-
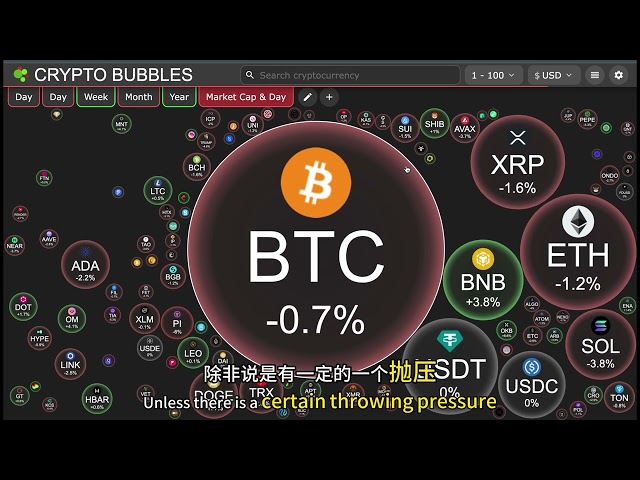
 Bitcoin
Bitcoin $83,405.1468
1.08% -
 Ethereum
Ethereum $1,912.6728
1.88% -
 Tether USDt
Tether USDt $0.9998
-0.02% -
 XRP
XRP $2.3402
1.69% -
 BNB
BNB $630.3565
5.89% -
 Solana
Solana $129.2270
-0.57% -
 USDC
USDC $0.9999
0.00% -
 Dogecoin
Dogecoin $0.1729
3.03% -
 Cardano
Cardano $0.7248
2.38% -
 TRON
TRON $0.2147
0.42% -
 Pi
Pi $1.3661
-6.43% -
 Chainlink
Chainlink $13.8271
2.04% -
 UNUS SED LEO
UNUS SED LEO $9.8262
0.10% -
 Toncoin
Toncoin $3.4413
1.84% -
 Stellar
Stellar $0.2729
3.28% -
 Hedera
Hedera $0.1916
2.99% -
 Avalanche
Avalanche $18.6675
1.25% -
 Shiba Inu
Shiba Inu $0.0...01305
2.61% -
 Sui
Sui $2.2948
2.75% -
 Litecoin
Litecoin $93.2169
4.69% -
 Polkadot
Polkadot $4.3872
4.38% -
 MANTRA
MANTRA $6.8361
4.30% -
 Bitcoin Cash
Bitcoin Cash $337.3260
3.38% -
 Ethena USDe
Ethena USDe $0.9996
-0.01% -
 Dai
Dai $1.0000
-0.01% -
 Bitget Token
Bitget Token $4.4585
2.28% -
 Hyperliquid
Hyperliquid $13.8960
3.65% -
 Monero
Monero $211.2489
0.36% -
 Uniswap
Uniswap $6.2340
3.26% -
 Aptos
Aptos $5.3849
3.93%
how that protects users funds?
Reputable cryptocurrency exchanges prioritize user fund security by implementing rigorous measures such as two-factor authentication, cold storage, third-party audits, insurance policies, and blockchain technology.
Feb 11, 2025 at 07:30 am

Cryptocurrency Exchanges: Protecting Users' Funds
Introduction
Cryptocurrency exchanges play a crucial role in the cryptocurrency ecosystem, facilitating the buying, selling, and trading of digital assets. However, with the rise of hacks and security breaches, protecting users' funds has become paramount. This article delves into the key steps and measures employed by reputable exchanges to ensure the security and integrity of their platforms.
Key Points
- Strong Security Infrastructure: Implement robust security measures such as two-factor authentication (2FA), multi-factor authentication (MFA), and advanced encryption protocols to protect users' accounts and sensitive information from unauthorized access.
- Cold Storage: Store the majority of user funds offline in cold storage devices, which are isolated from the internet, eliminating the risk of online attacks.
- Third-Party Audits and Certifications: Engage with independent third-party auditors to conduct regular security assessments and verify compliance with industry standards and best practices.
- Insurance Policies: Secure insurance policies to provide financial protection in the event of a security incident or loss of funds due to hacking or theft.
- Know Your Customer (KYC) and Anti-Money Laundering (AML) Compliance: Implement stringent KYC and AML procedures to prevent fraudulent activities, money laundering, and illicit transactions.
- Blockchain Technology Utilization: Leverage advanced blockchain technology to facilitate secure and transparent transactions, providing users with immutable records of their activities.
- User Education and Awareness: Provide clear and accessible resources to educate users on best security practices and potential risks associated with cryptocurrency investments.
Step-by-Step Guide to Protecting User Funds
1. Establish Robust Security Infrastructure
Implement advanced security measures such as:
- Two-Factor Authentication (2FA): Requires users to provide two forms of identification when logging in, such as a password and a code sent to their mobile device.
- Multi-Factor Authentication (MFA): Extends 2FA by requiring additional factors, such as a fingerprint scan or a hardware token.
- Encrypted Communication Channels: Uses SSL/TLS protocols to encrypt all communication between users and the exchange's servers, protecting sensitive data from interception.
2. Secure Cold Storage Implementation
- Store the majority of user funds in cold storage devices, such as hardware wallets or offline storage devices that are not connected to the internet.
- Establish strict protocols for accessing cold storage devices, limiting access to authorized personnel only.
- Regularly rotate cold storage keys and wallets to mitigate the risk of compromise.
3. Engage Third-Party Auditors and Certifications
- Hire reputable third-party auditors to conduct regular security assessments of the exchange's infrastructure and processes.
- Obtain industry certifications, such as ISO 27001 or SOC 2, which demonstrate compliance with best practices and regulatory standards.
- Publish audit reports and certification results transparently on the exchange's website.
4. Secure Adequate Insurance Policies
- Purchase insurance policies that cover potential losses or liabilities resulting from hacking, theft, or fraud.
- Ensure that the insurance coverage is comprehensive and adequate to protect users' funds.
- Regularly review and update insurance policies as the exchange's operations evolve.
5. Implement KYC and AML Compliance
- Conduct thorough KYC procedures to verify the identities of users and prevent fraudulent activities.
- Implement AML monitoring systems to detect and flag suspicious transactions or accounts associated with money laundering.
- Comply with applicable regulations and industry guidelines to maintain compliance and protect user funds.
6. Leverage Blockchain Technology
- Utilize blockchain technology to facilitate secure and transparent transactions.
- Implement smart contracts to automate processes and reduce the risk of human error or fraud.
- Provide users with blockchain-based proof of ownership and transaction records.
7. Provide User Education and Awareness
- Develop comprehensive educational resources to inform users about best security practices and potential risks associated with cryptocurrency investments.
- Organize educational webinars, tutorials, and online materials to enhance user knowledge and awareness.
- Establish a support system to assist users with security-related questions and concerns.
FAQs
Q: What are the best exchanges for secure cryptocurrency storage?
A: While excluding FTX, reputable exchanges known for their robust security practices include:
- Coinbase
- Binance
- Kraken
- Gemini
- Bitstamp
Q: How can I protect my cryptocurrency from hacks and theft?
A: Implement good security practices such as:
- Using strong passwords and enabling 2FA
- Storing your cryptocurrency in a hardware wallet
- Being cautious of phishing scams and social engineering attacks
- Staying informed about security vulnerabilities and updates
Q: What happens if an exchange is hacked?
A: In the event of a hack, the exchange's insurance policy may cover the lost or stolen funds, depending on the terms and conditions of the policy. However, it is crucial to note that insurance coverage may vary, and users should carefully review the terms of their exchange's policy.
Disclaimer:info@kdj.com
The information provided is not trading advice. kdj.com does not assume any responsibility for any investments made based on the information provided in this article. Cryptocurrencies are highly volatile and it is highly recommended that you invest with caution after thorough research!
If you believe that the content used on this website infringes your copyright, please contact us immediately (info@kdj.com) and we will delete it promptly.
- Why Is Coinbase a Good Business?
- 2025-03-17 20:25:57
- When it Comes to the Best Crypto to Invest in March 2025
- 2025-03-17 20:25:57
- Bitcoin Pepe (BPEP) Changes the Game With Technology That Could Transform Bitcoin Itself
- 2025-03-17 20:25:57
- XYZ Coin Crosses the $10 Million Mark in Its Presale Phase
- 2025-03-17 20:25:57
- Binance Expands Trade Offerings For MKR, EPIC, & These 3 Crypto
- 2025-03-17 20:25:57
- Arctic Pablo Coin ($APC) Presale: Explore the Depths of Cryptocurrency Investment
- 2025-03-17 20:25:57
Related knowledge

What is Ethereum’s Slashing mechanism and how to punish malicious behavior?
Feb 20,2025 at 03:08am
Key PointsOverview of slashingDifferent types of slashing in EthereumIncentives and consequences of slashingIdentifying and reporting slashed validatorsOngoing discussions and potential improvementsEthereum's Slashing Mechanism: Punishing Malicious BehaviorEthereum's slashing mechanism is an essential tool for ensuring network security and punishing mal...

What is the verifier node of Ethereum and how to become a verifier?
Feb 19,2025 at 06:00pm
The Verifier Node of Ethereum: A Comprehensive GuideKey Points:What is a Verifier Node?How to Become a Verifier NodeResponsibilities and Rewards of a Verifier NodeMinimum Requirements for Becoming a Verifier NodePotential Difficulties in Running a Verifier Node1. What is a Verifier Node?A Verifier Node is an independent entity on the Ethereum network th...

What is Ethereum’s staking, and how to participate and earn money?
Feb 19,2025 at 04:37pm
Key Points:Understanding Ethereum's Staking MechanismSteps to Participate in StakingBenefits and Rewards of StakingSecurity and Risk ConsiderationsTechnical Requirements and Hardware OptionsPotential Challenges and Troubleshooting TipsFAQs on Ethereum StakingWhat is Ethereum's Staking?Proof-of-Stake (PoS) is a consensus mechanism used in blockchain netw...

What is Ethereum’s DAO (Decentralized Autonomous Organization) and how does it work?
Feb 20,2025 at 03:12am
Key PointsDefinition and Structure of a DAOGovernance and Decision-Making in DAOsBenefits and Use Cases of DAOsChallenges and Limitations of DAOsWhat is Ethereum's DAO (Decentralized Autonomous Organization) and How Does It Work?Definition and Structure of a DAOA Decentralized Autonomous Organization (DAO) is an innovative governance and management fram...

What is Ethereum's multi-signature wallet and how to improve security?
Feb 20,2025 at 02:18pm
Key Points:Understanding the Concept of a Multi-Signature WalletBenefits and Drawbacks of Multisig WalletsRequirements for Setting Up a Multisig WalletStep-by-Step Guide to Generating a Multisig WalletImplementing Strategies for Enhanced Security1. Understanding the Concept of a Multi-Signature WalletA multi-signature (multisig) wallet in the Ethereum e...

What is Ethereum's oracle and how to provide data for smart contracts?
Feb 21,2025 at 01:30am
Key Points:Understanding the concept of oracles in EthereumExploring different types of oraclesDetailed guide on how to provide data for smart contractsAddressing potential challenges and considerationsWhat is Ethereum's Oracle?Oracles are crucial components in the Ethereum ecosystem, enabling smart contracts to access real-world data and off-chain even...

What is Ethereum’s Slashing mechanism and how to punish malicious behavior?
Feb 20,2025 at 03:08am
Key PointsOverview of slashingDifferent types of slashing in EthereumIncentives and consequences of slashingIdentifying and reporting slashed validatorsOngoing discussions and potential improvementsEthereum's Slashing Mechanism: Punishing Malicious BehaviorEthereum's slashing mechanism is an essential tool for ensuring network security and punishing mal...

What is the verifier node of Ethereum and how to become a verifier?
Feb 19,2025 at 06:00pm
The Verifier Node of Ethereum: A Comprehensive GuideKey Points:What is a Verifier Node?How to Become a Verifier NodeResponsibilities and Rewards of a Verifier NodeMinimum Requirements for Becoming a Verifier NodePotential Difficulties in Running a Verifier Node1. What is a Verifier Node?A Verifier Node is an independent entity on the Ethereum network th...

What is Ethereum’s staking, and how to participate and earn money?
Feb 19,2025 at 04:37pm
Key Points:Understanding Ethereum's Staking MechanismSteps to Participate in StakingBenefits and Rewards of StakingSecurity and Risk ConsiderationsTechnical Requirements and Hardware OptionsPotential Challenges and Troubleshooting TipsFAQs on Ethereum StakingWhat is Ethereum's Staking?Proof-of-Stake (PoS) is a consensus mechanism used in blockchain netw...

What is Ethereum’s DAO (Decentralized Autonomous Organization) and how does it work?
Feb 20,2025 at 03:12am
Key PointsDefinition and Structure of a DAOGovernance and Decision-Making in DAOsBenefits and Use Cases of DAOsChallenges and Limitations of DAOsWhat is Ethereum's DAO (Decentralized Autonomous Organization) and How Does It Work?Definition and Structure of a DAOA Decentralized Autonomous Organization (DAO) is an innovative governance and management fram...

What is Ethereum's multi-signature wallet and how to improve security?
Feb 20,2025 at 02:18pm
Key Points:Understanding the Concept of a Multi-Signature WalletBenefits and Drawbacks of Multisig WalletsRequirements for Setting Up a Multisig WalletStep-by-Step Guide to Generating a Multisig WalletImplementing Strategies for Enhanced Security1. Understanding the Concept of a Multi-Signature WalletA multi-signature (multisig) wallet in the Ethereum e...

What is Ethereum's oracle and how to provide data for smart contracts?
Feb 21,2025 at 01:30am
Key Points:Understanding the concept of oracles in EthereumExploring different types of oraclesDetailed guide on how to provide data for smart contractsAddressing potential challenges and considerationsWhat is Ethereum's Oracle?Oracles are crucial components in the Ethereum ecosystem, enabling smart contracts to access real-world data and off-chain even...
See all articles