-
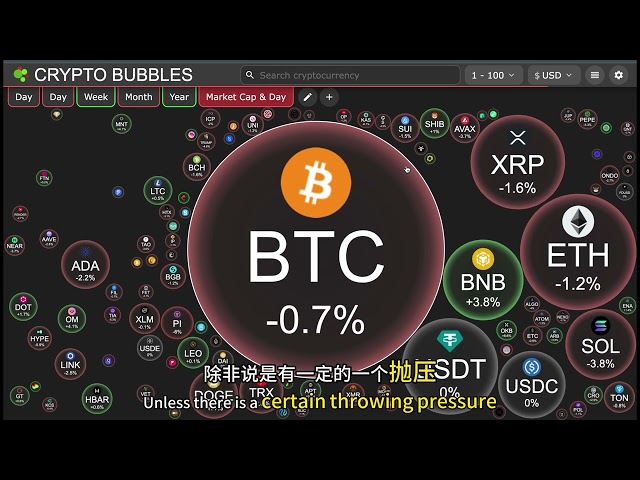
 Bitcoin
Bitcoin $83,267.6339
-0.22% -
 Ethereum
Ethereum $1,910.4421
0.59% -
 Tether USDt
Tether USDt $0.9999
-0.02% -
 XRP
XRP $2.3289
-0.69% -
 BNB
BNB $637.3734
6.38% -
 Solana
Solana $128.8563
-2.95% -
 USDC
USDC $1.0000
0.01% -
 Dogecoin
Dogecoin $0.1732
1.34% -
 Cardano
Cardano $0.7206
-0.36% -
 TRON
TRON $0.2147
-0.56% -
 Pi
Pi $1.3599
-6.77% -
 UNUS SED LEO
UNUS SED LEO $9.8297
0.05% -
 Chainlink
Chainlink $13.7729
-0.67% -
 Toncoin
Toncoin $3.3994
-0.35% -
 Stellar
Stellar $0.2709
0.69% -
 Hedera
Hedera $0.1899
0.68% -
 Avalanche
Avalanche $18.6247
-0.62% -
 Shiba Inu
Shiba Inu $0.0...01309
1.75% -
 Sui
Sui $2.2834
-0.20% -
 Litecoin
Litecoin $93.4414
3.24% -
 Polkadot
Polkadot $4.3758
2.99% -
 MANTRA
MANTRA $6.8177
3.23% -
 Bitcoin Cash
Bitcoin Cash $335.6751
1.56% -
 Ethena USDe
Ethena USDe $0.9996
-0.02% -
 Dai
Dai $1.0000
-0.02% -
 Bitget Token
Bitget Token $4.4428
0.50% -
 Hyperliquid
Hyperliquid $13.9667
3.87% -
 Monero
Monero $209.4895
-1.24% -
 Uniswap
Uniswap $6.2429
1.46% -
 Aptos
Aptos $5.3667
2.10%
How secure is the Uquid Coin (UQC) network?
Uquid Coin's robust security measures, including Proof-of-Work consensus, advanced encryption, and a decentralized network structure, reinforce its resilience against malicious attacks and unauthorized access.
Dec 30, 2024 at 05:44 am

Key Points:
- Uquid Coin leverages Proof-of-Work consensus mechanism for robust network security.
- Advanced encryption algorithms protect blockchain data and transactions.
- Decentralized network structure enhances resistance to malicious attacks.
- Reputable custodians ensure secure asset storage and management.
- Regular security audits and ongoing security enhancements reinforce network integrity.
In-Depth Analysis:
1. Proof-of-Work Consensus Mechanism:
Uquid Coin employs the Proof-of-Work (PoW) consensus mechanism, widely adopted by established blockchains like Bitcoin. PoW requires miners to solve complex computational puzzles to validate transactions and add new blocks to the blockchain. This process consumes significant computational power, making it costly and challenging for malicious actors to attack or manipulate the network.
2. Advanced Encryption Algorithms:
The Uquid Coin blockchain utilizes advanced encryption algorithms such as AES-256 to safeguard data and transactions. AES-256 is a highly secure cipher widely employed in industries like banking and government. It protects blockchain data, including transaction details, wallet addresses, and other sensitive information, from unauthorized access.
3. Decentralized Network Structure:
Uquid Coin operates on a decentralized network, meaning it is not controlled by a single entity. The blockchain is distributed across a vast network of nodes, ensuring data integrity and preventing malicious actors from compromising the entire system. This decentralization makes the network more resistant to attacks, as any attempt to alter the blockchain would require corrupting a majority of the nodes.
4. Reputable Custodians:
Uquid Coin has partnered with reputable custodians to provide secure storage and management of user assets. These custodians are regulated entities subject to strict security protocols and compliance standards. They employ multi-layered security measures, including cold storage, two-factor authentication, and ongoing monitoring, to safeguard user funds.
5. Regular Security Audits:
Uquid Coin undergoes regular security audits conducted by independent third-party experts. These audits thoroughly assess the network's security architecture, codebase, and operational practices. The findings from these audits are used to identify and address potential vulnerabilities and enhance the overall security of the network.
FAQs:
- Is Uquid Coin inherently immune to security breaches?
No blockchain network is completely immune to security breaches. However, Uquid Coin's robust security measures, including PoW consensus, advanced encryption, decentralization, reputable custodians, and regular security audits, significantly reduce the risk of successful attacks.
- What does PoW consensus contribute to Uquid Coin's security?
PoW consensus makes it computationally expensive to manipulate or attack the Uquid Coin blockchain. Miners require significant computational power to validate transactions and add new blocks, which acts as a deterrent to malicious actors.
- How does the decentralized network structure enhance Uquid Coin's security?
Decentralization eliminates single points of failure and prevents malicious actors from controlling the entire network. The blockchain data is distributed across a large number of nodes, making it more difficult for attackers to compromise the system.
- What role do custodians play in safeguarding Uquid Coin assets?
Custodians ensure the secure storage and management of user assets. They employ multiple security measures, such as cold storage and two-factor authentication, to protect against unauthorized access and theft.
- Why are regular security audits crucial for Uquid Coin?
Security audits by independent third parties provide an impartial assessment of the security architecture, codebase, and operational practices of Uquid Coin. The findings are used to identify potential vulnerabilities and improve the overall security of the network.
Disclaimer:info@kdj.com
The information provided is not trading advice. kdj.com does not assume any responsibility for any investments made based on the information provided in this article. Cryptocurrencies are highly volatile and it is highly recommended that you invest with caution after thorough research!
If you believe that the content used on this website infringes your copyright, please contact us immediately (info@kdj.com) and we will delete it promptly.
- Solana (SOL) Cup-and-Handle Pattern Hints at Breakout Toward $3,800
- 2025-03-17 19:10:57
- IntelMarkets (INTL) Price Could See Growth Following the Potential Approval of an XRP ETF Before May
- 2025-03-17 19:10:57
- Cardano (ADA) whales are making better choices as they shift a portion of their holdings into Mutuum Finance (MUTM)
- 2025-03-17 19:10:57
- The Mustard Seed: A Thesis That Bitcoin Will Reach $10M per Coin by 2035
- 2025-03-17 19:10:57
- The U.S. pro-crypto pivot under President Donald Trump may come at a hefty price, one European Central Bank Governing Council member has warned.
- 2025-03-17 19:10:57
- 21Shares to Liquidate Its Bitcoin and Ethereum Futures-Tracking ETFs
- 2025-03-17 19:10:57
Related knowledge

Which cryptocurrency websites are good for beginners?
Mar 14,2025 at 04:48pm
CoinbaseUser - friendly Interface: Coinbase offers a clean and intuitive interface that is easy for beginners to navigate. The platform is designed to be straightforward, with clear instructions for tasks like creating an account, depositing funds, and buying/selling cryptocurrencies. For example, when you log in, you are greeted with a dashboard that s...

How much will Bitcoin be worth in 2025
Mar 14,2025 at 04:23pm
Predicting the value of Bitcoin in 2025 is an extremely complex task. Bitcoin, as the pioneer of cryptocurrencies, has a price influenced by a vast array of factors, ranging from market dynamics and technological advancements to regulatory changes and global economic conditions.Market Supply and DemandLimited Supply: Bitcoin has a capped supply of 21 mi...

How to issue an ERC-20 token?
Mar 15,2025 at 04:20pm
Key Points:Understanding the prerequisites for ERC-20 token creation.Choosing the right development environment and tools.Writing the smart contract code.Compiling and deploying the smart contract to the Ethereum network.Testing the deployed token thoroughly.Listing the token on exchanges (optional).How to Issue an ERC-20 Token?Issuing an ERC-20 token i...

What are the core functions of the smart contract of ERC-20 tokens?
Mar 15,2025 at 11:10am
Key Points:ERC-20 smart contracts define the core functionality of a token, enabling transferability, balance tracking, and allowance for delegated transfers.Beyond basic token mechanics, smart contracts can incorporate features like burning, minting, and pausing token transactions.Advanced functionalities may include integration with other DeFi protoco...

What are the main functions of ERC-20 tokens?
Mar 13,2025 at 12:21am
Key Points:ERC-20 tokens are standardized tokens built on the Ethereum blockchain, enabling interoperability and ease of use.Their primary function is to represent fungible assets, meaning each token is interchangeable with any other of the same type.ERC-20 tokens facilitate various use cases, including fundraising (ICOs/IEOs), representing in-game asse...

How are ERC-20 tokens created on the Ethereum blockchain?
Mar 13,2025 at 01:30pm
Key Points:ERC-20 tokens are created by deploying a smart contract to the Ethereum blockchain.This smart contract defines the token's properties, such as name, symbol, total supply, and decimals.Several tools and platforms simplify the process, including online IDEs and dedicated token creation services.Understanding Solidity programming is crucial for ...

Which cryptocurrency websites are good for beginners?
Mar 14,2025 at 04:48pm
CoinbaseUser - friendly Interface: Coinbase offers a clean and intuitive interface that is easy for beginners to navigate. The platform is designed to be straightforward, with clear instructions for tasks like creating an account, depositing funds, and buying/selling cryptocurrencies. For example, when you log in, you are greeted with a dashboard that s...

How much will Bitcoin be worth in 2025
Mar 14,2025 at 04:23pm
Predicting the value of Bitcoin in 2025 is an extremely complex task. Bitcoin, as the pioneer of cryptocurrencies, has a price influenced by a vast array of factors, ranging from market dynamics and technological advancements to regulatory changes and global economic conditions.Market Supply and DemandLimited Supply: Bitcoin has a capped supply of 21 mi...

How to issue an ERC-20 token?
Mar 15,2025 at 04:20pm
Key Points:Understanding the prerequisites for ERC-20 token creation.Choosing the right development environment and tools.Writing the smart contract code.Compiling and deploying the smart contract to the Ethereum network.Testing the deployed token thoroughly.Listing the token on exchanges (optional).How to Issue an ERC-20 Token?Issuing an ERC-20 token i...

What are the core functions of the smart contract of ERC-20 tokens?
Mar 15,2025 at 11:10am
Key Points:ERC-20 smart contracts define the core functionality of a token, enabling transferability, balance tracking, and allowance for delegated transfers.Beyond basic token mechanics, smart contracts can incorporate features like burning, minting, and pausing token transactions.Advanced functionalities may include integration with other DeFi protoco...

What are the main functions of ERC-20 tokens?
Mar 13,2025 at 12:21am
Key Points:ERC-20 tokens are standardized tokens built on the Ethereum blockchain, enabling interoperability and ease of use.Their primary function is to represent fungible assets, meaning each token is interchangeable with any other of the same type.ERC-20 tokens facilitate various use cases, including fundraising (ICOs/IEOs), representing in-game asse...

How are ERC-20 tokens created on the Ethereum blockchain?
Mar 13,2025 at 01:30pm
Key Points:ERC-20 tokens are created by deploying a smart contract to the Ethereum blockchain.This smart contract defines the token's properties, such as name, symbol, total supply, and decimals.Several tools and platforms simplify the process, including online IDEs and dedicated token creation services.Understanding Solidity programming is crucial for ...
See all articles