-
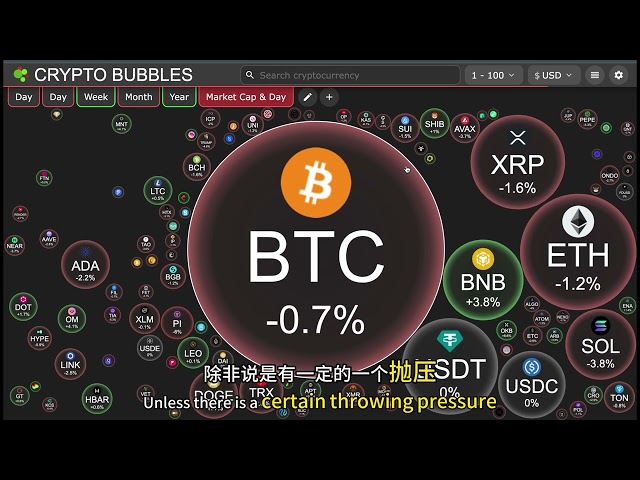
 Bitcoin
Bitcoin $83,405.1468
1.08% -
 Ethereum
Ethereum $1,912.6728
1.88% -
 Tether USDt
Tether USDt $0.9998
-0.02% -
 XRP
XRP $2.3402
1.69% -
 BNB
BNB $630.3565
5.89% -
 Solana
Solana $129.2270
-0.57% -
 USDC
USDC $0.9999
0.00% -
 Dogecoin
Dogecoin $0.1729
3.03% -
 Cardano
Cardano $0.7248
2.38% -
 TRON
TRON $0.2147
0.42% -
 Pi
Pi $1.3661
-6.43% -
 Chainlink
Chainlink $13.8271
2.04% -
 UNUS SED LEO
UNUS SED LEO $9.8262
0.10% -
 Toncoin
Toncoin $3.4413
1.84% -
 Stellar
Stellar $0.2729
3.28% -
 Hedera
Hedera $0.1916
2.99% -
 Avalanche
Avalanche $18.6675
1.25% -
 Shiba Inu
Shiba Inu $0.0...01305
2.61% -
 Sui
Sui $2.2948
2.75% -
 Litecoin
Litecoin $93.2169
4.69% -
 Polkadot
Polkadot $4.3872
4.38% -
 MANTRA
MANTRA $6.8361
4.30% -
 Bitcoin Cash
Bitcoin Cash $337.3260
3.38% -
 Ethena USDe
Ethena USDe $0.9996
-0.01% -
 Dai
Dai $1.0000
-0.01% -
 Bitget Token
Bitget Token $4.4585
2.28% -
 Hyperliquid
Hyperliquid $13.8960
3.65% -
 Monero
Monero $211.2489
0.36% -
 Uniswap
Uniswap $6.2340
3.26% -
 Aptos
Aptos $5.3849
3.93%
How is the cross-chain bridge technology of AVAX implemented?
Avalanche's cross-chain bridges, built on its Subnet architecture, use multiple consensus mechanisms and layered security (multi-signature validation, secure smart contracts) for efficient and secure token transfers between various blockchains, including Ethereum.
Mar 14, 2025 at 11:10 pm

Key Points:
- Avalanche's cross-chain bridge technology leverages its unique Subnets architecture.
- It utilizes a combination of different consensus mechanisms for security and efficiency.
- Bridge security relies on multiple layers of validation and verification.
- Several different bridge types exist, catering to varied needs and security requirements.
- Understanding the intricacies of Avalanche's Subnets is crucial to grasping its cross-chain capabilities.
How is the cross-chain bridge technology of AVAX implemented?
Avalanche's cross-chain bridge technology is a sophisticated system built upon its innovative Subnet architecture. Unlike many blockchain networks that rely on a single, monolithic chain, Avalanche allows for the creation of independent, customizable Subnets. These Subnets can utilize various consensus mechanisms, enabling flexibility and scalability. This architecture is fundamental to its cross-chain capabilities, allowing for secure and efficient communication between different blockchains, including Ethereum, Polygon, and others.
The core of Avalanche's cross-chain bridging lies in its ability to connect these independent Subnets. A bridge isn't a single piece of code, but rather a system of smart contracts and validators operating across multiple Subnets. These contracts facilitate the transfer of tokens and data between the connected networks. The specific implementation varies depending on the Subnets involved and the type of bridge used.
Different Types of Avalanche Bridges
Avalanche offers several types of bridges, each designed for specific use cases and security requirements. Understanding these differences is key to comprehending the overall system.
- Subnet-to-Subnet Bridges: These are bridges connecting two or more Subnets within the Avalanche ecosystem. They often leverage Avalanche's native consensus mechanisms for speed and security. The transfer of assets within the Avalanche ecosystem generally uses this method and is typically very fast.
- External Bridges: These are bridges connecting Avalanche Subnets to external blockchains like Ethereum. These bridges are more complex, requiring additional security measures to safeguard against vulnerabilities. They typically involve locking tokens on one chain and minting equivalent tokens on another, with the reverse process for withdrawals. This is where the complexity of cross-chain communication really comes into play.
Security Mechanisms in Avalanche Cross-Chain Bridges
Security is paramount in any cross-chain bridge. Avalanche employs multiple layers of security to protect against attacks and ensure the integrity of transactions. These layers include:
- Multi-signature validation: Transactions are often validated by multiple validators, requiring consensus before being finalized. This helps prevent malicious actors from manipulating the system.
- Secure smart contracts: The smart contracts governing the bridging process are rigorously audited and designed to withstand various attack vectors. Regular updates and security patches are crucial.
- Reputation systems: Some bridges incorporate reputation systems to monitor the behavior of validators, penalizing those engaging in malicious activities. This helps maintain the overall security of the network.
- Wrapped Tokens: The use of wrapped tokens, such as wrapped ETH (wETH) on Avalanche, further enhances security by isolating the risk of the original asset's blockchain.
The Role of Validators in Avalanche's Cross-Chain Functionality
Validators play a crucial role in the security and efficiency of Avalanche's cross-chain bridges. They are responsible for verifying and validating transactions across different Subnets. The selection and operation of validators are critical to the overall system's performance and resilience. The more validators participating, generally the more secure and robust the bridge becomes. This decentralized approach is a key strength of the Avalanche network.
The Avalanche Subnet Architecture
Understanding the Avalanche Subnet architecture is crucial to grasping how cross-chain bridges function. Subnets are essentially independent blockchains that can be customized to suit specific needs. This allows for the creation of specialized networks optimized for particular applications. The ability to easily create and connect Subnets is what allows for the seamless integration of various blockchains into the Avalanche ecosystem. This flexibility is a significant advantage over more monolithic blockchain designs.
Detailed Look at the Bridging Process (Example: Ethereum to Avalanche)
Let's imagine transferring ETH to the Avalanche network. The process typically involves the following steps:
- Locking ETH: You initiate the transfer by locking your ETH on an Ethereum-based bridge contract.
- Minting AVAX-Wrapped ETH (wETH): Upon confirmation on Ethereum, an equivalent amount of wETH (a token representing your ETH) is minted on the Avalanche subnet.
- Receiving wETH: You then receive the wETH in your Avalanche wallet.
- Redeeming wETH: To return your ETH to the Ethereum network, you would reverse the process, burning wETH on Avalanche and unlocking your original ETH on Ethereum.
Frequently Asked Questions:
Q: What are the transaction fees for using Avalanche's cross-chain bridges?
A: Transaction fees vary depending on network congestion and the specific bridge used. They generally include gas fees on both the source and destination chains.
Q: How secure are Avalanche's cross-chain bridges?
A: Avalanche employs multiple security mechanisms, including multi-signature validation and secure smart contracts, to protect against attacks. However, no system is perfectly secure, and risks remain.
Q: What are the limitations of Avalanche's cross-chain technology?
A: While highly efficient, the complexity of the system can introduce potential vulnerabilities. Scalability can also become a concern during periods of high network activity.
Q: What blockchains does Avalanche bridge to?
A: Avalanche bridges to several prominent blockchains, including Ethereum, Polygon, and others. The supported blockchains are constantly expanding.
Q: Is bridging on Avalanche faster than other solutions?
A: Generally, yes. Avalanche's Subnet architecture and efficient consensus mechanisms often result in faster transaction times compared to other cross-chain solutions. However, this can vary based on network conditions.
Disclaimer:info@kdj.com
The information provided is not trading advice. kdj.com does not assume any responsibility for any investments made based on the information provided in this article. Cryptocurrencies are highly volatile and it is highly recommended that you invest with caution after thorough research!
If you believe that the content used on this website infringes your copyright, please contact us immediately (info@kdj.com) and we will delete it promptly.
- Why Is Coinbase a Good Business?
- 2025-03-17 20:25:57
- When it Comes to the Best Crypto to Invest in March 2025
- 2025-03-17 20:25:57
- Bitcoin Pepe (BPEP) Changes the Game With Technology That Could Transform Bitcoin Itself
- 2025-03-17 20:25:57
- XYZ Coin Crosses the $10 Million Mark in Its Presale Phase
- 2025-03-17 20:25:57
- Binance Expands Trade Offerings For MKR, EPIC, & These 3 Crypto
- 2025-03-17 20:25:57
- Arctic Pablo Coin ($APC) Presale: Explore the Depths of Cryptocurrency Investment
- 2025-03-17 20:25:57
Related knowledge

Which cryptocurrency websites are good for beginners?
Mar 14,2025 at 04:48pm
CoinbaseUser - friendly Interface: Coinbase offers a clean and intuitive interface that is easy for beginners to navigate. The platform is designed to be straightforward, with clear instructions for tasks like creating an account, depositing funds, and buying/selling cryptocurrencies. For example, when you log in, you are greeted with a dashboard that s...

How much will Bitcoin be worth in 2025
Mar 14,2025 at 04:23pm
Predicting the value of Bitcoin in 2025 is an extremely complex task. Bitcoin, as the pioneer of cryptocurrencies, has a price influenced by a vast array of factors, ranging from market dynamics and technological advancements to regulatory changes and global economic conditions.Market Supply and DemandLimited Supply: Bitcoin has a capped supply of 21 mi...

How to issue an ERC-20 token?
Mar 15,2025 at 04:20pm
Key Points:Understanding the prerequisites for ERC-20 token creation.Choosing the right development environment and tools.Writing the smart contract code.Compiling and deploying the smart contract to the Ethereum network.Testing the deployed token thoroughly.Listing the token on exchanges (optional).How to Issue an ERC-20 Token?Issuing an ERC-20 token i...

What are the core functions of the smart contract of ERC-20 tokens?
Mar 15,2025 at 11:10am
Key Points:ERC-20 smart contracts define the core functionality of a token, enabling transferability, balance tracking, and allowance for delegated transfers.Beyond basic token mechanics, smart contracts can incorporate features like burning, minting, and pausing token transactions.Advanced functionalities may include integration with other DeFi protoco...

What are the main functions of ERC-20 tokens?
Mar 13,2025 at 12:21am
Key Points:ERC-20 tokens are standardized tokens built on the Ethereum blockchain, enabling interoperability and ease of use.Their primary function is to represent fungible assets, meaning each token is interchangeable with any other of the same type.ERC-20 tokens facilitate various use cases, including fundraising (ICOs/IEOs), representing in-game asse...

How are ERC-20 tokens created on the Ethereum blockchain?
Mar 13,2025 at 01:30pm
Key Points:ERC-20 tokens are created by deploying a smart contract to the Ethereum blockchain.This smart contract defines the token's properties, such as name, symbol, total supply, and decimals.Several tools and platforms simplify the process, including online IDEs and dedicated token creation services.Understanding Solidity programming is crucial for ...

Which cryptocurrency websites are good for beginners?
Mar 14,2025 at 04:48pm
CoinbaseUser - friendly Interface: Coinbase offers a clean and intuitive interface that is easy for beginners to navigate. The platform is designed to be straightforward, with clear instructions for tasks like creating an account, depositing funds, and buying/selling cryptocurrencies. For example, when you log in, you are greeted with a dashboard that s...

How much will Bitcoin be worth in 2025
Mar 14,2025 at 04:23pm
Predicting the value of Bitcoin in 2025 is an extremely complex task. Bitcoin, as the pioneer of cryptocurrencies, has a price influenced by a vast array of factors, ranging from market dynamics and technological advancements to regulatory changes and global economic conditions.Market Supply and DemandLimited Supply: Bitcoin has a capped supply of 21 mi...

How to issue an ERC-20 token?
Mar 15,2025 at 04:20pm
Key Points:Understanding the prerequisites for ERC-20 token creation.Choosing the right development environment and tools.Writing the smart contract code.Compiling and deploying the smart contract to the Ethereum network.Testing the deployed token thoroughly.Listing the token on exchanges (optional).How to Issue an ERC-20 Token?Issuing an ERC-20 token i...

What are the core functions of the smart contract of ERC-20 tokens?
Mar 15,2025 at 11:10am
Key Points:ERC-20 smart contracts define the core functionality of a token, enabling transferability, balance tracking, and allowance for delegated transfers.Beyond basic token mechanics, smart contracts can incorporate features like burning, minting, and pausing token transactions.Advanced functionalities may include integration with other DeFi protoco...

What are the main functions of ERC-20 tokens?
Mar 13,2025 at 12:21am
Key Points:ERC-20 tokens are standardized tokens built on the Ethereum blockchain, enabling interoperability and ease of use.Their primary function is to represent fungible assets, meaning each token is interchangeable with any other of the same type.ERC-20 tokens facilitate various use cases, including fundraising (ICOs/IEOs), representing in-game asse...

How are ERC-20 tokens created on the Ethereum blockchain?
Mar 13,2025 at 01:30pm
Key Points:ERC-20 tokens are created by deploying a smart contract to the Ethereum blockchain.This smart contract defines the token's properties, such as name, symbol, total supply, and decimals.Several tools and platforms simplify the process, including online IDEs and dedicated token creation services.Understanding Solidity programming is crucial for ...
See all articles