-
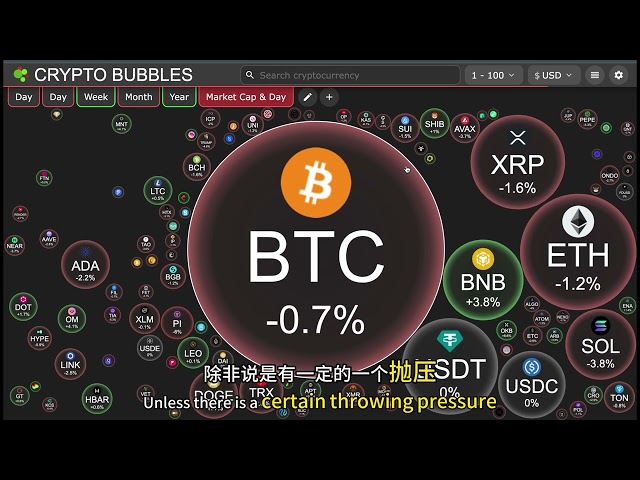
 Bitcoin
Bitcoin $83,405.1468
1.08% -
 Ethereum
Ethereum $1,912.6728
1.88% -
 Tether USDt
Tether USDt $0.9998
-0.02% -
 XRP
XRP $2.3402
1.69% -
 BNB
BNB $630.3565
5.89% -
 Solana
Solana $129.2270
-0.57% -
 USDC
USDC $0.9999
0.00% -
 Dogecoin
Dogecoin $0.1729
3.03% -
 Cardano
Cardano $0.7248
2.38% -
 TRON
TRON $0.2147
0.42% -
 Pi
Pi $1.3661
-6.43% -
 Chainlink
Chainlink $13.8271
2.04% -
 UNUS SED LEO
UNUS SED LEO $9.8262
0.10% -
 Toncoin
Toncoin $3.4413
1.84% -
 Stellar
Stellar $0.2729
3.28% -
 Hedera
Hedera $0.1916
2.99% -
 Avalanche
Avalanche $18.6675
1.25% -
 Shiba Inu
Shiba Inu $0.0...01305
2.61% -
 Sui
Sui $2.2948
2.75% -
 Litecoin
Litecoin $93.2169
4.69% -
 Polkadot
Polkadot $4.3872
4.38% -
 MANTRA
MANTRA $6.8361
4.30% -
 Bitcoin Cash
Bitcoin Cash $337.3260
3.38% -
 Ethena USDe
Ethena USDe $0.9996
-0.01% -
 Dai
Dai $1.0000
-0.01% -
 Bitget Token
Bitget Token $4.4585
2.28% -
 Hyperliquid
Hyperliquid $13.8960
3.65% -
 Monero
Monero $211.2489
0.36% -
 Uniswap
Uniswap $6.2340
3.26% -
 Aptos
Aptos $5.3849
3.93%
How secure is AVAX coin? What encryption technologies does it use?
AVAX security relies on a layered approach: its novel Avalanche consensus mechanism, robust cryptographic hashing, regular security audits, and community scrutiny. While strong, no cryptocurrency is invulnerable; user vigilance remains crucial.
Mar 12, 2025 at 08:50 am

Key Points:
- Avalanche's security relies on a multi-faceted approach, not solely on a single encryption technology.
- It utilizes a novel consensus mechanism, Avalanche, offering high throughput and security.
- The platform benefits from strong cryptographic hashing algorithms for transaction verification.
- Security audits and community scrutiny play a significant role in enhancing AVAX's overall security.
- While robust, no cryptocurrency is entirely immune to potential vulnerabilities.
How Secure is AVAX Coin? What Encryption Technologies Does It Use?
The security of AVAX, the native token of the Avalanche blockchain, is a complex issue dependent on several interwoven factors. It's not simply a matter of a single encryption technology but rather a layered security architecture. Understanding this multi-faceted approach is crucial to assessing the overall security posture of the AVAX coin and the Avalanche platform.
Firstly, Avalanche's core innovation lies in its unique consensus mechanism, also called Avalanche. This algorithm differs significantly from Proof-of-Work (PoW) and Proof-of-Stake (PoS) systems. Unlike PoW's energy-intensive approach, Avalanche employs a probabilistic sampling method to achieve consensus quickly and efficiently. This speeds up transaction finality while offering high security through its inherent redundancy. The more validators participating, the more robust the consensus becomes. The system constantly validates transactions, reducing vulnerabilities and making it far more difficult for malicious actors to manipulate the network.
Beyond the consensus mechanism, the Avalanche platform employs robust cryptographic hashing algorithms. These algorithms are fundamental to ensuring the integrity and immutability of transactions recorded on the blockchain. These hashing functions are designed to be one-way functions, meaning it is computationally infeasible to reverse the process and derive the original input from the hash value. This prevents tampering with transaction data after it has been recorded. Specific algorithms used are continuously reviewed and updated based on advancements in cryptographic research. This commitment to constant improvement ensures the platform keeps pace with evolving security threats.
The security of AVAX also benefits from the community's active participation in monitoring the network. Regular security audits by independent firms are conducted to identify and address potential vulnerabilities. These audits act as an important check and balance, helping to uncover any weaknesses in the system's design or implementation before they can be exploited. Furthermore, the open-source nature of the Avalanche protocol allows for community scrutiny, with developers and security researchers continuously examining the codebase for potential flaws. This constant vigilance acts as a powerful deterrent against malicious actors and helps to maintain the overall security of the network.
However, it's crucial to remember that no cryptocurrency is entirely immune to risks. While the Avalanche protocol employs advanced security measures, vulnerabilities could still exist. Software bugs, unforeseen attacks, and even human error remain potential threats. The constant evolution of the cryptographic landscape necessitates continuous improvement and adaptation to maintain a high level of security. The Avalanche team actively addresses identified issues and incorporates community feedback to improve security protocols.
The use of strong cryptographic techniques combined with the decentralized nature of the network and community scrutiny are key components to the security model of Avalanche. However, user security also relies on best practices. Users must secure their private keys, be wary of phishing scams, and utilize secure wallets. The responsibility for security isn't solely on the developers but also on the users themselves.
Common Questions:
Q: What are the specific cryptographic hashing algorithms used by Avalanche?
A: Avalanche doesn't publicly specify every single algorithm used for internal processes. However, it relies heavily on well-established and widely used cryptographic hashing algorithms for transaction verification and data integrity. These would likely include SHA-256, or its successor SHA-3, and potentially other variations depending on specific implementation needs. The choice of algorithms is based on their security and performance characteristics.
Q: How does the Avalanche consensus mechanism improve security compared to traditional PoW or PoS?
A: Avalanche offers several security advantages. Unlike PoW, it avoids the energy-intensive mining process, making it more environmentally friendly. Compared to PoS, Avalanche's probabilistic sampling method allows for faster transaction finality and a higher throughput, which is less vulnerable to attacks that target the consensus process. Its decentralized nature and redundancy also offer greater resilience against malicious actors attempting to control the network.
Q: Are there any known vulnerabilities in the AVAX coin or Avalanche platform?
A: While Avalanche has a strong security record, like all blockchain platforms, it’s not immune to potential vulnerabilities. Publicly disclosed vulnerabilities are rare, and the team usually addresses them promptly. However, the possibility of undiscovered vulnerabilities always exists, which is why continuous security audits and community scrutiny are essential. Staying informed about any security updates or advisories issued by the Avalanche team is crucial for users.
Q: How can I protect my AVAX coins from theft or loss?
A: Securely storing your AVAX coins is paramount. Use reputable and well-reviewed hardware wallets for the most secure storage. Avoid storing large amounts of AVAX on exchanges, as they are susceptible to hacks. Always be wary of phishing attempts, verify the legitimacy of websites and emails before interacting with them, and never share your private keys with anyone. Regularly update your wallet software to benefit from the latest security patches.
Disclaimer:info@kdj.com
The information provided is not trading advice. kdj.com does not assume any responsibility for any investments made based on the information provided in this article. Cryptocurrencies are highly volatile and it is highly recommended that you invest with caution after thorough research!
If you believe that the content used on this website infringes your copyright, please contact us immediately (info@kdj.com) and we will delete it promptly.
- Shiba Inu ($SHIB) Refuses to Back Down
- 2025-03-17 19:30:57
- Fear & Greed Index Slips to “Fear” Territory at 22
- 2025-03-17 19:30:57
- Coinbase Adds Doginme ($DOGINME) to Its Listing Roadmap, Sending the Token's Price Soaring
- 2025-03-17 19:30:57
- Bitcoin (BTC) Flashes Strong Bullish Signals, Targeting $100K Breakout This Month
- 2025-03-17 19:25:57
- Solaxy (SOLX) Raises $26.7M in Presale to Fix Solana's Congestion Problems
- 2025-03-17 19:25:57
- XRPTurbo, an AI-powered launchpad for the next generation of XRP tokens and NFTs
- 2025-03-17 19:25:57
Related knowledge

Which cryptocurrency websites are good for beginners?
Mar 14,2025 at 04:48pm
CoinbaseUser - friendly Interface: Coinbase offers a clean and intuitive interface that is easy for beginners to navigate. The platform is designed to be straightforward, with clear instructions for tasks like creating an account, depositing funds, and buying/selling cryptocurrencies. For example, when you log in, you are greeted with a dashboard that s...

How much will Bitcoin be worth in 2025
Mar 14,2025 at 04:23pm
Predicting the value of Bitcoin in 2025 is an extremely complex task. Bitcoin, as the pioneer of cryptocurrencies, has a price influenced by a vast array of factors, ranging from market dynamics and technological advancements to regulatory changes and global economic conditions.Market Supply and DemandLimited Supply: Bitcoin has a capped supply of 21 mi...

How to issue an ERC-20 token?
Mar 15,2025 at 04:20pm
Key Points:Understanding the prerequisites for ERC-20 token creation.Choosing the right development environment and tools.Writing the smart contract code.Compiling and deploying the smart contract to the Ethereum network.Testing the deployed token thoroughly.Listing the token on exchanges (optional).How to Issue an ERC-20 Token?Issuing an ERC-20 token i...

What are the core functions of the smart contract of ERC-20 tokens?
Mar 15,2025 at 11:10am
Key Points:ERC-20 smart contracts define the core functionality of a token, enabling transferability, balance tracking, and allowance for delegated transfers.Beyond basic token mechanics, smart contracts can incorporate features like burning, minting, and pausing token transactions.Advanced functionalities may include integration with other DeFi protoco...

What are the main functions of ERC-20 tokens?
Mar 13,2025 at 12:21am
Key Points:ERC-20 tokens are standardized tokens built on the Ethereum blockchain, enabling interoperability and ease of use.Their primary function is to represent fungible assets, meaning each token is interchangeable with any other of the same type.ERC-20 tokens facilitate various use cases, including fundraising (ICOs/IEOs), representing in-game asse...

How are ERC-20 tokens created on the Ethereum blockchain?
Mar 13,2025 at 01:30pm
Key Points:ERC-20 tokens are created by deploying a smart contract to the Ethereum blockchain.This smart contract defines the token's properties, such as name, symbol, total supply, and decimals.Several tools and platforms simplify the process, including online IDEs and dedicated token creation services.Understanding Solidity programming is crucial for ...

Which cryptocurrency websites are good for beginners?
Mar 14,2025 at 04:48pm
CoinbaseUser - friendly Interface: Coinbase offers a clean and intuitive interface that is easy for beginners to navigate. The platform is designed to be straightforward, with clear instructions for tasks like creating an account, depositing funds, and buying/selling cryptocurrencies. For example, when you log in, you are greeted with a dashboard that s...

How much will Bitcoin be worth in 2025
Mar 14,2025 at 04:23pm
Predicting the value of Bitcoin in 2025 is an extremely complex task. Bitcoin, as the pioneer of cryptocurrencies, has a price influenced by a vast array of factors, ranging from market dynamics and technological advancements to regulatory changes and global economic conditions.Market Supply and DemandLimited Supply: Bitcoin has a capped supply of 21 mi...

How to issue an ERC-20 token?
Mar 15,2025 at 04:20pm
Key Points:Understanding the prerequisites for ERC-20 token creation.Choosing the right development environment and tools.Writing the smart contract code.Compiling and deploying the smart contract to the Ethereum network.Testing the deployed token thoroughly.Listing the token on exchanges (optional).How to Issue an ERC-20 Token?Issuing an ERC-20 token i...

What are the core functions of the smart contract of ERC-20 tokens?
Mar 15,2025 at 11:10am
Key Points:ERC-20 smart contracts define the core functionality of a token, enabling transferability, balance tracking, and allowance for delegated transfers.Beyond basic token mechanics, smart contracts can incorporate features like burning, minting, and pausing token transactions.Advanced functionalities may include integration with other DeFi protoco...

What are the main functions of ERC-20 tokens?
Mar 13,2025 at 12:21am
Key Points:ERC-20 tokens are standardized tokens built on the Ethereum blockchain, enabling interoperability and ease of use.Their primary function is to represent fungible assets, meaning each token is interchangeable with any other of the same type.ERC-20 tokens facilitate various use cases, including fundraising (ICOs/IEOs), representing in-game asse...

How are ERC-20 tokens created on the Ethereum blockchain?
Mar 13,2025 at 01:30pm
Key Points:ERC-20 tokens are created by deploying a smart contract to the Ethereum blockchain.This smart contract defines the token's properties, such as name, symbol, total supply, and decimals.Several tools and platforms simplify the process, including online IDEs and dedicated token creation services.Understanding Solidity programming is crucial for ...
See all articles