-
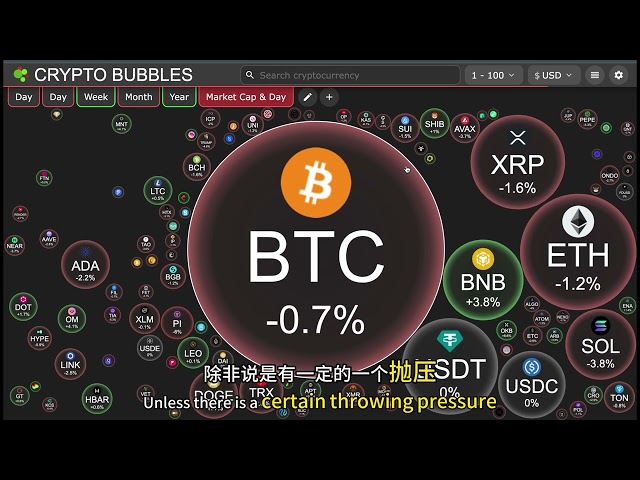
 Bitcoin
Bitcoin $83,405.1468
1.08% -
 Ethereum
Ethereum $1,912.6728
1.88% -
 Tether USDt
Tether USDt $0.9998
-0.02% -
 XRP
XRP $2.3402
1.69% -
 BNB
BNB $630.3565
5.89% -
 Solana
Solana $129.2270
-0.57% -
 USDC
USDC $0.9999
0.00% -
 Dogecoin
Dogecoin $0.1729
3.03% -
 Cardano
Cardano $0.7248
2.38% -
 TRON
TRON $0.2147
0.42% -
 Pi
Pi $1.3661
-6.43% -
 Chainlink
Chainlink $13.8271
2.04% -
 UNUS SED LEO
UNUS SED LEO $9.8262
0.10% -
 Toncoin
Toncoin $3.4413
1.84% -
 Stellar
Stellar $0.2729
3.28% -
 Hedera
Hedera $0.1916
2.99% -
 Avalanche
Avalanche $18.6675
1.25% -
 Shiba Inu
Shiba Inu $0.0...01305
2.61% -
 Sui
Sui $2.2948
2.75% -
 Litecoin
Litecoin $93.2169
4.69% -
 Polkadot
Polkadot $4.3872
4.38% -
 MANTRA
MANTRA $6.8361
4.30% -
 Bitcoin Cash
Bitcoin Cash $337.3260
3.38% -
 Ethena USDe
Ethena USDe $0.9996
-0.01% -
 Dai
Dai $1.0000
-0.01% -
 Bitget Token
Bitget Token $4.4585
2.28% -
 Hyperliquid
Hyperliquid $13.8960
3.65% -
 Monero
Monero $211.2489
0.36% -
 Uniswap
Uniswap $6.2340
3.26% -
 Aptos
Aptos $5.3849
3.93%
How do I enable privacy mode in MetaMask?
MetaMask lacks a "privacy mode," but combining a VPN, Tor, a hardware wallet, privacy-focused blockchains, and secure browsing practices significantly enhances user anonymity and security.
Mar 17, 2025 at 04:51 am

Key Points:
- MetaMask itself doesn't offer a dedicated "privacy mode" in the traditional sense. Privacy is enhanced through careful configuration and usage choices.
- Using a VPN significantly enhances your privacy when interacting with the blockchain.
- Utilizing a privacy-focused network like Tor can further obscure your IP address.
- Employing a hardware wallet offers a higher level of security and privacy compared to software wallets like MetaMask.
- Understanding and utilizing different transaction privacy features on specific blockchains is crucial.
How Do I Enable Privacy Mode in MetaMask?
The question of "enabling privacy mode" in MetaMask requires a nuanced answer. MetaMask doesn't have a single button to flip for complete privacy. Instead, achieving enhanced privacy involves several proactive steps that users must take. Thinking of it as a series of privacy-enhancing practices rather than a single "mode" is more accurate. Let's explore these practices.
1. Using a Virtual Private Network (VPN):
A VPN masks your IP address, making it more difficult for others to trace your online activities back to your physical location. This is a crucial first step in enhancing your privacy when using MetaMask. When connected to a VPN, your internet traffic is routed through a secure server, hiding your real IP address from websites and services, including blockchain nodes. Choose a reputable VPN provider with a strong privacy policy.
2. Utilizing the Tor Network:
Tor is a decentralized network that routes your internet traffic through multiple relays, making it significantly harder to track your online activity. Using Tor in conjunction with a VPN provides an additional layer of anonymity. However, be aware that Tor can be slower than a standard internet connection. Connecting MetaMask through the Tor browser adds a further layer of obfuscation to your transactions.
3. Hardware Wallets for Enhanced Security:
While MetaMask is a convenient software wallet, it stores your private keys on your computer, which can be vulnerable to malware or hacking. A hardware wallet, like Ledger or Trezor, stores your private keys offline on a secure device, significantly reducing the risk of unauthorized access and improving your overall privacy. Consider this a crucial investment for higher levels of security and, consequently, better privacy.
4. Understanding Blockchain Privacy Features:
Different blockchains offer varying degrees of transaction privacy. Some, like Zcash or Monero, are designed with privacy in mind, using techniques like zero-knowledge proofs to obscure transaction details. If you require high levels of privacy, explore using these privacy-focused cryptocurrencies and their respective wallets, though integration with MetaMask may vary.
5. Careful Transaction Practices:
Avoid broadcasting sensitive information in your transaction notes or metadata. Always be wary of phishing scams and never share your seed phrase or private keys with anyone. Regularly review and update your MetaMask security settings to ensure you're utilizing the latest features and patches. Remember, even with these practices, absolute anonymity is difficult to achieve on a public blockchain.
6. Using a Privacy-Focused Browser:
Browsers like Brave or Firefox with enhanced privacy features offer added protection compared to more mainstream browsers. These browsers often include built-in ad blockers and tracking protection, reducing the amount of data collected about your browsing habits, which can indirectly improve your privacy when using MetaMask.
7. Regular Security Audits:
Regularly check for and install security updates for your operating system and MetaMask extension. Keep your antivirus software up to date and run regular scans to detect and remove any malware that could compromise your security and privacy. Proactive security measures are crucial for maintaining privacy.
Common Questions:
Q: Does MetaMask log my transactions?
A: MetaMask itself does not log your transactions, but the blockchain you are interacting with records them publicly. Your interaction with the MetaMask interface may be subject to the privacy policies of your operating system, browser, and any other applications you are using concurrently.
Q: Can I completely anonymize my transactions using MetaMask?
A: No, complete anonymity on a public blockchain is generally not achievable. While the strategies above enhance privacy, they don't guarantee complete anonymity.
Q: Is using a VPN enough for privacy with MetaMask?
A: A VPN is a good first step, but combining it with other methods, like Tor and a hardware wallet, provides a much stronger layer of privacy.
Q: What happens if my computer is compromised while using MetaMask?
A: If your computer is compromised, your private keys stored in MetaMask could be at risk. This highlights the importance of using strong passwords, regularly updating software, and considering a hardware wallet for enhanced security.
Q: Are there any other wallets that offer better privacy than MetaMask?
A: Yes, several wallets prioritize privacy more explicitly, often integrating with privacy-focused cryptocurrencies like Monero or Zcash. Researching and choosing a wallet that aligns with your privacy needs is crucial.
Disclaimer:info@kdj.com
The information provided is not trading advice. kdj.com does not assume any responsibility for any investments made based on the information provided in this article. Cryptocurrencies are highly volatile and it is highly recommended that you invest with caution after thorough research!
If you believe that the content used on this website infringes your copyright, please contact us immediately (info@kdj.com) and we will delete it promptly.
- Why Is Coinbase a Good Business?
- 2025-03-17 20:25:57
- When it Comes to the Best Crypto to Invest in March 2025
- 2025-03-17 20:25:57
- Bitcoin Pepe (BPEP) Changes the Game With Technology That Could Transform Bitcoin Itself
- 2025-03-17 20:25:57
- XYZ Coin Crosses the $10 Million Mark in Its Presale Phase
- 2025-03-17 20:25:57
- Binance Expands Trade Offerings For MKR, EPIC, & These 3 Crypto
- 2025-03-17 20:25:57
- Arctic Pablo Coin ($APC) Presale: Explore the Depths of Cryptocurrency Investment
- 2025-03-17 20:25:57
Related knowledge

How do I use multi-signature on my hardware wallet on my Ledger device?
Mar 17,2025 at 01:36am
Key Points:Multi-signature (multisig) wallets enhance security by requiring multiple approvals for transactions.Ledger devices support multisig through compatible wallets and specific configurations.Setting up multisig involves generating multiple keys and configuring the wallet accordingly.Understanding the intricacies of threshold signatures is crucia...

How do I use staking on my Ledger device?
Mar 17,2025 at 12:41pm
Key Points:Ledger devices offer a secure way to stake various cryptocurrencies. However, the process varies depending on the coin and the chosen staking provider.You'll generally need a Ledger Live account and the correct application installed on your device.Understanding the risks associated with staking, such as potential slashing, is crucial before p...

How do I export my private keys from my Ledger device?
Mar 17,2025 at 02:30pm
Key Points:Ledger devices do not directly "export" private keys in the traditional sense. The private keys are never revealed or accessible outside the secure element of the device.You can access and use your private keys indirectly through the device's interaction with your chosen wallet software.The process involves using your Ledger device with compa...

How do I fix a connection issue with my Ledger device?
Mar 16,2025 at 08:26am
Key Points:Troubleshooting Ledger connection issues often involves checking the device's charge, the USB cable, and the computer's USB ports.Software updates on both the Ledger device and its associated computer applications are crucial for optimal functionality and connection stability.Correctly installing the Ledger Live application and ensuring its c...

How do I use a password manager on my Ledger Nano S/X?
Mar 16,2025 at 09:25pm
Key Points:Ledger devices do not directly integrate with password managers. Their security model prioritizes offline key storage.You can use a password manager for your computer passwords, but not for your Ledger device seed phrase or PIN.Storing your Ledger PIN in a password manager is highly discouraged due to security risks.Strong, unique PINs and se...

How do I check the authenticity of my Ledger device?
Mar 17,2025 at 02:45pm
Key Points:Verifying your Ledger device's authenticity involves checking for several security features both on the device itself and through Ledger's official website.The packaging and the device itself contain unique identifiers that can be verified.Ledger's website provides tools to confirm the authenticity of your device and its bootloader.Understand...

How do I use multi-signature on my hardware wallet on my Ledger device?
Mar 17,2025 at 01:36am
Key Points:Multi-signature (multisig) wallets enhance security by requiring multiple approvals for transactions.Ledger devices support multisig through compatible wallets and specific configurations.Setting up multisig involves generating multiple keys and configuring the wallet accordingly.Understanding the intricacies of threshold signatures is crucia...

How do I use staking on my Ledger device?
Mar 17,2025 at 12:41pm
Key Points:Ledger devices offer a secure way to stake various cryptocurrencies. However, the process varies depending on the coin and the chosen staking provider.You'll generally need a Ledger Live account and the correct application installed on your device.Understanding the risks associated with staking, such as potential slashing, is crucial before p...

How do I export my private keys from my Ledger device?
Mar 17,2025 at 02:30pm
Key Points:Ledger devices do not directly "export" private keys in the traditional sense. The private keys are never revealed or accessible outside the secure element of the device.You can access and use your private keys indirectly through the device's interaction with your chosen wallet software.The process involves using your Ledger device with compa...

How do I fix a connection issue with my Ledger device?
Mar 16,2025 at 08:26am
Key Points:Troubleshooting Ledger connection issues often involves checking the device's charge, the USB cable, and the computer's USB ports.Software updates on both the Ledger device and its associated computer applications are crucial for optimal functionality and connection stability.Correctly installing the Ledger Live application and ensuring its c...

How do I use a password manager on my Ledger Nano S/X?
Mar 16,2025 at 09:25pm
Key Points:Ledger devices do not directly integrate with password managers. Their security model prioritizes offline key storage.You can use a password manager for your computer passwords, but not for your Ledger device seed phrase or PIN.Storing your Ledger PIN in a password manager is highly discouraged due to security risks.Strong, unique PINs and se...

How do I check the authenticity of my Ledger device?
Mar 17,2025 at 02:45pm
Key Points:Verifying your Ledger device's authenticity involves checking for several security features both on the device itself and through Ledger's official website.The packaging and the device itself contain unique identifiers that can be verified.Ledger's website provides tools to confirm the authenticity of your device and its bootloader.Understand...
See all articles