-
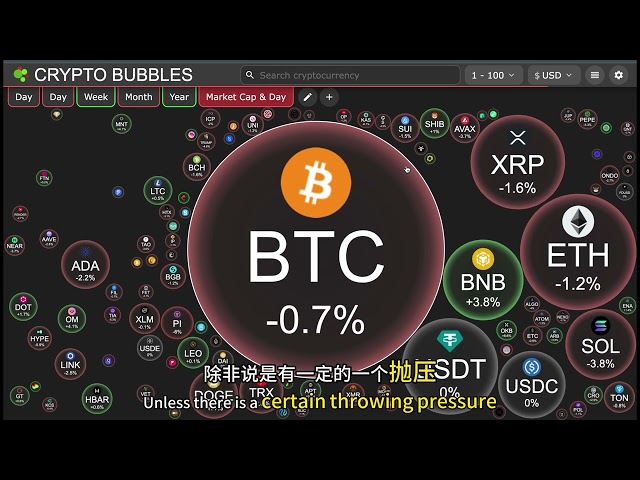
 Bitcoin
Bitcoin $83,580.1551
0.17% -
 Ethereum
Ethereum $1,919.8787
1.25% -
 Tether USDt
Tether USDt $0.9998
-0.02% -
 XRP
XRP $2.3457
1.96% -
 BNB
BNB $630.2576
4.80% -
 Solana
Solana $127.3404
-1.19% -
 USDC
USDC $0.9998
-0.01% -
 Dogecoin
Dogecoin $0.1723
2.18% -
 Cardano
Cardano $0.7233
2.69% -
 TRON
TRON $0.2191
1.67% -
 Pi
Pi $1.3203
-5.53% -
 UNUS SED LEO
UNUS SED LEO $9.8267
2.11% -
 Chainlink
Chainlink $13.7576
1.96% -
 Toncoin
Toncoin $3.4760
1.88% -
 Stellar
Stellar $0.2745
3.69% -
 Hedera
Hedera $0.1924
2.86% -
 Avalanche
Avalanche $18.4804
-0.08% -
 Shiba Inu
Shiba Inu $0.0...01290
-2.12% -
 Sui
Sui $2.3260
3.69% -
 Litecoin
Litecoin $93.4261
4.62% -
 MANTRA
MANTRA $6.9340
2.94% -
 Polkadot
Polkadot $4.3747
3.09% -
 Bitcoin Cash
Bitcoin Cash $339.4677
2.91% -
 Ethena USDe
Ethena USDe $0.9997
-0.01% -
 Dai
Dai $1.0001
-0.01% -
 Bitget Token
Bitget Token $4.4397
1.21% -
 Hyperliquid
Hyperliquid $13.7253
2.64% -
 Monero
Monero $212.5077
0.92% -
 Uniswap
Uniswap $6.2006
2.51% -
 Aptos
Aptos $5.3861
3.98%
An article explains the concept, common algorithms, principles and applications of hash values
Hashing algorithms, such as SHA-256, act as one-directional encryption functions, making it computationally infeasible to derive the original input from the resulting hash value.
Feb 08, 2025 at 05:31 pm

Understanding the Role of Hash Values in the Cryptocurrency Realm
Key Points
- Hash Function Principles and Algorithms
- Characteristics and Applications of Hash Values
- Secure Hash Algorithms: Non-Invertible Encryption
- Practical Cryptography Applications of Hashing
- Industry Use Cases and Standards
- Multi-Platform Compatibility and Interoperability
- Decentralized Ledger Security and Validation
- Privacy and Anonymity Through Hashing
- Future Trends and Innovations in Hashing
Hash Function Principles and Algorithms
Hash functions are mathematical transformations that map a digital input of arbitrary size to a fixed-size hash value. They are designed to be effective for efficiently verifying the integrity and authenticity of data. Common algorithms include:
- MD5 (Message Digest 5): A widely used algorithm but susceptible to collision attacks.
- SHA-2 (Secure Hash Algorithm-2): A set of algorithms (e.g., SHA-256, SHA-512) with enhanced security features.
- RIPEMD-160 (RACE Integrity Primitives Evaluation Message Digest): A secure and collision-resistant algorithm often used in cryptocurrencies.
Characteristics and Applications of Hash Values
Hash values are unique representations of data, with key characteristics such as:
- Deterministic: The same input always produces the same hash value.
- One-Way: It is computationally infeasible to derive the input from a given hash value.
- Collision Resistance: It is difficult to find two inputs that produce the same hash value.
Hash values are crucial in applications like:
- Password security: Storing hashed passwords prevents plaintext exposure.
- Data integrity verification: Detecting unauthorized data modifications.
- Digital signatures: Providing proof of origin and authenticity of digital documents.
Secure Hash Algorithms: Non-Invertible Encryption
Secure hash algorithms, such as SHA-2 and RIPEMD-160, are widely used in cryptography due to their non-invertible nature. They act as one-directional functions, where the original input cannot be retrieved from the hash value. This property is essential for:
- Preventing Password Cracking: Hashing passwords makes them resistant to brute-force attacks.
- Authenticating Digital Currency Transactions: Hashing ensures the integrity and authenticity of crypto transactions, preventing tampering.
- Securing Blockchains: Hashing forms the backbone of blockchain technology, validating blocks and maintaining the integrity of the ledger.
Practical Cryptography Applications of Hashing
Hashing has numerous applications in cryptography, including:
- Digital Signatures: Creating a unique digital fingerprint that verifies the sender and data integrity.
- Message Authentication Codes (MACs): Generating keys derived from a hash function to ensure message authenticity and prevent tampering.
- Key Derivation Functions (KDFs): Deriving encryption keys from a shared secret or password using a hash function.
- Password-Based Encryption (PBE): Using a hash function to securely store and authenticate user passwords.
Industry Use Cases and Standards
Various industries rely on hashing for security and data integrity, including:
- Financial Services: Hashing is used in payment systems, KYC (Know-Your-Customer) processes, and anti-fraud measures.
- Healthcare: Hashing protects patient data, medical records, and prescription authenticity.
- E-Commerce: Hashing secures online transactions, validates digital receipts, and prevents product counterfeiting.
- Government and Legal: Hashing is employed in digital signatures, document validation, and fraud detection in the legal system.
Multi-Platform Compatibility and Interoperability
Hash functions are designed to be compatible across different platforms and operating systems. This ensures interoperability and data exchange without compromising security. Standardized protocols and libraries, such as HMAC (Hash-based Message Authentication Code), facilitate secure hashing across various platforms.
Decentralized Ledger Security and Validation
Hashing is fundamental to decentralized ledger technologies like blockchain. It provides the following security and validation functions:
- Block Validation: Each block in a blockchain contains a hash of the previous block, creating an immutable chain.
- Transaction Verification: Transactions are hashed and included in blocks, verifying their authenticity and preventing double-spending.
- Consensus Algorithms: Hashing plays a role in consensus algorithms, ensuring agreement on the state of the blockchain.
Privacy and Anonymity Through Hashing
Hashing techniques can enhance privacy and anonymity in cryptocurrency transactions:
- Anonymity: Hashing public keys linked to cryptocurrency addresses can provide a level of anonymity.
- Privacy: Hashing transaction details can obscure transaction specifics while preserving traceability for accounting purposes.
- Zero-Knowledge Proofs: Hashing is used in zero-knowledge proofs, a technique to prove a statement without revealing the underlying information.
Future Trends and Innovations in Hashing
Ongoing research and innovation in hashing technology aim to improve security, efficiency, and scalability:
- Quantum-Resistant Hashing: Exploring algorithms resistant to quantum attacks, mitigating future security risks.
- Collision-Resistant Hashing: Developing algorithms that are highly resistant to hash collision attacks.
- Scalable Hashing: Designing algorithms that can handle high transaction volumes without compromising security.
- Post-Quantum Cryptography: Investigating hash functions and algorithms that are secure against quantum computing attacks.
- Blockchain Interoperability: Developing hashing techniques that facilitate interoperability between different blockchain platforms.
FAQs
- What is a hash value?
A unique digital fingerprint of data generated by a hash function, representing the data securely and efficiently. - Why are hash values important?
They provide data integrity verification, prevent tampering, and enable digital signatures, password security, and cryptography applications. - What are the most common hash algorithms?
MD5, SHA-2 (SHA-256, SHA-512), and RIPEMD-160 are widely used hash algorithms. - How are hash values used in cryptocurrency?
Hashing ensures transaction authenticity, prevents double-spending, and provides anonymity and privacy in some cases. - What are the emerging trends in hashing technology?
Quantum-resistant hashing, collision-resistant hashing, and scalable hashing are areas of active research and innovation.
Disclaimer:info@kdj.com
The information provided is not trading advice. kdj.com does not assume any responsibility for any investments made based on the information provided in this article. Cryptocurrencies are highly volatile and it is highly recommended that you invest with caution after thorough research!
If you believe that the content used on this website infringes your copyright, please contact us immediately (info@kdj.com) and we will delete it promptly.
- Pepe (PEPE) Has Emerged as One of the Top-Performing Meme Coins in the Market
- 2025-03-18 00:30:58
- Dawgz AI (DAGZ) Price Prediction Shows Explosive Growth Potential as Investors Recognize Its Unique Positioning
- 2025-03-18 00:30:58
- Rexas Finance (RXS) May Outperform Pepe Coin (PEPE) This Cycle
- 2025-03-18 00:26:54
- Three Altcoins to Watch as the Crypto Market Awaits a Recovery Rally
- 2025-03-18 00:26:54
- Bitcoin (BTC) Price Prediction: Will BTC Hold Above the $81,400 Support Level?
- 2025-03-18 00:26:54
- Smart Money Investors Have Sold Some Popular Cryptocurrencies During the Ongoing Crypto Bear Market
- 2025-03-18 00:26:54
Related knowledge

What is Ethereum’s Slashing mechanism and how to punish malicious behavior?
Feb 20,2025 at 03:08am
Key PointsOverview of slashingDifferent types of slashing in EthereumIncentives and consequences of slashingIdentifying and reporting slashed validatorsOngoing discussions and potential improvementsEthereum's Slashing Mechanism: Punishing Malicious BehaviorEthereum's slashing mechanism is an essential tool for ensuring network security and punishing mal...

What is the verifier node of Ethereum and how to become a verifier?
Feb 19,2025 at 06:00pm
The Verifier Node of Ethereum: A Comprehensive GuideKey Points:What is a Verifier Node?How to Become a Verifier NodeResponsibilities and Rewards of a Verifier NodeMinimum Requirements for Becoming a Verifier NodePotential Difficulties in Running a Verifier Node1. What is a Verifier Node?A Verifier Node is an independent entity on the Ethereum network th...

What is Ethereum’s staking, and how to participate and earn money?
Feb 19,2025 at 04:37pm
Key Points:Understanding Ethereum's Staking MechanismSteps to Participate in StakingBenefits and Rewards of StakingSecurity and Risk ConsiderationsTechnical Requirements and Hardware OptionsPotential Challenges and Troubleshooting TipsFAQs on Ethereum StakingWhat is Ethereum's Staking?Proof-of-Stake (PoS) is a consensus mechanism used in blockchain netw...

What is Ethereum’s DAO (Decentralized Autonomous Organization) and how does it work?
Feb 20,2025 at 03:12am
Key PointsDefinition and Structure of a DAOGovernance and Decision-Making in DAOsBenefits and Use Cases of DAOsChallenges and Limitations of DAOsWhat is Ethereum's DAO (Decentralized Autonomous Organization) and How Does It Work?Definition and Structure of a DAOA Decentralized Autonomous Organization (DAO) is an innovative governance and management fram...

What is Ethereum's multi-signature wallet and how to improve security?
Feb 20,2025 at 02:18pm
Key Points:Understanding the Concept of a Multi-Signature WalletBenefits and Drawbacks of Multisig WalletsRequirements for Setting Up a Multisig WalletStep-by-Step Guide to Generating a Multisig WalletImplementing Strategies for Enhanced Security1. Understanding the Concept of a Multi-Signature WalletA multi-signature (multisig) wallet in the Ethereum e...

What is Ethereum's oracle and how to provide data for smart contracts?
Feb 21,2025 at 01:30am
Key Points:Understanding the concept of oracles in EthereumExploring different types of oraclesDetailed guide on how to provide data for smart contractsAddressing potential challenges and considerationsWhat is Ethereum's Oracle?Oracles are crucial components in the Ethereum ecosystem, enabling smart contracts to access real-world data and off-chain even...

What is Ethereum’s Slashing mechanism and how to punish malicious behavior?
Feb 20,2025 at 03:08am
Key PointsOverview of slashingDifferent types of slashing in EthereumIncentives and consequences of slashingIdentifying and reporting slashed validatorsOngoing discussions and potential improvementsEthereum's Slashing Mechanism: Punishing Malicious BehaviorEthereum's slashing mechanism is an essential tool for ensuring network security and punishing mal...

What is the verifier node of Ethereum and how to become a verifier?
Feb 19,2025 at 06:00pm
The Verifier Node of Ethereum: A Comprehensive GuideKey Points:What is a Verifier Node?How to Become a Verifier NodeResponsibilities and Rewards of a Verifier NodeMinimum Requirements for Becoming a Verifier NodePotential Difficulties in Running a Verifier Node1. What is a Verifier Node?A Verifier Node is an independent entity on the Ethereum network th...

What is Ethereum’s staking, and how to participate and earn money?
Feb 19,2025 at 04:37pm
Key Points:Understanding Ethereum's Staking MechanismSteps to Participate in StakingBenefits and Rewards of StakingSecurity and Risk ConsiderationsTechnical Requirements and Hardware OptionsPotential Challenges and Troubleshooting TipsFAQs on Ethereum StakingWhat is Ethereum's Staking?Proof-of-Stake (PoS) is a consensus mechanism used in blockchain netw...

What is Ethereum’s DAO (Decentralized Autonomous Organization) and how does it work?
Feb 20,2025 at 03:12am
Key PointsDefinition and Structure of a DAOGovernance and Decision-Making in DAOsBenefits and Use Cases of DAOsChallenges and Limitations of DAOsWhat is Ethereum's DAO (Decentralized Autonomous Organization) and How Does It Work?Definition and Structure of a DAOA Decentralized Autonomous Organization (DAO) is an innovative governance and management fram...

What is Ethereum's multi-signature wallet and how to improve security?
Feb 20,2025 at 02:18pm
Key Points:Understanding the Concept of a Multi-Signature WalletBenefits and Drawbacks of Multisig WalletsRequirements for Setting Up a Multisig WalletStep-by-Step Guide to Generating a Multisig WalletImplementing Strategies for Enhanced Security1. Understanding the Concept of a Multi-Signature WalletA multi-signature (multisig) wallet in the Ethereum e...

What is Ethereum's oracle and how to provide data for smart contracts?
Feb 21,2025 at 01:30am
Key Points:Understanding the concept of oracles in EthereumExploring different types of oraclesDetailed guide on how to provide data for smart contractsAddressing potential challenges and considerationsWhat is Ethereum's Oracle?Oracles are crucial components in the Ethereum ecosystem, enabling smart contracts to access real-world data and off-chain even...
See all articles