-
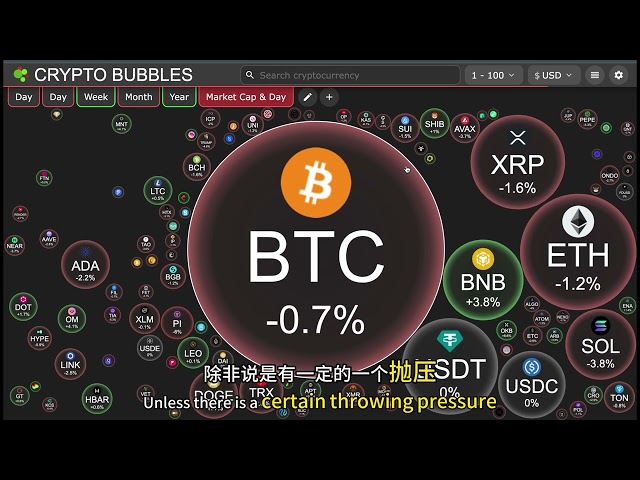
 Bitcoin
Bitcoin $83,405.1468
1.08% -
 Ethereum
Ethereum $1,912.6728
1.88% -
 Tether USDt
Tether USDt $0.9998
-0.02% -
 XRP
XRP $2.3402
1.69% -
 BNB
BNB $630.3565
5.89% -
 Solana
Solana $129.2270
-0.57% -
 USDC
USDC $0.9999
0.00% -
 Dogecoin
Dogecoin $0.1729
3.03% -
 Cardano
Cardano $0.7248
2.38% -
 TRON
TRON $0.2147
0.42% -
 Pi
Pi $1.3661
-6.43% -
 Chainlink
Chainlink $13.8271
2.04% -
 UNUS SED LEO
UNUS SED LEO $9.8262
0.10% -
 Toncoin
Toncoin $3.4413
1.84% -
 Stellar
Stellar $0.2729
3.28% -
 Hedera
Hedera $0.1916
2.99% -
 Avalanche
Avalanche $18.6675
1.25% -
 Shiba Inu
Shiba Inu $0.0...01305
2.61% -
 Sui
Sui $2.2948
2.75% -
 Litecoin
Litecoin $93.2169
4.69% -
 Polkadot
Polkadot $4.3872
4.38% -
 MANTRA
MANTRA $6.8361
4.30% -
 Bitcoin Cash
Bitcoin Cash $337.3260
3.38% -
 Ethena USDe
Ethena USDe $0.9996
-0.01% -
 Dai
Dai $1.0000
-0.01% -
 Bitget Token
Bitget Token $4.4585
2.28% -
 Hyperliquid
Hyperliquid $13.8960
3.65% -
 Monero
Monero $211.2489
0.36% -
 Uniswap
Uniswap $6.2340
3.26% -
 Aptos
Aptos $5.3849
3.93%
What are the common methods for generating Ethereum wallet addresses?
Ethereum wallet addresses are generated cryptographically, offering varying security levels depending on the method: online, software, or hardware wallets. Each provides different levels of control and security, with hardware wallets being the most secure but also the most expensive.
Mar 12, 2025 at 12:50 am

Key Points:
- Ethereum wallet addresses are generated using cryptographic techniques, ensuring uniqueness and security.
- Several methods exist, ranging from using online wallets to creating your own with software or hardware.
- Each method offers varying levels of security and control, influencing the choice for different users.
- Understanding the underlying principles of key generation is crucial for secure wallet management.
- Security best practices are paramount regardless of the chosen address generation method.
What are the common methods for generating Ethereum wallet addresses?
Generating an Ethereum wallet address involves creating a unique cryptographic key pair. This key pair comprises a private key (kept secret) and a public key (used to receive Ether and tokens). The public key is then converted into an address, a shortened version displayed on the blockchain. Several methods facilitate this process:
1. Using Online Wallets:
Many online services offer Ethereum wallets. These platforms handle the key generation process for you. Simply create an account and the wallet is automatically generated. The ease of use comes at the cost of relinquishing control over your private keys to the service provider. Security relies heavily on the platform's security measures. Examples include MetaMask, Trust Wallet, and Coinbase Wallet.
2. Using Software Wallets:
Software wallets, like MyEtherWallet or Parity, are downloaded and installed on your computer. These provide more control than online wallets, as you manage your keys locally. However, security depends on your computer's security and the software's integrity. It's crucial to download only from official sources and protect your computer from malware.
3. Using Hardware Wallets:
Hardware wallets, such as Ledger and Trezor, are physical devices storing your private keys offline. This is the most secure method. They offer a high degree of protection against hacking and malware. However, they are typically more expensive than other options. Losing the device means losing access to your funds.
4. Generating Addresses Manually:
This method requires a deep understanding of cryptography and is generally not recommended for beginners. It involves using cryptographic libraries and algorithms to generate a key pair. Errors during this process can render your wallet unusable or compromise its security. Expertise in cryptography and secure coding practices are essential.
Understanding Key Generation:
The core of any Ethereum wallet address generation lies in the creation of a private key. This is usually a random 256-bit number. From this private key, a public key is derived using elliptic curve cryptography (ECC). The Ethereum address is then generated by hashing the public key using Keccak-256, a cryptographic hash function. This process ensures that each address is unique and prevents collisions.
Security Considerations:
Regardless of the method, securing your wallet is paramount. Never share your private key with anyone. Be wary of phishing scams and only use reputable wallet providers. Regularly back up your wallet and keep your software updated. For hardware wallets, ensure you have a recovery seed phrase safely stored in a secure location.
Common Questions and Answers:
Q: Are online wallets safe?
A: Online wallets offer convenience but compromise control over your private keys. Their safety relies on the platform's security. Use only reputable providers and practice strong password hygiene.
Q: What is a private key and why is it so important?
A: A private key is a secret number that allows you to access and control your Ethereum funds. Without it, you cannot spend your cryptocurrency. Losing or compromising it results in irreversible loss of funds.
Q: How do I choose the right wallet type?
A: The best wallet type depends on your technical skills and security needs. Beginners might prefer online wallets for ease of use, while experienced users may opt for hardware wallets for maximum security. Software wallets offer a middle ground.
Q: What happens if I lose my private key or hardware wallet?
A: Losing your private key or hardware wallet means losing access to your Ethereum funds. It's crucial to back up your wallet securely and store your recovery phrase in a safe place.
Q: Can I generate multiple addresses from a single private key?
A: No, each private key corresponds to a single Ethereum address. However, you can create multiple wallets, each with its own private key and address.
Q: Is it possible to recover an Ethereum address if I forget my password?
A: Recovery depends on the type of wallet. Online wallets may offer password recovery options, but hardware and software wallets rely on your backup seed phrase. Without it, recovery is generally not possible.
Q: What is a seed phrase and how important is it?
A: A seed phrase (or recovery phrase) is a list of words that allows you to restore your wallet if you lose access to it. It is crucial to keep this phrase safe and secure; losing it results in the irreversible loss of your funds. It's as important as the private key itself.
Q: How does Ethereum ensure the uniqueness of wallet addresses?
A: The combination of cryptographic hashing and elliptic curve cryptography ensures the uniqueness of each Ethereum address. The probability of two different private keys resulting in the same address is astronomically low.
Disclaimer:info@kdj.com
The information provided is not trading advice. kdj.com does not assume any responsibility for any investments made based on the information provided in this article. Cryptocurrencies are highly volatile and it is highly recommended that you invest with caution after thorough research!
If you believe that the content used on this website infringes your copyright, please contact us immediately (info@kdj.com) and we will delete it promptly.
- Shiba Inu ($SHIB) Refuses to Back Down
- 2025-03-17 19:30:57
- Fear & Greed Index Slips to “Fear” Territory at 22
- 2025-03-17 19:30:57
- Coinbase Adds Doginme ($DOGINME) to Its Listing Roadmap, Sending the Token's Price Soaring
- 2025-03-17 19:30:57
- Bitcoin (BTC) Flashes Strong Bullish Signals, Targeting $100K Breakout This Month
- 2025-03-17 19:25:57
- Solaxy (SOLX) Raises $26.7M in Presale to Fix Solana's Congestion Problems
- 2025-03-17 19:25:57
- XRPTurbo, an AI-powered launchpad for the next generation of XRP tokens and NFTs
- 2025-03-17 19:25:57
Related knowledge

How do I use multi-signature on my hardware wallet on my Ledger device?
Mar 17,2025 at 01:36am
Key Points:Multi-signature (multisig) wallets enhance security by requiring multiple approvals for transactions.Ledger devices support multisig through compatible wallets and specific configurations.Setting up multisig involves generating multiple keys and configuring the wallet accordingly.Understanding the intricacies of threshold signatures is crucia...

How do I use staking on my Ledger device?
Mar 17,2025 at 12:41pm
Key Points:Ledger devices offer a secure way to stake various cryptocurrencies. However, the process varies depending on the coin and the chosen staking provider.You'll generally need a Ledger Live account and the correct application installed on your device.Understanding the risks associated with staking, such as potential slashing, is crucial before p...

How do I export my private keys from my Ledger device?
Mar 17,2025 at 02:30pm
Key Points:Ledger devices do not directly "export" private keys in the traditional sense. The private keys are never revealed or accessible outside the secure element of the device.You can access and use your private keys indirectly through the device's interaction with your chosen wallet software.The process involves using your Ledger device with compa...

How do I fix a connection issue with my Ledger device?
Mar 16,2025 at 08:26am
Key Points:Troubleshooting Ledger connection issues often involves checking the device's charge, the USB cable, and the computer's USB ports.Software updates on both the Ledger device and its associated computer applications are crucial for optimal functionality and connection stability.Correctly installing the Ledger Live application and ensuring its c...

How do I use a password manager on my Ledger Nano S/X?
Mar 16,2025 at 09:25pm
Key Points:Ledger devices do not directly integrate with password managers. Their security model prioritizes offline key storage.You can use a password manager for your computer passwords, but not for your Ledger device seed phrase or PIN.Storing your Ledger PIN in a password manager is highly discouraged due to security risks.Strong, unique PINs and se...

How do I check the authenticity of my Ledger device?
Mar 17,2025 at 02:45pm
Key Points:Verifying your Ledger device's authenticity involves checking for several security features both on the device itself and through Ledger's official website.The packaging and the device itself contain unique identifiers that can be verified.Ledger's website provides tools to confirm the authenticity of your device and its bootloader.Understand...

How do I use multi-signature on my hardware wallet on my Ledger device?
Mar 17,2025 at 01:36am
Key Points:Multi-signature (multisig) wallets enhance security by requiring multiple approvals for transactions.Ledger devices support multisig through compatible wallets and specific configurations.Setting up multisig involves generating multiple keys and configuring the wallet accordingly.Understanding the intricacies of threshold signatures is crucia...

How do I use staking on my Ledger device?
Mar 17,2025 at 12:41pm
Key Points:Ledger devices offer a secure way to stake various cryptocurrencies. However, the process varies depending on the coin and the chosen staking provider.You'll generally need a Ledger Live account and the correct application installed on your device.Understanding the risks associated with staking, such as potential slashing, is crucial before p...

How do I export my private keys from my Ledger device?
Mar 17,2025 at 02:30pm
Key Points:Ledger devices do not directly "export" private keys in the traditional sense. The private keys are never revealed or accessible outside the secure element of the device.You can access and use your private keys indirectly through the device's interaction with your chosen wallet software.The process involves using your Ledger device with compa...

How do I fix a connection issue with my Ledger device?
Mar 16,2025 at 08:26am
Key Points:Troubleshooting Ledger connection issues often involves checking the device's charge, the USB cable, and the computer's USB ports.Software updates on both the Ledger device and its associated computer applications are crucial for optimal functionality and connection stability.Correctly installing the Ledger Live application and ensuring its c...

How do I use a password manager on my Ledger Nano S/X?
Mar 16,2025 at 09:25pm
Key Points:Ledger devices do not directly integrate with password managers. Their security model prioritizes offline key storage.You can use a password manager for your computer passwords, but not for your Ledger device seed phrase or PIN.Storing your Ledger PIN in a password manager is highly discouraged due to security risks.Strong, unique PINs and se...

How do I check the authenticity of my Ledger device?
Mar 17,2025 at 02:45pm
Key Points:Verifying your Ledger device's authenticity involves checking for several security features both on the device itself and through Ledger's official website.The packaging and the device itself contain unique identifiers that can be verified.Ledger's website provides tools to confirm the authenticity of your device and its bootloader.Understand...
See all articles