-
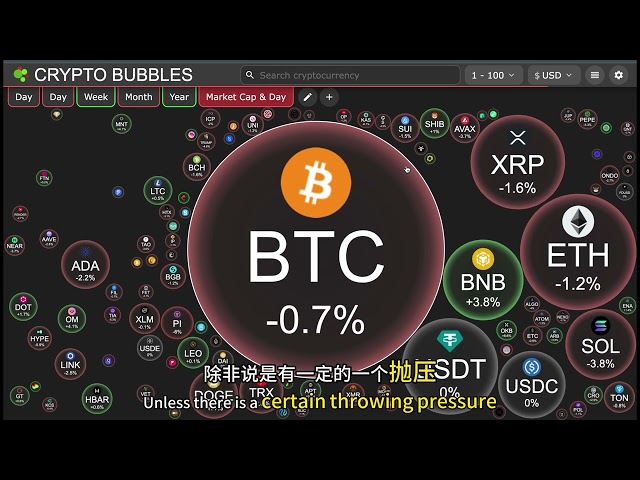
 Bitcoin
Bitcoin $83,267.6339
-0.22% -
 Ethereum
Ethereum $1,910.4421
0.59% -
 Tether USDt
Tether USDt $0.9999
-0.02% -
 XRP
XRP $2.3289
-0.69% -
 BNB
BNB $637.3734
6.38% -
 Solana
Solana $128.8563
-2.95% -
 USDC
USDC $1.0000
0.01% -
 Dogecoin
Dogecoin $0.1732
1.34% -
 Cardano
Cardano $0.7206
-0.36% -
 TRON
TRON $0.2147
-0.56% -
 Pi
Pi $1.3599
-6.77% -
 UNUS SED LEO
UNUS SED LEO $9.8297
0.05% -
 Chainlink
Chainlink $13.7729
-0.67% -
 Toncoin
Toncoin $3.3994
-0.35% -
 Stellar
Stellar $0.2709
0.69% -
 Hedera
Hedera $0.1899
0.68% -
 Avalanche
Avalanche $18.6247
-0.62% -
 Shiba Inu
Shiba Inu $0.0...01309
1.75% -
 Sui
Sui $2.2834
-0.20% -
 Litecoin
Litecoin $93.4414
3.24% -
 Polkadot
Polkadot $4.3758
2.99% -
 MANTRA
MANTRA $6.8177
3.23% -
 Bitcoin Cash
Bitcoin Cash $335.6751
1.56% -
 Ethena USDe
Ethena USDe $0.9996
-0.02% -
 Dai
Dai $1.0000
-0.02% -
 Bitget Token
Bitget Token $4.4428
0.50% -
 Hyperliquid
Hyperliquid $13.9667
3.87% -
 Monero
Monero $209.4895
-1.24% -
 Uniswap
Uniswap $6.2429
1.46% -
 Aptos
Aptos $5.3667
2.10%
What risks come from browser extensions in crypto wallets?
Balancing Convenience and Security: Browser extensions can enhance wallet functionality but demand vigilant oversight to mitigate malware, phishing, and permissions risks.
Feb 11, 2025 at 04:54 pm

Key Points:
- Browser extensions can provide convenience and additional functionality to crypto wallets.
- However, they also introduce potential security risks that users should be aware of.
- It is important to choose browser extensions from reputable sources and to be aware of the permissions they request.
- Users should also regularly check their browser extensions for suspicious activity.
Potential Risks of Browser Extensions in Crypto Wallets:
- Malware: Browser extensions can be infected with malware that can steal sensitive information, such as wallet seed phrases or private keys. This malware can be installed without the user's knowledge or consent.
- Phishing: Browser extensions can be used to create phishing websites that look identical to legitimate websites. These websites may trick users into providing their login credentials or other sensitive information.
- Keyloggers: Browser extensions can be used to install keyloggers that record every keystroke a user makes. This information can be used to steal passwords, wallet seed phrases, and other sensitive data.
- Permissions: Browser extensions often request permissions to access various parts of a user's browser, such as the ability to read and modify data on websites. These permissions can be used to steal sensitive information or to manipulate the user's browsing experience.
- Vulnerabilities: Browser extensions can contain vulnerabilities that can be exploited by hackers to gain access to a user's wallet or to steal sensitive information. These vulnerabilities can be patched by the extension developer, but it is important to keep browser extensions up to date.
Steps to Minimize Risks:
- Choose Extensions from Reputable Sources: Only install browser extensions from reputable sources, such as the Chrome Web Store or the Firefox Add-ons Store.
- Be Aware of Permissions: Carefully review the permissions requested by a browser extension before installing it. If you are unsure about a permission, do not install the extension.
- Disable Unused Extensions: Disable any browser extensions that you are not actively using. This will reduce the risk of an extension being exploited by a hacker.
- Regularly Check for Suspicious Activity: Regularly check your browser extensions for suspicious activity, such as changes to the extension's appearance or behavior. If you notice anything suspicious, disable the extension and contact the extension developer.
FAQs:
Q: Can browser extensions access my private keys?
A: Yes, browser extensions can access your private keys if they have been granted permission to do so. It is important to only grant permissions to extensions from reputable sources.
Q: How can I tell if a browser extension is malicious?
A: Look for signs of suspicious activity, such as changes to the extension's appearance or behavior. You can also check the extension's reviews to see if other users have reported any problems.
Q: What should I do if I suspect a browser extension is malicious?
A: Disable the extension immediately and contact the extension developer. You may also want to run a malware scan on your computer.
Q: Can I use a hardware wallet to protect my crypto from browser extension risks?
A: Yes, hardware wallets are a good way to protect your crypto from browser extension risks. Hardware wallets store your private keys offline, making them inaccessible to hackers.
Disclaimer:info@kdj.com
The information provided is not trading advice. kdj.com does not assume any responsibility for any investments made based on the information provided in this article. Cryptocurrencies are highly volatile and it is highly recommended that you invest with caution after thorough research!
If you believe that the content used on this website infringes your copyright, please contact us immediately (info@kdj.com) and we will delete it promptly.
- Solana (SOL) Cup-and-Handle Pattern Hints at Breakout Toward $3,800
- 2025-03-17 19:10:57
- IntelMarkets (INTL) Price Could See Growth Following the Potential Approval of an XRP ETF Before May
- 2025-03-17 19:10:57
- Cardano (ADA) whales are making better choices as they shift a portion of their holdings into Mutuum Finance (MUTM)
- 2025-03-17 19:10:57
- The Mustard Seed: A Thesis That Bitcoin Will Reach $10M per Coin by 2035
- 2025-03-17 19:10:57
- The U.S. pro-crypto pivot under President Donald Trump may come at a hefty price, one European Central Bank Governing Council member has warned.
- 2025-03-17 19:10:57
- 21Shares to Liquidate Its Bitcoin and Ethereum Futures-Tracking ETFs
- 2025-03-17 19:10:57
Related knowledge

What is Ethereum’s Slashing mechanism and how to punish malicious behavior?
Feb 20,2025 at 03:08am
Key PointsOverview of slashingDifferent types of slashing in EthereumIncentives and consequences of slashingIdentifying and reporting slashed validatorsOngoing discussions and potential improvementsEthereum's Slashing Mechanism: Punishing Malicious BehaviorEthereum's slashing mechanism is an essential tool for ensuring network security and punishing mal...

What is the verifier node of Ethereum and how to become a verifier?
Feb 19,2025 at 06:00pm
The Verifier Node of Ethereum: A Comprehensive GuideKey Points:What is a Verifier Node?How to Become a Verifier NodeResponsibilities and Rewards of a Verifier NodeMinimum Requirements for Becoming a Verifier NodePotential Difficulties in Running a Verifier Node1. What is a Verifier Node?A Verifier Node is an independent entity on the Ethereum network th...

What is Ethereum’s staking, and how to participate and earn money?
Feb 19,2025 at 04:37pm
Key Points:Understanding Ethereum's Staking MechanismSteps to Participate in StakingBenefits and Rewards of StakingSecurity and Risk ConsiderationsTechnical Requirements and Hardware OptionsPotential Challenges and Troubleshooting TipsFAQs on Ethereum StakingWhat is Ethereum's Staking?Proof-of-Stake (PoS) is a consensus mechanism used in blockchain netw...

What is Ethereum’s DAO (Decentralized Autonomous Organization) and how does it work?
Feb 20,2025 at 03:12am
Key PointsDefinition and Structure of a DAOGovernance and Decision-Making in DAOsBenefits and Use Cases of DAOsChallenges and Limitations of DAOsWhat is Ethereum's DAO (Decentralized Autonomous Organization) and How Does It Work?Definition and Structure of a DAOA Decentralized Autonomous Organization (DAO) is an innovative governance and management fram...

What is Ethereum's multi-signature wallet and how to improve security?
Feb 20,2025 at 02:18pm
Key Points:Understanding the Concept of a Multi-Signature WalletBenefits and Drawbacks of Multisig WalletsRequirements for Setting Up a Multisig WalletStep-by-Step Guide to Generating a Multisig WalletImplementing Strategies for Enhanced Security1. Understanding the Concept of a Multi-Signature WalletA multi-signature (multisig) wallet in the Ethereum e...

What is Ethereum's oracle and how to provide data for smart contracts?
Feb 21,2025 at 01:30am
Key Points:Understanding the concept of oracles in EthereumExploring different types of oraclesDetailed guide on how to provide data for smart contractsAddressing potential challenges and considerationsWhat is Ethereum's Oracle?Oracles are crucial components in the Ethereum ecosystem, enabling smart contracts to access real-world data and off-chain even...

What is Ethereum’s Slashing mechanism and how to punish malicious behavior?
Feb 20,2025 at 03:08am
Key PointsOverview of slashingDifferent types of slashing in EthereumIncentives and consequences of slashingIdentifying and reporting slashed validatorsOngoing discussions and potential improvementsEthereum's Slashing Mechanism: Punishing Malicious BehaviorEthereum's slashing mechanism is an essential tool for ensuring network security and punishing mal...

What is the verifier node of Ethereum and how to become a verifier?
Feb 19,2025 at 06:00pm
The Verifier Node of Ethereum: A Comprehensive GuideKey Points:What is a Verifier Node?How to Become a Verifier NodeResponsibilities and Rewards of a Verifier NodeMinimum Requirements for Becoming a Verifier NodePotential Difficulties in Running a Verifier Node1. What is a Verifier Node?A Verifier Node is an independent entity on the Ethereum network th...

What is Ethereum’s staking, and how to participate and earn money?
Feb 19,2025 at 04:37pm
Key Points:Understanding Ethereum's Staking MechanismSteps to Participate in StakingBenefits and Rewards of StakingSecurity and Risk ConsiderationsTechnical Requirements and Hardware OptionsPotential Challenges and Troubleshooting TipsFAQs on Ethereum StakingWhat is Ethereum's Staking?Proof-of-Stake (PoS) is a consensus mechanism used in blockchain netw...

What is Ethereum’s DAO (Decentralized Autonomous Organization) and how does it work?
Feb 20,2025 at 03:12am
Key PointsDefinition and Structure of a DAOGovernance and Decision-Making in DAOsBenefits and Use Cases of DAOsChallenges and Limitations of DAOsWhat is Ethereum's DAO (Decentralized Autonomous Organization) and How Does It Work?Definition and Structure of a DAOA Decentralized Autonomous Organization (DAO) is an innovative governance and management fram...

What is Ethereum's multi-signature wallet and how to improve security?
Feb 20,2025 at 02:18pm
Key Points:Understanding the Concept of a Multi-Signature WalletBenefits and Drawbacks of Multisig WalletsRequirements for Setting Up a Multisig WalletStep-by-Step Guide to Generating a Multisig WalletImplementing Strategies for Enhanced Security1. Understanding the Concept of a Multi-Signature WalletA multi-signature (multisig) wallet in the Ethereum e...

What is Ethereum's oracle and how to provide data for smart contracts?
Feb 21,2025 at 01:30am
Key Points:Understanding the concept of oracles in EthereumExploring different types of oraclesDetailed guide on how to provide data for smart contractsAddressing potential challenges and considerationsWhat is Ethereum's Oracle?Oracles are crucial components in the Ethereum ecosystem, enabling smart contracts to access real-world data and off-chain even...
See all articles