key Points:Ledger devices offer a secure way to stake various cryptocurrencies. However, the process varies depending on the coin and the chosen staking provider.You'll generally need a Ledger Live account and the correct application installed on your device.Understanding the risks associated with staking, such as potential slashing, is crucial before p...

How do I export my private keys from my Ledger device?
Mar 17,2025 at 02:30pm
Key Points:Ledger devices do not directly "export" private keys in the traditional sense. The private keys are never revealed or accessible outside the secure element of the device.You can access and use your private keys indirectly through the device's interaction with your chosen wallet software.The process involves using your Ledger device with compa...

How do I fix a connection issue with my Ledger device?
Mar 16,2025 at 08:26am
Key Points:Troubleshooting Ledger connection issues often involves checking the device's charge, the USB cable, and the computer's USB ports.Software updates on both the Ledger device and its associated computer applications are crucial for optimal functionality and connection stability.Correctly installing the Ledger Live application and ensuring its c...

How do I use a password manager on my Ledger Nano S/X?
Mar 16,2025 at 09:25pm
Key Points:Ledger devices do not directly integrate with password managers. Their security model prioritizes offline key storage.You can use a password manager for your computer passwords, but not for your Ledger device seed phrase or PIN.Storing your Ledger PIN in a password manager is highly discouraged due to security risks.Strong, unique PINs and se...

How do I check the authenticity of my Ledger device?
Mar 17,2025 at 02:45pm
Key Points:Verifying your Ledger device's authenticity involves checking for several security features both on the device itself and through Ledger's official website.The packaging and the device itself contain unique identifiers that can be verified.Ledger's website provides tools to confirm the authenticity of your device and its bootloader.Understand...

How do I use multi-signature on my hardware wallet on my Ledger device?
Mar 17,2025 at 01:36am
Key Points:Multi-signature (multisig) wallets enhance security by requiring multiple approvals for transactions.Ledger devices support multisig through compatible wallets and specific configurations.Setting up multisig involves generating multiple keys and configuring the wallet accordingly.Understanding the intricacies of threshold signatures is crucia...

How do I use staking on my Ledger device?
Mar 17,2025 at 12:41pm
Key Points:Ledger devices offer a secure way to stake various cryptocurrencies. However, the process varies depending on the coin and the chosen staking provider.You'll generally need a Ledger Live account and the correct application installed on your device.Understanding the risks associated with staking, such as potential slashing, is crucial before p...

How do I export my private keys from my Ledger device?
Mar 17,2025 at 02:30pm
Key Points:Ledger devices do not directly "export" private keys in the traditional sense. The private keys are never revealed or accessible outside the secure element of the device.You can access and use your private keys indirectly through the device's interaction with your chosen wallet software.The process involves using your Ledger device with compa...

How do I fix a connection issue with my Ledger device?
Mar 16,2025 at 08:26am
Key Points:Troubleshooting Ledger connection issues often involves checking the device's charge, the USB cable, and the computer's USB ports.Software updates on both the Ledger device and its associated computer applications are crucial for optimal functionality and connection stability.Correctly installing the Ledger Live application and ensuring its c...

How do I use a password manager on my Ledger Nano S/X?
Mar 16,2025 at 09:25pm
Key Points:Ledger devices do not directly integrate with password managers. Their security model prioritizes offline key storage.You can use a password manager for your computer passwords, but not for your Ledger device seed phrase or PIN.Storing your Ledger PIN in a password manager is highly discouraged due to security risks.Strong, unique PINs and se...

How do I check the authenticity of my Ledger device?
Mar 17,2025 at 02:45pm
Key Points:Verifying your Ledger device's authenticity involves checking for several security features both on the device itself and through Ledger's official website.The packaging and the device itself contain unique identifiers that can be verified.Ledger's website provides tools to confirm the authenticity of your device and its bootloader.Understand...
See all articles