-
 Bitcoin
Bitcoin $96,161.2493
-2.14% -
 Ethereum
Ethereum $2,686.5756
-2.45% -
 XRP
XRP $2.5719
-3.67% -
 Tether USDt
Tether USDt $0.9999
-0.04% -
 BNB
BNB $655.8976
-0.15% -
 Solana
Solana $171.9849
-2.65% -
 USDC
USDC $1.0001
0.00% -
 Dogecoin
Dogecoin $0.2435
-4.35% -
 Cardano
Cardano $0.7615
-4.97% -
 TRON
TRON $0.2379
-4.28% -
 Chainlink
Chainlink $17.4447
-5.17% -
 Avalanche
Avalanche $24.9624
-1.92% -
 Sui
Sui $3.3374
-3.85% -
 Stellar
Stellar $0.3266
-3.96% -
 Litecoin
Litecoin $127.2255
-5.17% -
 Toncoin
Toncoin $3.6609
1.73% -
 Shiba Inu
Shiba Inu $0.0...01526
-2.42% -
 UNUS SED LEO
UNUS SED LEO $9.7275
-0.32% -
 Hedera
Hedera $0.2145
-3.18% -
 Hyperliquid
Hyperliquid $24.2706
-2.62% -
 Polkadot
Polkadot $5.0883
0.29% -
 MANTRA
MANTRA $7.6370
0.37% -
 Bitcoin Cash
Bitcoin Cash $317.1514
-3.50% -
 Bitget Token
Bitget Token $5.0005
7.55% -
 Ethena USDe
Ethena USDe $0.9987
-0.10% -
 Dai
Dai $1.0000
-0.01% -
 Uniswap
Uniswap $8.8025
-5.45% -
 Monero
Monero $233.1225
-0.50% -
 NEAR Protocol
NEAR Protocol $3.4727
-2.15% -
 Pepe
Pepe $0.0...09302
-4.88%
How secure is the LTO Network coin network?
The LTO Network's multi-layered security measures, including multi-signature authentication, DPoS consensus, and advanced cryptography, ensure the integrity and robustness of its blockchain and data.
Dec 30, 2024 at 08:23 am

Key Points:
- The LTO Network employs multiple layers of security measures to safeguard its blockchain and data.
- Features such as multi-signature authentication, consensus mechanisms, and advanced cryptography ensure the network's robustness and integrity.
- Continuous monitoring, vulnerability assessments, and strict protocols enhance the LTO Network's security posture.
In-Depth Analysis
1. Multi-Signature Authentication
- Multi-signature technology requires multiple parties (typically two or more) to sign off on a transaction before it is processed on the blockchain.
- This mechanism ensures that sensitive operations, such as transferring large amounts of LTO tokens, are authorized by multiple individuals, reducing the risk of unauthorized transactions.
- The LTO Network employs multi-signature requirements for specific actions, enhancing the network's overall security.
2. Consensus Mechanisms
- Consensus mechanisms are algorithms used by the network to reach an agreement on the validity of transactions and determine the true state of the blockchain.
- The LTO Network utilizes a Delegated Proof-of-Stake (DPoS) consensus mechanism, where a group of elected delegates validate transactions and maintain the network.
- This mechanism ensures that the network remains stable and secure, preventing malicious actors from gaining control or manipulating the blockchain.
3. Advanced Cryptography
- The LTO Network employs advanced cryptographic algorithms, such as elliptic curve cryptography (ECC) and SHA256 hashing, to protect data and transactions.
- ECC provides robust encryption, making it computationally infeasible to reverse-engineer private keys or forge transactions.
- SHA256 hashing ensures that data stored on the blockchain is immutable and tamper-proof, enhancing the network's integrity.
4. Continuous Monitoring
- The LTO Network infrastructure undergoes continuous monitoring to detect and respond to security vulnerabilities or suspicious activities.
- Real-time monitoring systems analyze network traffic, server logs, and transaction patterns to identify potential threats.
- Security personnel are constantly vigilant and can quickly take action to mitigate any identified risks, ensuring the network's security and resilience.
5. Vulnerability Assessments
- Regular vulnerability assessments are conducted to identify and mitigate potential weaknesses in the LTO Network software and infrastructure.
- Independent security experts and third-party auditors thoroughly review the network's code, systems, and protocols to identify any vulnerabilities.
- Any identified vulnerabilities are promptly addressed through security patches and updates, further enhancing the network's overall security.
6. Strict Security Protocols
- The LTO Network follows stringent security protocols and best practices to safeguard its blockchain and data.
- These protocols include robust access control mechanisms, secure data storage practices, and regular software updates.
- Employees and contractors undergo thorough background checks and are required to adhere to strict confidentiality and security regulations.
FAQs
Q: How does the LTO Network compare to other cryptocurrency networks in terms of security?
A: The LTO Network employs a comprehensive security framework that combines industry-standard best practices with innovative technologies. While direct comparisons with other networks may vary due to different security models, the LTO Network is recognized for its robust multi-signature authentication, consensus mechanism, and advanced cryptography.
Q: Has the LTO Network ever been hacked or compromised?
A: As of the time of this publication, the LTO Network has not experienced any successful hacks or breaches that have compromised the integrity of its blockchain or user data. The network's security measures, continuous monitoring, and vulnerability assessments effectively mitigate potential risks and maintain the network's stability.
Q: What steps can users take to enhance their own security on the LTO Network?
A: Users are encouraged to adopt best practices to protect their LTO tokens and personal information. These include using strong passwords, enabling two-factor authentication, storing tokens in secure wallets, and being cautious of phishing scams. By adhering to security guidelines, users can contribute to the overall security of the LTO Network ecosystem.
Disclaimer:info@kdj.com
The information provided is not trading advice. kdj.com does not assume any responsibility for any investments made based on the information provided in this article. Cryptocurrencies are highly volatile and it is highly recommended that you invest with caution after thorough research!
If you believe that the content used on this website infringes your copyright, please contact us immediately (info@kdj.com) and we will delete it promptly.
- Tether Launches TradeFi, a Blockchain-Based Financial Service Aimed at Optimizing International Trade
- 2025-02-22 17:00:25
- Altcoin Season Has Begun, Proclaims CryptoQuant CEO Ki Young Ju
- 2025-02-22 17:00:25
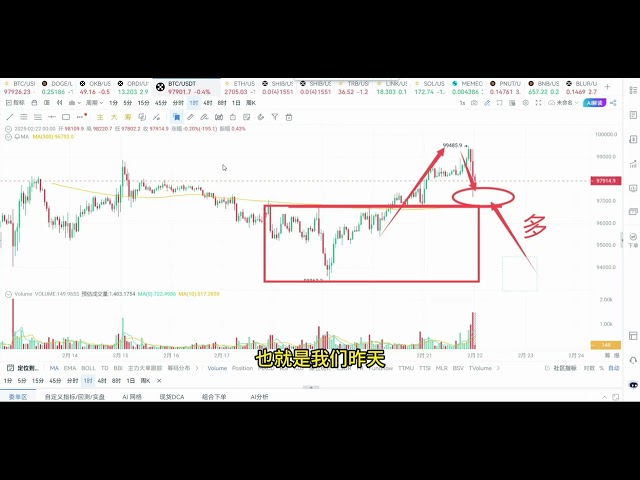
- Bybit Hack: Crypto Exchange Loses $1.4B in ETH, Market Cap Drops 1.86% to $3.17 Trillion
- 2025-02-22 17:00:25
- Ethereum (ETH), FTX Token (FTT), Coinbase, stETH, and Blur (BLUR) Are the Top 5 Most Attention-Grabbing Cryptocurrency-Related Keywords
- 2025-02-22 17:00:25
- Bybit Hack: Exchange Loses Over $1.1 Billion in Ethereum in One of the Biggest Security Breaches Ever
- 2025-02-22 17:00:25
- How to Build a Crypto Price Alert System Using CoinGecko and Python
- 2025-02-22 17:00:25
Related knowledge

What are the long-term investment risks of Bitcoin?
Feb 22,2025 at 05:30pm
Key PointsVolatility and price fluctuationsRegulatory uncertaintySecurity risksCompetition from altcoinsMarket manipulation and scamsTransaction feesEnvironmental concernsLong-Term Investment Risks of BitcoinVolatility and Price FluctuationsBitcoin's high volatility is a double-edged sword. While it has the potential to generate substantial returns, it ...

What are the main contents of Bitcoin's "white paper"?
Feb 21,2025 at 04:36am
Key Points:Understanding Bitcoin's Genesis: The White Paper's IntroductionA Decentralized Digital Currency: Bitcoin's Core ConceptBlockchain Technology: The Foundation of Bitcoin's Immutable LedgerProof-of-Work: Securing Bitcoin's NetworkThe Design of Bitcoin's Currency: Issuance, Scarcity, and DivisibilityBitcoin's Potential Applications and Future Pro...

What does the Cryptographic Fundamentals of Bitcoin consist of?
Feb 21,2025 at 12:06pm
Key PointsUnderstanding the cryptographic algorithms used in BitcoinFamiliarization with the Bitcoin blockchain and its underlying mechanicsExamination of the security measures that protect Bitcoin from attackAnalysis of the decentralized nature of Bitcoin and its implicationsDiscussion of the scalability and transaction fee issues associated with Bitco...

How do Bitcoin mining pools work?
Feb 21,2025 at 09:07pm
Key Points of Bitcoin Mining Pools:Understanding Bitcoin Mining PoolsSteps to Join a Bitcoin Mining PoolChoosing the Right Mining PoolBenefits and Considerations of Mining PoolsHow do Bitcoin mining pools work?Understanding Bitcoin Mining PoolsBitcoin mining pools are distributed networks of mining participants who combine their computing power to solve...

What role does Bitcoin's hash function play in the system?
Feb 21,2025 at 09:06am
Key PointsSecure Data Storage: The hash function safeguards data within Bitcoin's blockchain, ensuring its immutability and integrity.Transaction Verification: The hash function plays a crucial role in verifying transactions and maintaining the network's consensus.Security against Double-Spending: The hash function helps prevent double-spending by crypt...

What is the initial purchase and transaction process for Bitcoin?
Feb 20,2025 at 01:00pm
Key Points:Understanding the concept of BitcoinCreating a Bitcoin walletFunding your Bitcoin walletPurchasing Bitcoin through an exchangeConfirming and receiving BitcoinInitial Purchase and Transaction Process for Bitcoin1. Understanding BitcoinBitcoin is a decentralized digital currency created in 2009 by an unknown individual or group using the pseudo...

What are the long-term investment risks of Bitcoin?
Feb 22,2025 at 05:30pm
Key PointsVolatility and price fluctuationsRegulatory uncertaintySecurity risksCompetition from altcoinsMarket manipulation and scamsTransaction feesEnvironmental concernsLong-Term Investment Risks of BitcoinVolatility and Price FluctuationsBitcoin's high volatility is a double-edged sword. While it has the potential to generate substantial returns, it ...

What are the main contents of Bitcoin's "white paper"?
Feb 21,2025 at 04:36am
Key Points:Understanding Bitcoin's Genesis: The White Paper's IntroductionA Decentralized Digital Currency: Bitcoin's Core ConceptBlockchain Technology: The Foundation of Bitcoin's Immutable LedgerProof-of-Work: Securing Bitcoin's NetworkThe Design of Bitcoin's Currency: Issuance, Scarcity, and DivisibilityBitcoin's Potential Applications and Future Pro...

What does the Cryptographic Fundamentals of Bitcoin consist of?
Feb 21,2025 at 12:06pm
Key PointsUnderstanding the cryptographic algorithms used in BitcoinFamiliarization with the Bitcoin blockchain and its underlying mechanicsExamination of the security measures that protect Bitcoin from attackAnalysis of the decentralized nature of Bitcoin and its implicationsDiscussion of the scalability and transaction fee issues associated with Bitco...

How do Bitcoin mining pools work?
Feb 21,2025 at 09:07pm
Key Points of Bitcoin Mining Pools:Understanding Bitcoin Mining PoolsSteps to Join a Bitcoin Mining PoolChoosing the Right Mining PoolBenefits and Considerations of Mining PoolsHow do Bitcoin mining pools work?Understanding Bitcoin Mining PoolsBitcoin mining pools are distributed networks of mining participants who combine their computing power to solve...

What role does Bitcoin's hash function play in the system?
Feb 21,2025 at 09:06am
Key PointsSecure Data Storage: The hash function safeguards data within Bitcoin's blockchain, ensuring its immutability and integrity.Transaction Verification: The hash function plays a crucial role in verifying transactions and maintaining the network's consensus.Security against Double-Spending: The hash function helps prevent double-spending by crypt...

What is the initial purchase and transaction process for Bitcoin?
Feb 20,2025 at 01:00pm
Key Points:Understanding the concept of BitcoinCreating a Bitcoin walletFunding your Bitcoin walletPurchasing Bitcoin through an exchangeConfirming and receiving BitcoinInitial Purchase and Transaction Process for Bitcoin1. Understanding BitcoinBitcoin is a decentralized digital currency created in 2009 by an unknown individual or group using the pseudo...
See all articles

















![BONK The Meme Coin MORE THAN ORDINARY [DOG] on Solana BONK The Meme Coin MORE THAN ORDINARY [DOG] on Solana](/uploads/2025/02/22/cryptocurrencies-news/videos/bonk-meme-coin-ordinary-dog-solana/image-1.jpg)