-
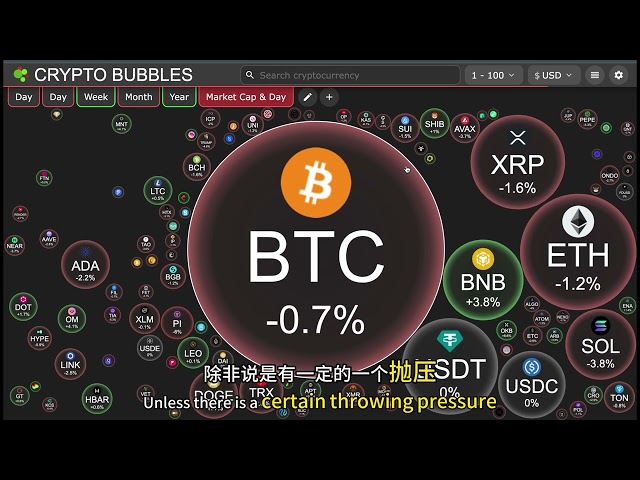
 Bitcoin
Bitcoin $83,405.1468
1.08% -
 Ethereum
Ethereum $1,912.6728
1.88% -
 Tether USDt
Tether USDt $0.9998
-0.02% -
 XRP
XRP $2.3402
1.69% -
 BNB
BNB $630.3565
5.89% -
 Solana
Solana $129.2270
-0.57% -
 USDC
USDC $0.9999
0.00% -
 Dogecoin
Dogecoin $0.1729
3.03% -
 Cardano
Cardano $0.7248
2.38% -
 TRON
TRON $0.2147
0.42% -
 Pi
Pi $1.3661
-6.43% -
 Chainlink
Chainlink $13.8271
2.04% -
 UNUS SED LEO
UNUS SED LEO $9.8262
0.10% -
 Toncoin
Toncoin $3.4413
1.84% -
 Stellar
Stellar $0.2729
3.28% -
 Hedera
Hedera $0.1916
2.99% -
 Avalanche
Avalanche $18.6675
1.25% -
 Shiba Inu
Shiba Inu $0.0...01305
2.61% -
 Sui
Sui $2.2948
2.75% -
 Litecoin
Litecoin $93.2169
4.69% -
 Polkadot
Polkadot $4.3872
4.38% -
 MANTRA
MANTRA $6.8361
4.30% -
 Bitcoin Cash
Bitcoin Cash $337.3260
3.38% -
 Ethena USDe
Ethena USDe $0.9996
-0.01% -
 Dai
Dai $1.0000
-0.01% -
 Bitget Token
Bitget Token $4.4585
2.28% -
 Hyperliquid
Hyperliquid $13.8960
3.65% -
 Monero
Monero $211.2489
0.36% -
 Uniswap
Uniswap $6.2340
3.26% -
 Aptos
Aptos $5.3849
3.93%
What is the relationship between a private key and symmetric encryption in cryptography?
Private keys are crucial for asymmetric, not symmetric, encryption. Symmetric encryption uses one key for both encryption and decryption, while asymmetric uses a public key to encrypt and a private key to decrypt, often working together for enhanced security.
Mar 13, 2025 at 06:45 pm

Key Points:
- Private keys are fundamental to asymmetric cryptography, not symmetric cryptography.
- Symmetric encryption uses a single key for both encryption and decryption.
- Asymmetric cryptography, which utilizes private keys, employs separate keys for encryption (public key) and decryption (private key).
- While seemingly unrelated at first glance, understanding the contrast highlights the distinct security models employed.
- Misunderstanding this relationship can lead to vulnerabilities in cryptographic systems.
What is the relationship between a private key and symmetric encryption in cryptography?
The relationship between a private key and symmetric encryption is primarily one of contrast rather than direct connection. Private keys are a cornerstone of asymmetric cryptography, a system fundamentally different from symmetric encryption. Symmetric encryption uses a single, secret key for both encrypting and decrypting data. Think of it like a padlock with only one key; both sender and receiver need the same key. This shared secret needs to be securely exchanged, which presents a significant challenge.
Private keys, on the other hand, exist within the realm of asymmetric or public-key cryptography. This system uses two distinct keys: a public key for encryption and a private key for decryption. The public key can be widely distributed, while the private key must remain absolutely secret. This solves the key exchange problem inherent in symmetric encryption. The analogy here is a mailbox with a slot for dropping letters (public key for encryption) and a key to access the mail inside (private key for decryption).
The core difference lies in their functionality and the security models they support. Symmetric encryption relies on the secrecy of a single key, making secure key distribution crucial. Asymmetric encryption leverages the mathematical relationship between the public and private keys, allowing for secure communication without the need to pre-share a secret key.
Let's examine a scenario where both are used together, a common practice in many secure systems. Often, a symmetric key is used for encrypting the actual data because it's significantly faster than asymmetric encryption. However, the symmetric key itself is encrypted using the recipient's public key before transmission. Only the recipient, possessing the corresponding private key, can decrypt the symmetric key and then use it to decrypt the actual data. This hybrid approach combines the speed of symmetric encryption with the secure key exchange provided by asymmetric cryptography.
Consider the following example illustrating the difference:
- Symmetric Encryption: Alice and Bob share a secret key. Alice encrypts a message using the key, and Bob decrypts it using the same key. If someone intercepts the message, they cannot decrypt it without the shared key.
- Asymmetric Encryption: Alice has a public and private key pair. Bob uses Alice's public key to encrypt a message. Only Alice, with her private key, can decrypt it. Even if someone intercepts the message and obtains Alice's public key, they cannot decrypt it without the private key.
The private key’s role is exclusively within the asymmetric system. It doesn't directly interact with or influence the mechanics of symmetric encryption. Their connection is primarily in practical implementation where they often work together to provide a robust and efficient security solution. The private key safeguards the symmetric key, ensuring only the intended recipient can access the actual data. Misunderstanding this distinction can lead to vulnerabilities. For example, relying solely on symmetric encryption without a secure key exchange mechanism can compromise the entire system.
Frequently Asked Questions:
Q: Can a private key be used for encryption?
A: Yes, a private key can be used for encryption, but this is less common than using it for decryption. This is often referred to as digital signatures, verifying the authenticity and integrity of the message. The sender encrypts a message digest (a cryptographic hash of the message) with their private key. The recipient can then verify the signature using the sender's public key.
Q: What happens if a private key is compromised?
A: If a private key is compromised, the security of the entire system reliant on that key is jeopardized. Anyone with access to the private key can decrypt messages intended for the owner of the key, and can forge signatures. This is why private key security is paramount.
Q: Is symmetric encryption more secure than asymmetric encryption?
A: Neither is inherently "more secure". The security of both depends on the implementation and the strength of the algorithms used. Symmetric encryption is generally faster, but the challenge lies in secure key exchange. Asymmetric encryption addresses this challenge but is computationally more intensive.
Q: Can I generate my own private key using a simple algorithm?
A: No. Generating strong private keys requires sophisticated cryptographic algorithms and random number generators to ensure the keys are unpredictable and resistant to attacks. Using simple algorithms would produce weak keys, easily compromised.
Q: What are some common uses of private keys in cryptocurrencies?
A: In cryptocurrencies, private keys are used to authorize transactions. Ownership of a private key proves ownership of the corresponding cryptocurrency address and allows the owner to spend the funds associated with that address. Losing your private key means losing access to your cryptocurrency.
Disclaimer:info@kdj.com
The information provided is not trading advice. kdj.com does not assume any responsibility for any investments made based on the information provided in this article. Cryptocurrencies are highly volatile and it is highly recommended that you invest with caution after thorough research!
If you believe that the content used on this website infringes your copyright, please contact us immediately (info@kdj.com) and we will delete it promptly.
- Why Is Coinbase a Good Business?
- 2025-03-17 20:25:57
- When it Comes to the Best Crypto to Invest in March 2025
- 2025-03-17 20:25:57
- Bitcoin Pepe (BPEP) Changes the Game With Technology That Could Transform Bitcoin Itself
- 2025-03-17 20:25:57
- XYZ Coin Crosses the $10 Million Mark in Its Presale Phase
- 2025-03-17 20:25:57
- Binance Expands Trade Offerings For MKR, EPIC, & These 3 Crypto
- 2025-03-17 20:25:57
- Arctic Pablo Coin ($APC) Presale: Explore the Depths of Cryptocurrency Investment
- 2025-03-17 20:25:57
Related knowledge

How do I use multi-signature on my hardware wallet on my Ledger device?
Mar 17,2025 at 01:36am
Key Points:Multi-signature (multisig) wallets enhance security by requiring multiple approvals for transactions.Ledger devices support multisig through compatible wallets and specific configurations.Setting up multisig involves generating multiple keys and configuring the wallet accordingly.Understanding the intricacies of threshold signatures is crucia...

How do I use staking on my Ledger device?
Mar 17,2025 at 12:41pm
Key Points:Ledger devices offer a secure way to stake various cryptocurrencies. However, the process varies depending on the coin and the chosen staking provider.You'll generally need a Ledger Live account and the correct application installed on your device.Understanding the risks associated with staking, such as potential slashing, is crucial before p...

How do I export my private keys from my Ledger device?
Mar 17,2025 at 02:30pm
Key Points:Ledger devices do not directly "export" private keys in the traditional sense. The private keys are never revealed or accessible outside the secure element of the device.You can access and use your private keys indirectly through the device's interaction with your chosen wallet software.The process involves using your Ledger device with compa...

How do I fix a connection issue with my Ledger device?
Mar 16,2025 at 08:26am
Key Points:Troubleshooting Ledger connection issues often involves checking the device's charge, the USB cable, and the computer's USB ports.Software updates on both the Ledger device and its associated computer applications are crucial for optimal functionality and connection stability.Correctly installing the Ledger Live application and ensuring its c...

How do I use a password manager on my Ledger Nano S/X?
Mar 16,2025 at 09:25pm
Key Points:Ledger devices do not directly integrate with password managers. Their security model prioritizes offline key storage.You can use a password manager for your computer passwords, but not for your Ledger device seed phrase or PIN.Storing your Ledger PIN in a password manager is highly discouraged due to security risks.Strong, unique PINs and se...

How do I check the authenticity of my Ledger device?
Mar 17,2025 at 02:45pm
Key Points:Verifying your Ledger device's authenticity involves checking for several security features both on the device itself and through Ledger's official website.The packaging and the device itself contain unique identifiers that can be verified.Ledger's website provides tools to confirm the authenticity of your device and its bootloader.Understand...

How do I use multi-signature on my hardware wallet on my Ledger device?
Mar 17,2025 at 01:36am
Key Points:Multi-signature (multisig) wallets enhance security by requiring multiple approvals for transactions.Ledger devices support multisig through compatible wallets and specific configurations.Setting up multisig involves generating multiple keys and configuring the wallet accordingly.Understanding the intricacies of threshold signatures is crucia...

How do I use staking on my Ledger device?
Mar 17,2025 at 12:41pm
Key Points:Ledger devices offer a secure way to stake various cryptocurrencies. However, the process varies depending on the coin and the chosen staking provider.You'll generally need a Ledger Live account and the correct application installed on your device.Understanding the risks associated with staking, such as potential slashing, is crucial before p...

How do I export my private keys from my Ledger device?
Mar 17,2025 at 02:30pm
Key Points:Ledger devices do not directly "export" private keys in the traditional sense. The private keys are never revealed or accessible outside the secure element of the device.You can access and use your private keys indirectly through the device's interaction with your chosen wallet software.The process involves using your Ledger device with compa...

How do I fix a connection issue with my Ledger device?
Mar 16,2025 at 08:26am
Key Points:Troubleshooting Ledger connection issues often involves checking the device's charge, the USB cable, and the computer's USB ports.Software updates on both the Ledger device and its associated computer applications are crucial for optimal functionality and connection stability.Correctly installing the Ledger Live application and ensuring its c...

How do I use a password manager on my Ledger Nano S/X?
Mar 16,2025 at 09:25pm
Key Points:Ledger devices do not directly integrate with password managers. Their security model prioritizes offline key storage.You can use a password manager for your computer passwords, but not for your Ledger device seed phrase or PIN.Storing your Ledger PIN in a password manager is highly discouraged due to security risks.Strong, unique PINs and se...

How do I check the authenticity of my Ledger device?
Mar 17,2025 at 02:45pm
Key Points:Verifying your Ledger device's authenticity involves checking for several security features both on the device itself and through Ledger's official website.The packaging and the device itself contain unique identifiers that can be verified.Ledger's website provides tools to confirm the authenticity of your device and its bootloader.Understand...
See all articles